This month, SC Labs revisited the vulnerability management space and reviewed a handful of solutions. Vulnerability management tools have become an important aspect of the security process. Through scanning an environment and penetration testing, they reveal where vulnerabilities exist and what could potentially be the results of their exploitation. Having one of these products in your arsenal will aid in eliminating blind spots and ensuring other security measures are adequately configured to provide the protection you expect.

As are many cybersecurity products, some of these tools are incorporating machine learning in the form of predictive modeling to give visibility into vulnerabilities that not only have known and unknown threats and exploitations, but also vulnerabilities with no currently known exploitations.
Vulnerability management tools also take into consideration specific business practices and security needs. They score vulnerabilities based on threat intelligence and other data leveraged from outside of the client realm. These vulnerability risk scores are analyzed further and bolstered with data in the form of asset weights so you can be sure the information you are receiving is based on your specific organization and not a generalized, umbrella security report.
With the rapid advancements and breakneck pace for all things cybersecurity, vulnerability management tools are becoming all the more necessary to stay ahead of ever-changing threats as is making sure your other security tools are adequately configured and functioning. The cost of adding these tools is worth the peace of mind knowing your security posture is not hiding any sinister, exploitable vulnerabilities and that you know exactly where your blind spots are.
Product Group Opener
Vulnerability management tools are an often-overlooked basics in an organization’s security posture. The main takeaway after reviewing this month’s set of products is that the most effective way to ensure your organization is putting the focus where it is needed to keep up with an expanding and changing threat landscape is to implement a vulnerability management program. A well-run program will bring critical issues to your attention and give you an idea of the type of remediation that will have the most impact.
These tools take a lot of the guesswork out of the process. While spotting a vulnerability is easy after a breach, given the expansiveness of today’s threats, organizations need to know about potentially exploitable vulnerabilities before an incident occurs. These vulnerability management tools help you determine whether you need role-based access, agent-based scanning options or remediation assistance for quick patching while also highlighting any compliance or regulatory requirements that aren’t met.
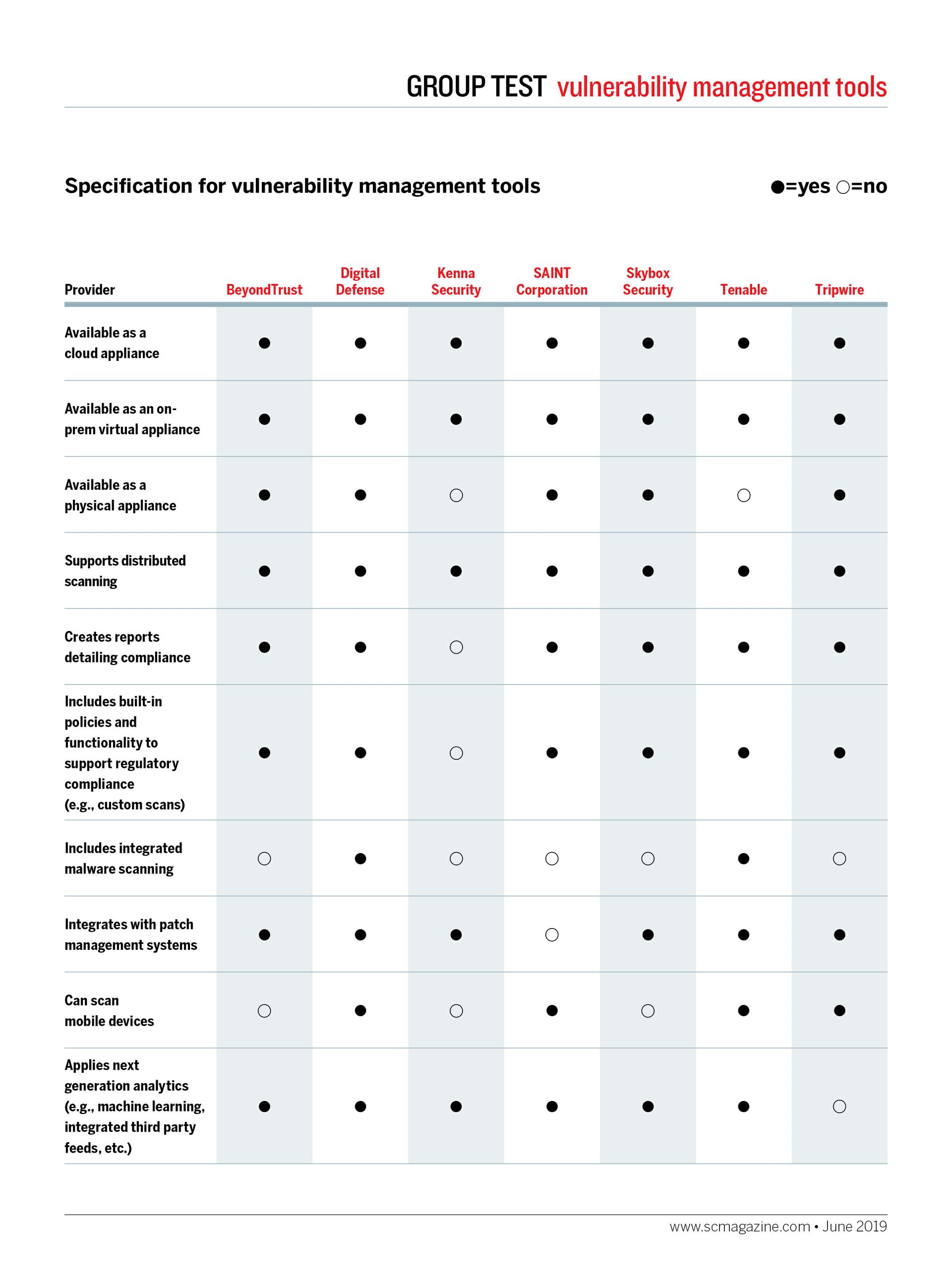
The typical network design has changed over the years and vulnerability management tools have been able to keep pace. They include compliance reporting, cloud scanning, remote scanners, machine learning predictive algorithms and agent-based tools to help protect an organization from zero-day attacks as well as keep up with the known and unknown threats.
