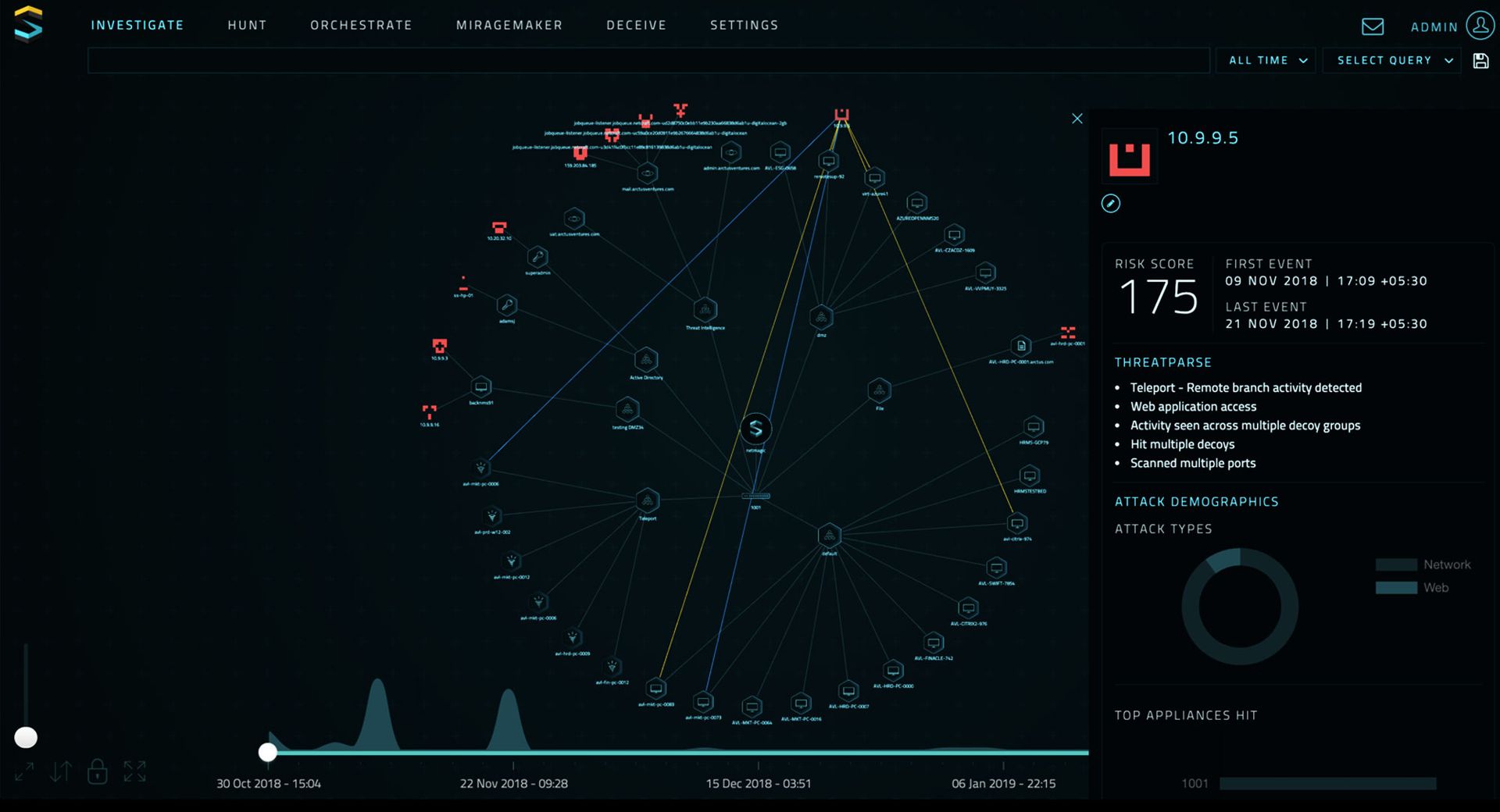
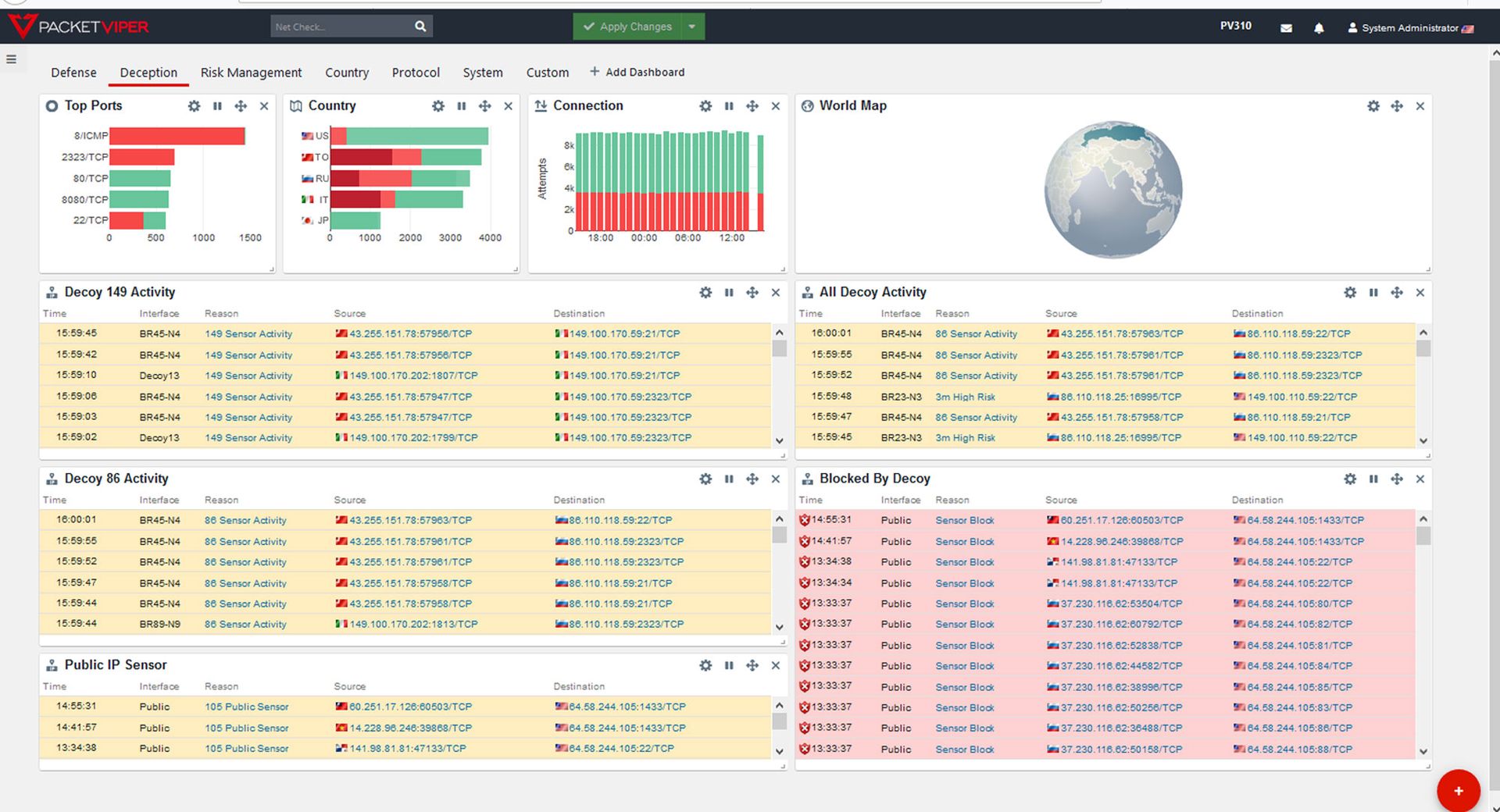
