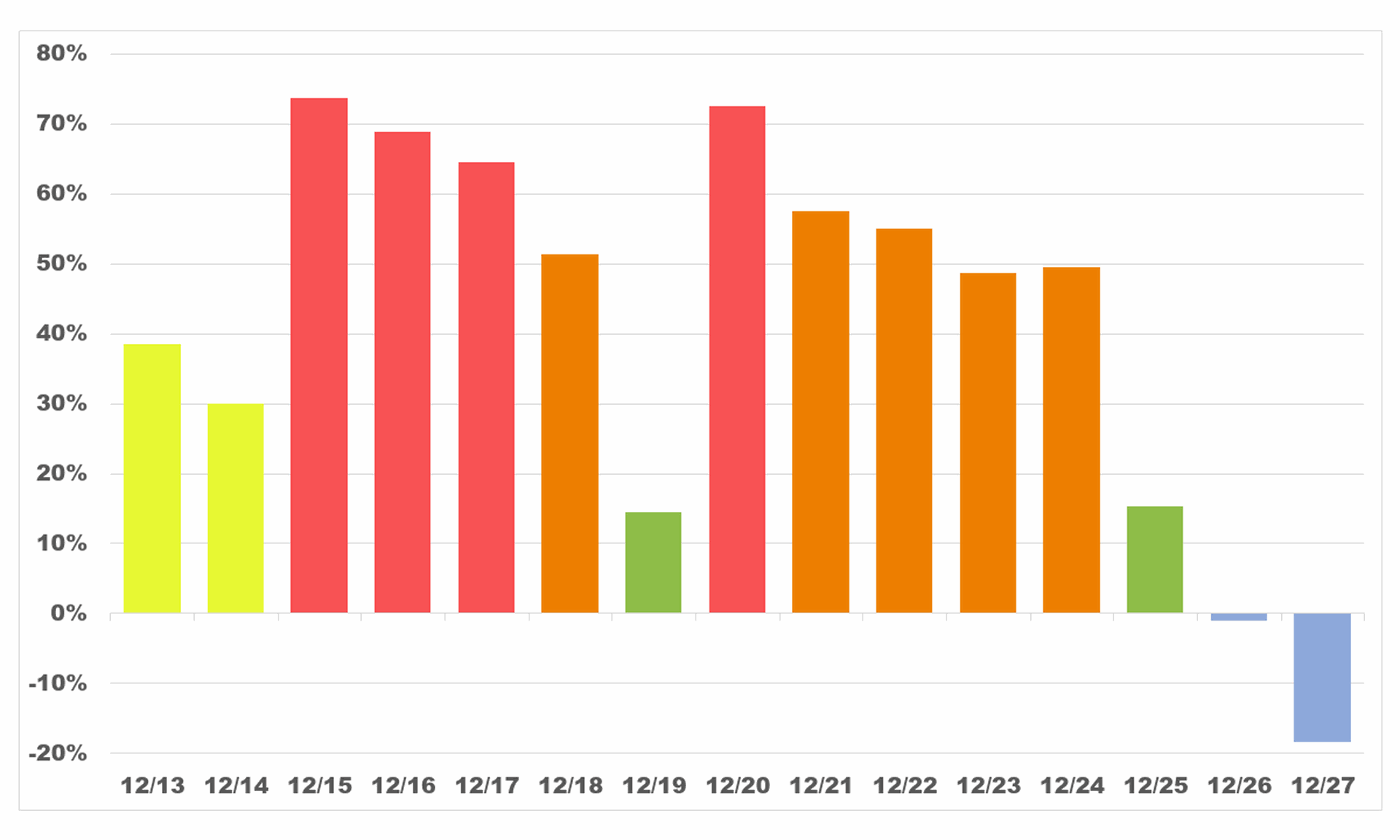
Internet scanning for vulnerable Log4j systems dipped nearly 40% since the day before Christmas, hitting its lowest levels in more than two weeks.
According to data from Sean Gallagher, a threat analyst at Sophos, scanning jumped nearly 40% between Dec. 12 and Dec. 13 and remained at least 30% higher than that December 12 baseline every day except one between Dec. 13 and Dec. 24. On Dec. 25, it dropped to 15% higher than baseline, and the next day it dropped marginally below the Dec. 12 baseline. Scanning continued to drop the day after that.
Apache released the latest patch for Log4j, a ubiquitous logging library, on Dec. 13.
"We typically see a decrease in malicious activity as we get closer to Orthodox Christmas and New Year," said Gallagher. "Scammers and hackers have lives too."
Orthodox Christmas takes place on Jan. 7 and is the Christmas date widely celebrated in Russia.
Scammers lives are probably the reason for the dipping to around 14% above baseline on Dec. 19, said Gallagher. Dec. 19 was a Sunday.
There are two peaks in Gallagher's data he said may reflect the change-over from an initial wave of global data collection to hackers adopting the vulnerability.
"We think a lot of the initial traffic was simply people scanning to see what the vulnerable system population was," he said.
Now in its third week causing a global information security panic, the Log4j vulnerability punches a hole in one of Java's most common library. Experts assume despite frantic efforts to remediate, clean up could take months or years.
Dipping malicious activity around holidays, nights and weekends is common phenomena for criminals and nation-states across the board. In 2018, a researcher with Akamai told Axios that you could tell when World Cup games started by a dip in attacks and when the scores got out of hand when attacks rose again.