With exploits growing in sophistication and reachability, we were happy to see many products moving toward encompassing artificial intelligence and machine learning algorithms that can predict where an organization is vulnerable and eliminate blind spots while heavily ensuring scalability for all environments. Many of the products we looked at also support a fair level of customizability, so vulnerability ratings are weighted to an organization’s assets and business practices to ensure protection where it matters most. Just as with last year’s vulnerability management solutions API integration is the growing and nearly consistent among the tools reviewed.
As we’ve noted, vulnerability management should be a significant part of your organization’s security program. You cannot protect your assets if you are unaware of your vulnerabilities and where they are. Security measures put in place are worth nothing if they are put where your weaknesses are. Vulnerability management tools serve to complement the measures you already have in place by ensuring they are working as desired and adequately configured to cover you where you are vulnerable. You should be able to kickoff scans/tests from other tools and ingest the results into your ticketing system or other important toolsets.
While scanning is never enough, by starting with the knowledge of where your vulnerabilities exist, you can begin to understand the potential implications of those vulnerabilities should they be exploited. We always recommend conducting independent security testing (e.g. penetration testing) on your environment. However, some of the tools we reviewed here have some testing capabilities that are as good (if not better) than some automatic tests that are out there, including a quick and easy way to export the data into an easily digestible report. Many reports are customizable to create vulnerability views to meet the criteria of anyone and everyone. Some products include a seamless transition between vulnerability data, the resulting report and suggested fixes for those vulnerabilities to ensure you get the most out of security measures at the least manual work cost. They takes the guesswork and overhead out of remediation and expedite the process so you can eliminate as many vulnerabilities in your environment as quickly as possible.
Overall, these tools seemingly are advancing and adapting with the security landscape effortlessly. They help to harden an organization’s security posture with penetration testing, scheduled and automated scans, and digestible reports – in some cases, even taking vulnerability management further into the realm of prediction with or without the existence of known and unknown exploits. And that promises to put you a step ahead of risk.
Pick of the Litter
BeyondTrust Enterprise Vulnerability Management is SC Labs Best Buy for combining its modular price structure that can be tailored to any size environment with an optional hardware appliance also offered at a competitive price.
SAINT Security Suite has grown into a feature-rich product over the past year, including new practical integrations and a more than reasonable price point. For that, SAINT Security Suite takes the SC Labs Recommended product of the month spot.
Pick of the Litter by Matthew Hreben
June 2019 products reviews
BeyondTrust – Enterprise Vulnerability Management
Digital Defense Frontline – Vulnerability Manager 6.2
Kenna – Kenna Security Platform
SAINT – Security Suite 9.5
Skybox Security – Security Suite, Vulnerability and Threat Management
Tenable – Tenable.io
Tripwire – IP360 9.0.3