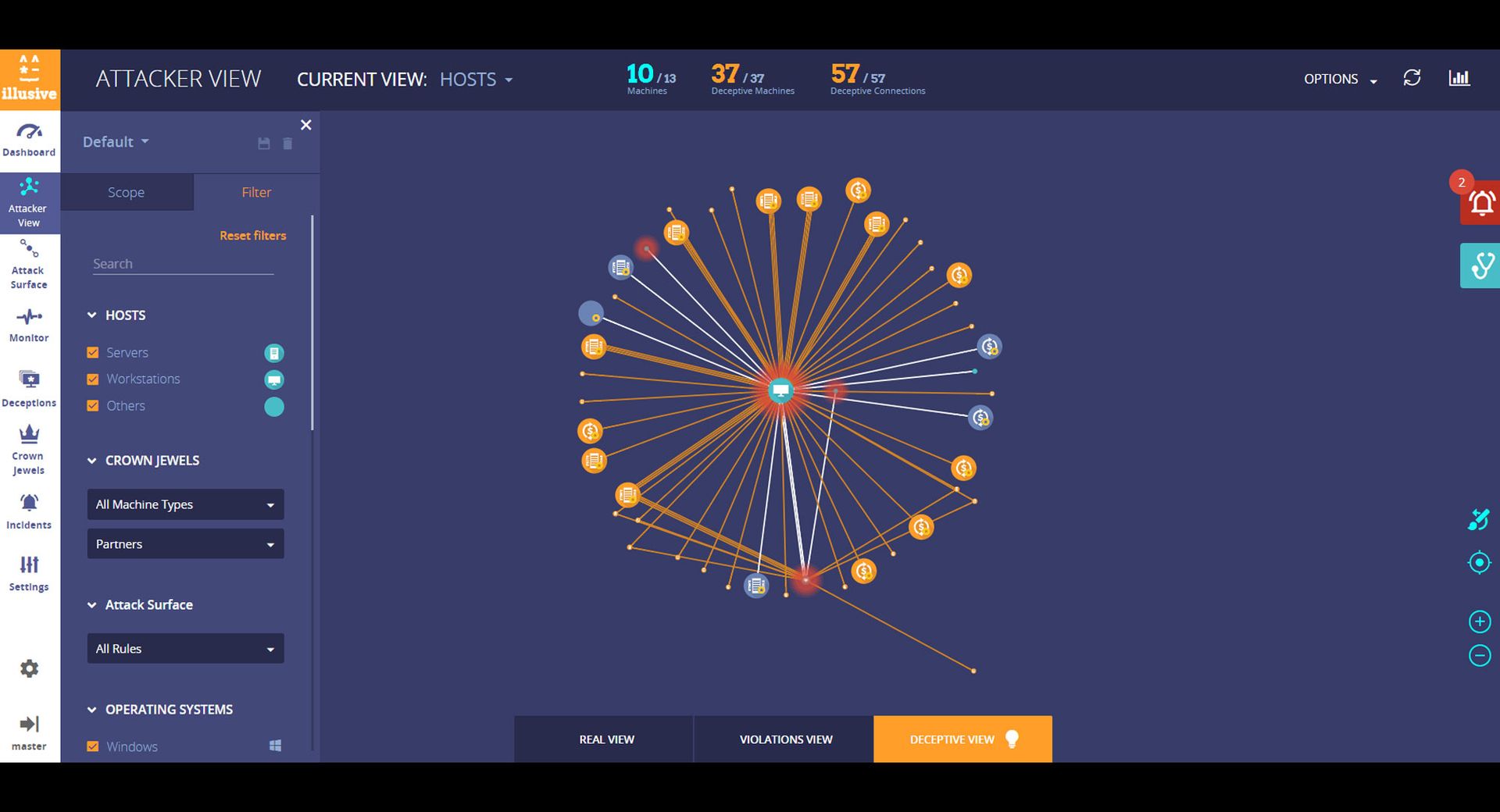
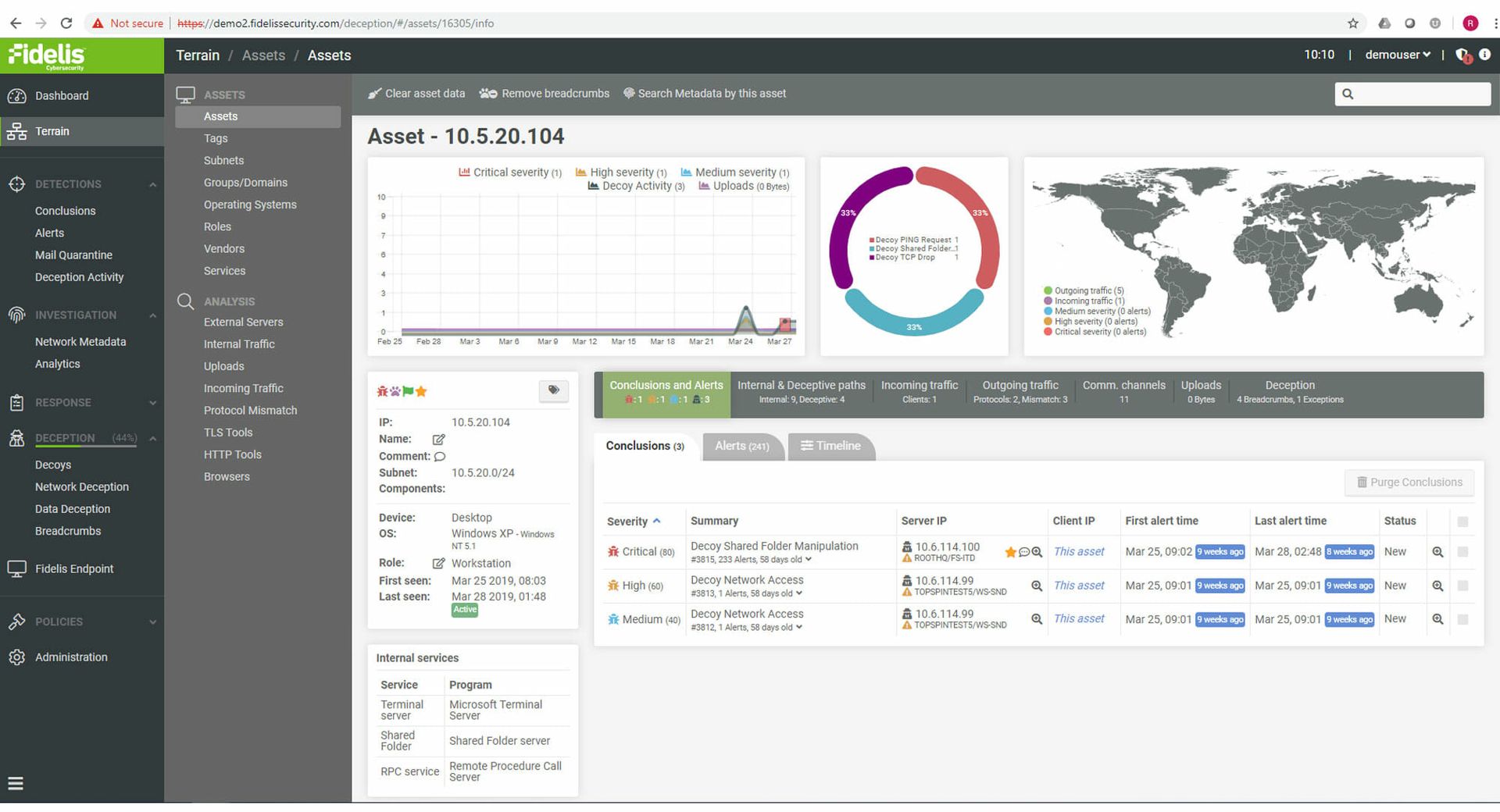
