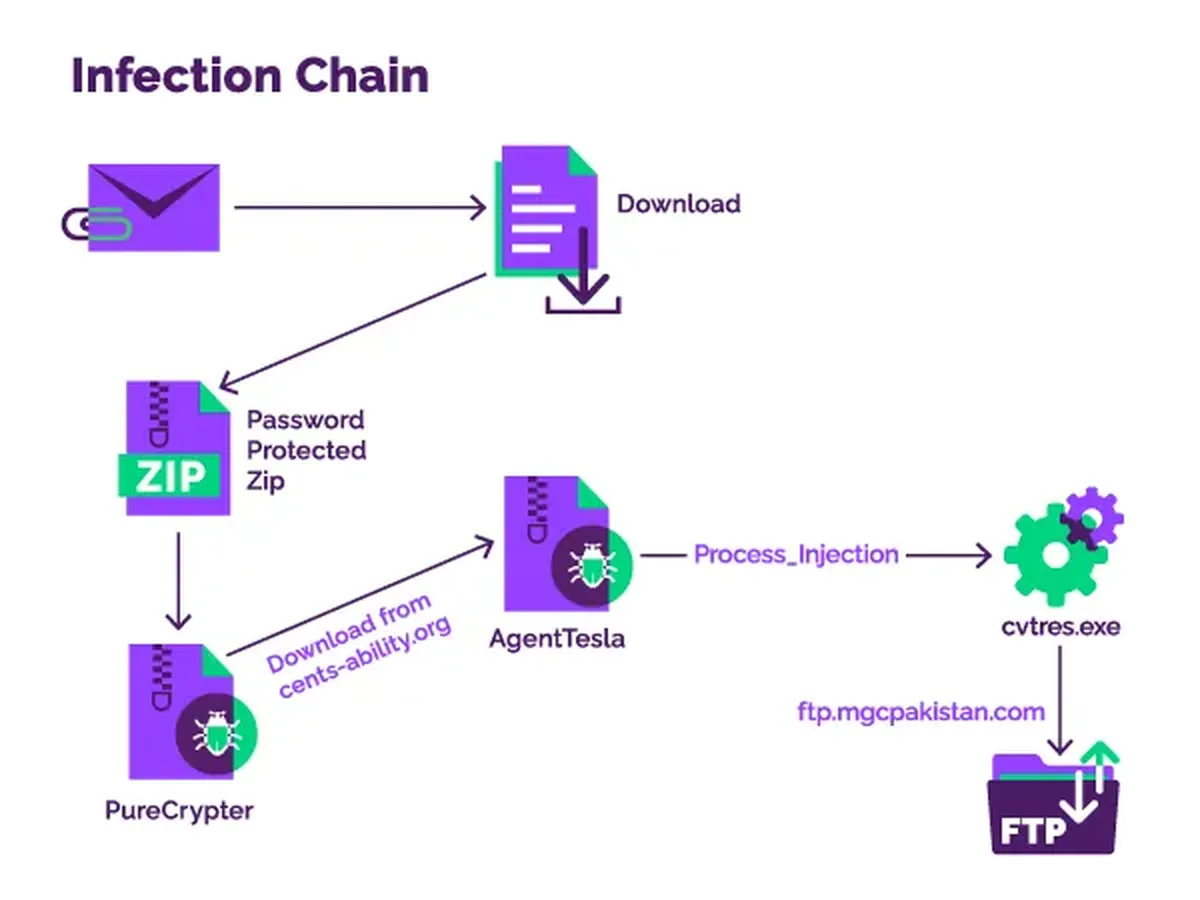
An unknown threat group has been targeting government agencies in Asia Pacific and North America via abuse of the popular Discord network and a hijacked website belonging to a non-profit. The two-stage attacks include enticing victims to install the PureCrypter downloader, which then delivers a variety of possible malware payloads.
In a Thursday blog post, Menlo Labs said it is monitoring the threat actors and government agencies should be aware of the threat. "This threat actor doesn’t appear to be a major player in the threat landscape, but the targeting of government entities is surely a reason to watch out for them," researchers wrote.
The goal of the adversaries is to steal "stored passwords from different browsers, clipboard logging, screen keylogging and screen capturing. It is written in .Net and supports all versions of Windows operating system," researchers wrote.
The researchers said the PureCrypter campaign works by using the domain of a compromised non-profit organization as a command and control (C2) to deliver a secondary payload. This campaign delivered several types of malware, including Redline Stealer, AgentTesla, Eternity, Blackmoon and Philadelphia ransomware.
Menlo Labs assesses that this unknown threat actor will continue to use the compromised and taken infrastructure as long as they can, before finding a new home. The researchers said that while leaving credentials in malware was an OpSec failure by the threat actor, it left a trace for analysts to follow. Fortunately in this case, Menlo’s Cloud Security Platform blocked this attack, which allowed Menlo Labs to see it and start to track this actor.
David Maynor, senior director of threat intelligence at Cybrary, said threat actors are increasingly finding they have the same problem as corporate America: good help is hard to find.
“To close the gap, threat actors increasingly are using for pay malware written and tested by third parties,” Maynor said. “Hosting it on Discord is becoming a common TTP, although through personal experience I know Discord responds quickly to malware takedown requests.”
Casey Ellis, founder and CTO at Bugcrowd, added that any APT that targets government agencies is troubling, especially in these early stages while their identity – and by extension their primary driving motivations -- are still being figured out.