SC Product Reviews: Identity & Access Management
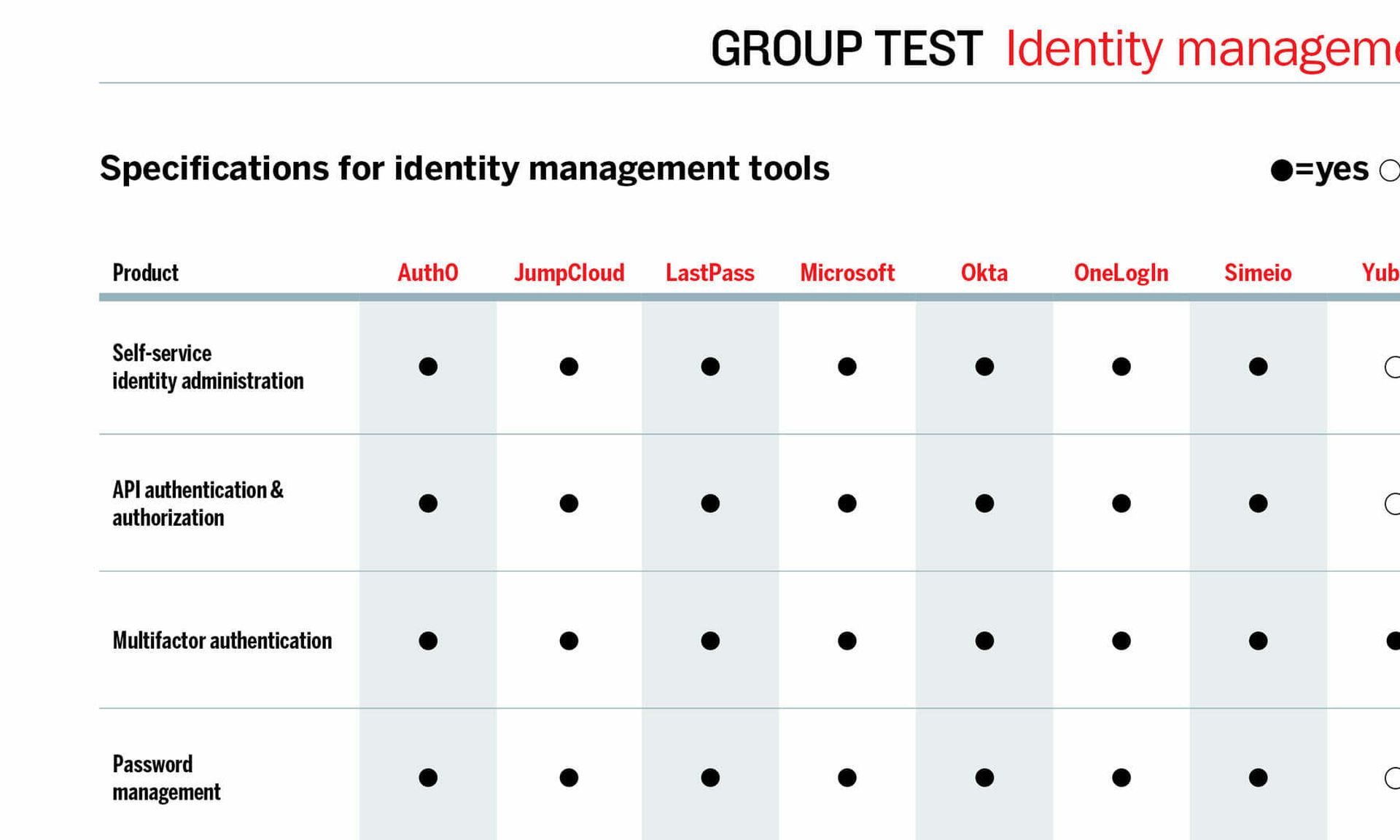
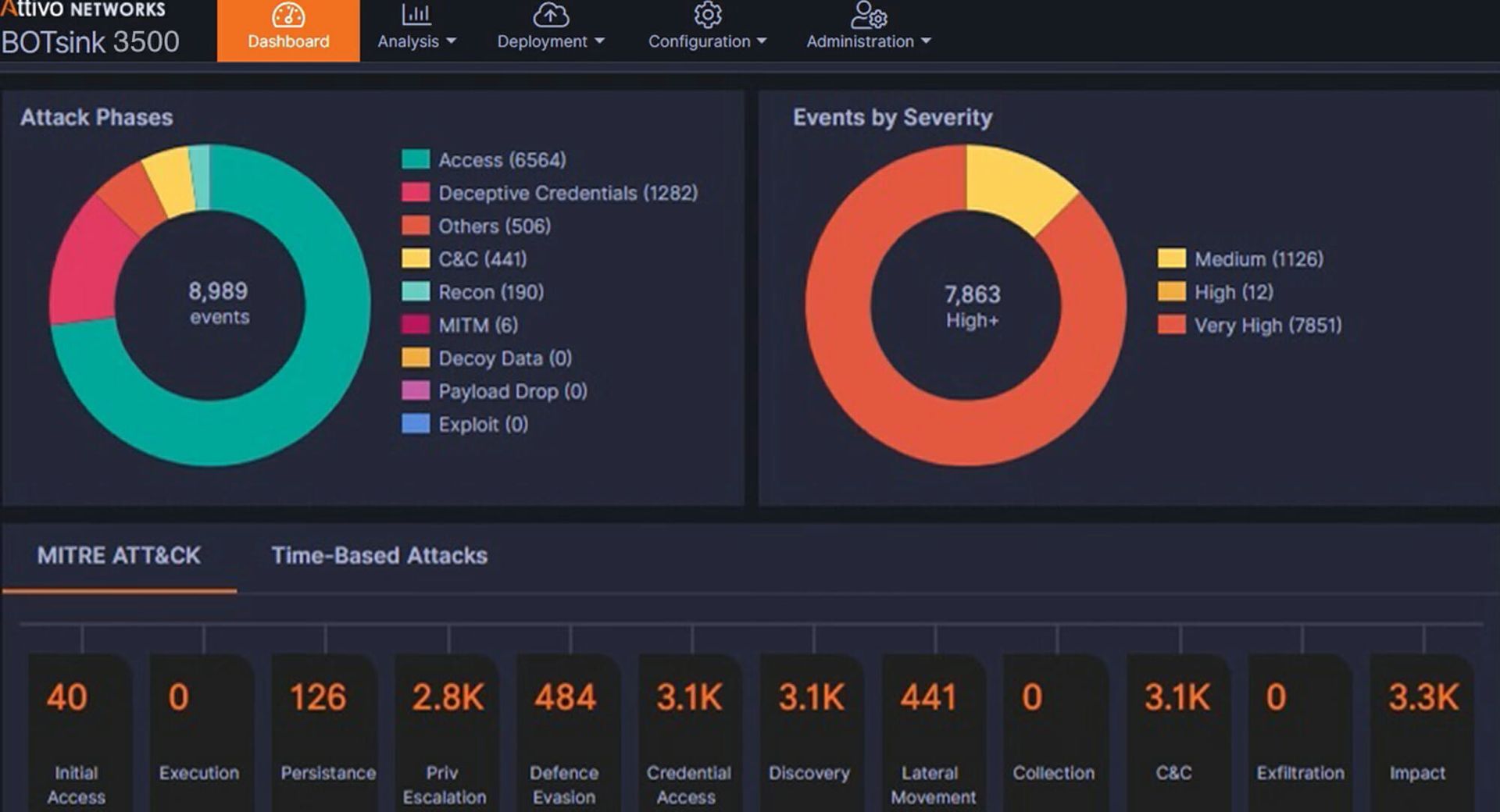
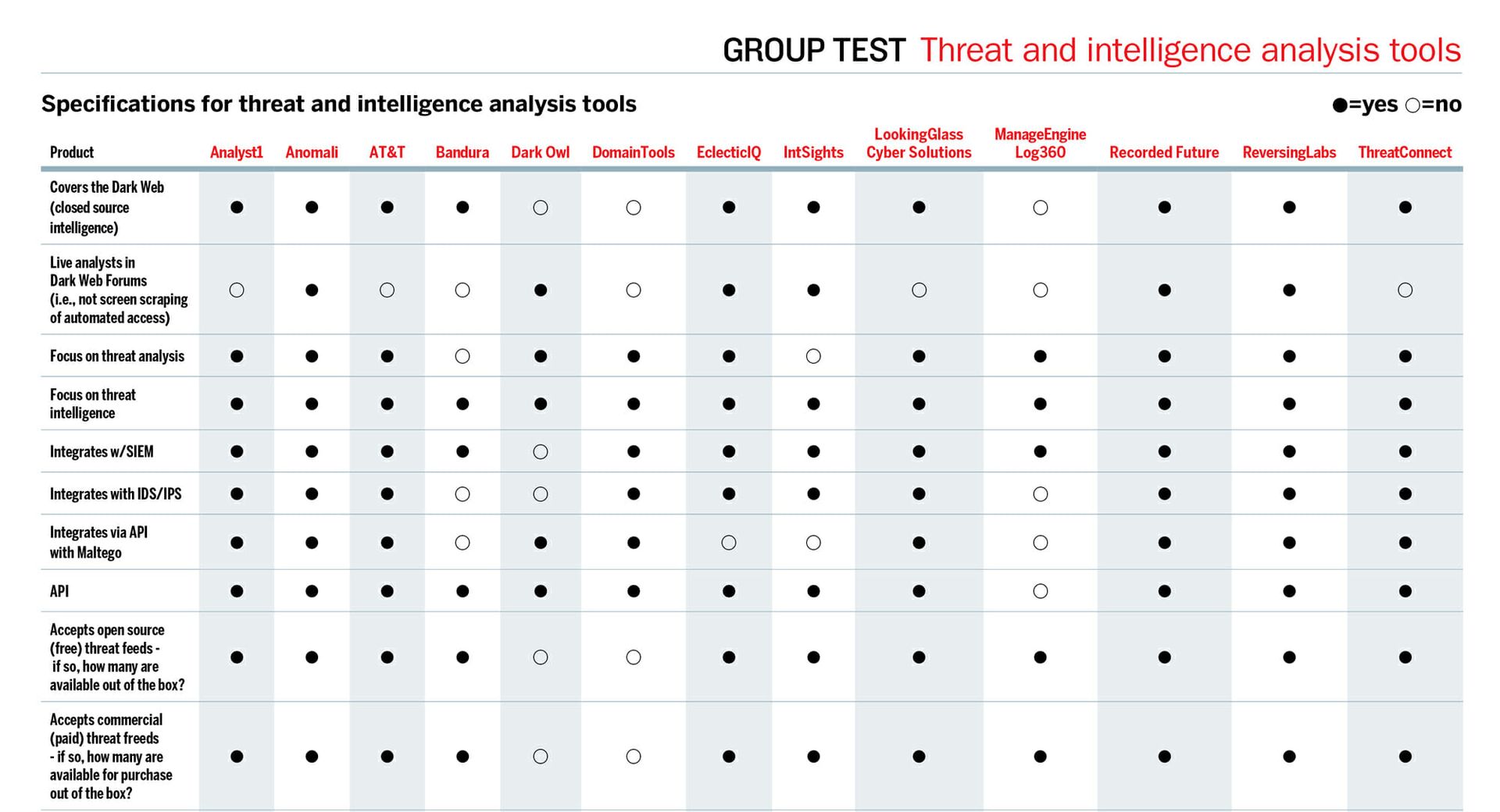
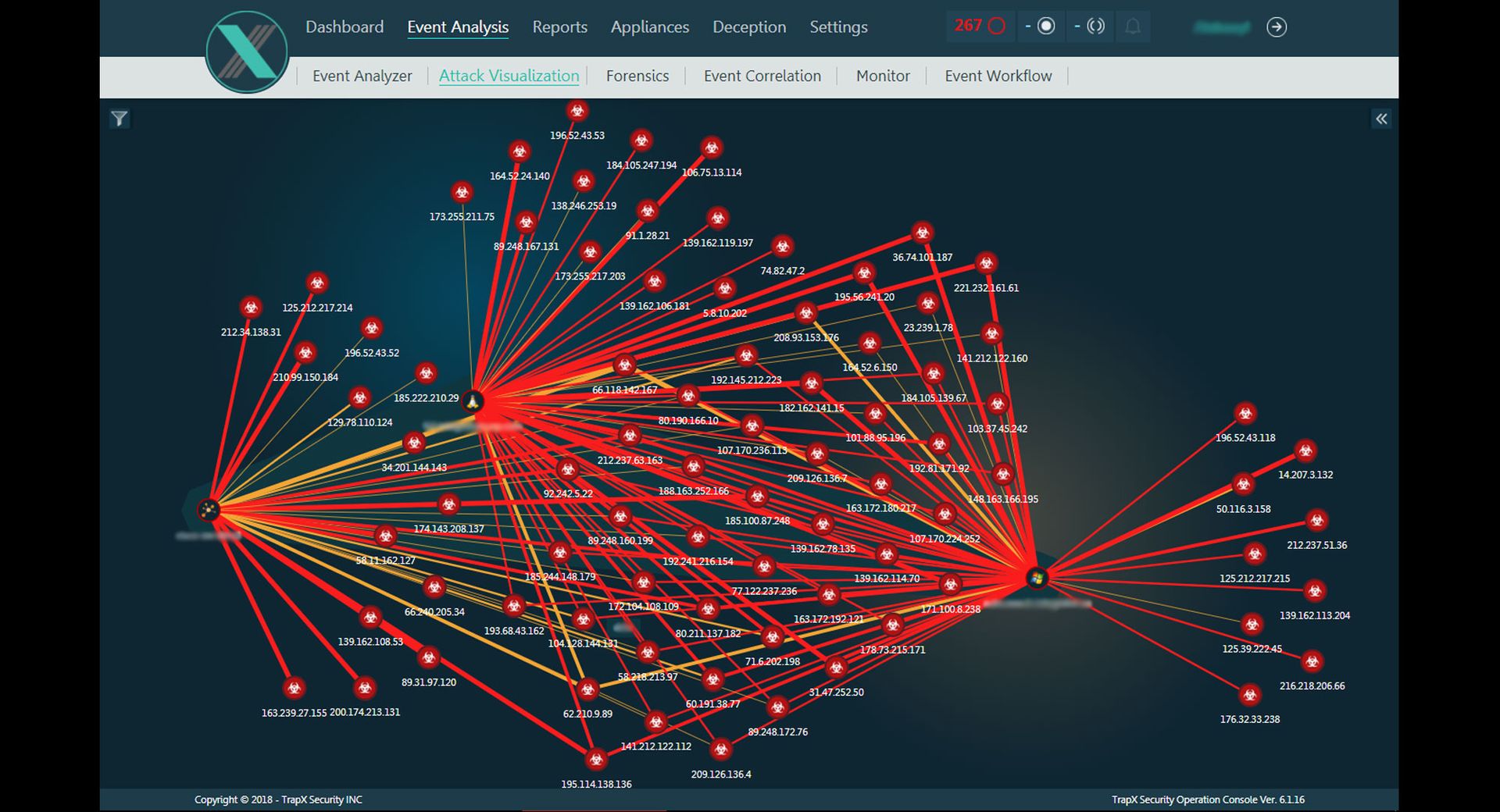
The identity and access management solutions reviewed here guard the proverbial gates of critical organization resources, checking the IDs of everyone that attempts to enter, ensuring identities match end-user claims and privileged access is sufficient for entry.