Many organizations, from national security agencies to multinational corporations, will employ ‘white-hat’ hacking teams to hunt for vulnerabilities in software. White hats, or ethical hacking teams, test environments through the eyes of threat actors and provide organizations with insight into vulnerabilities that can be exploited.
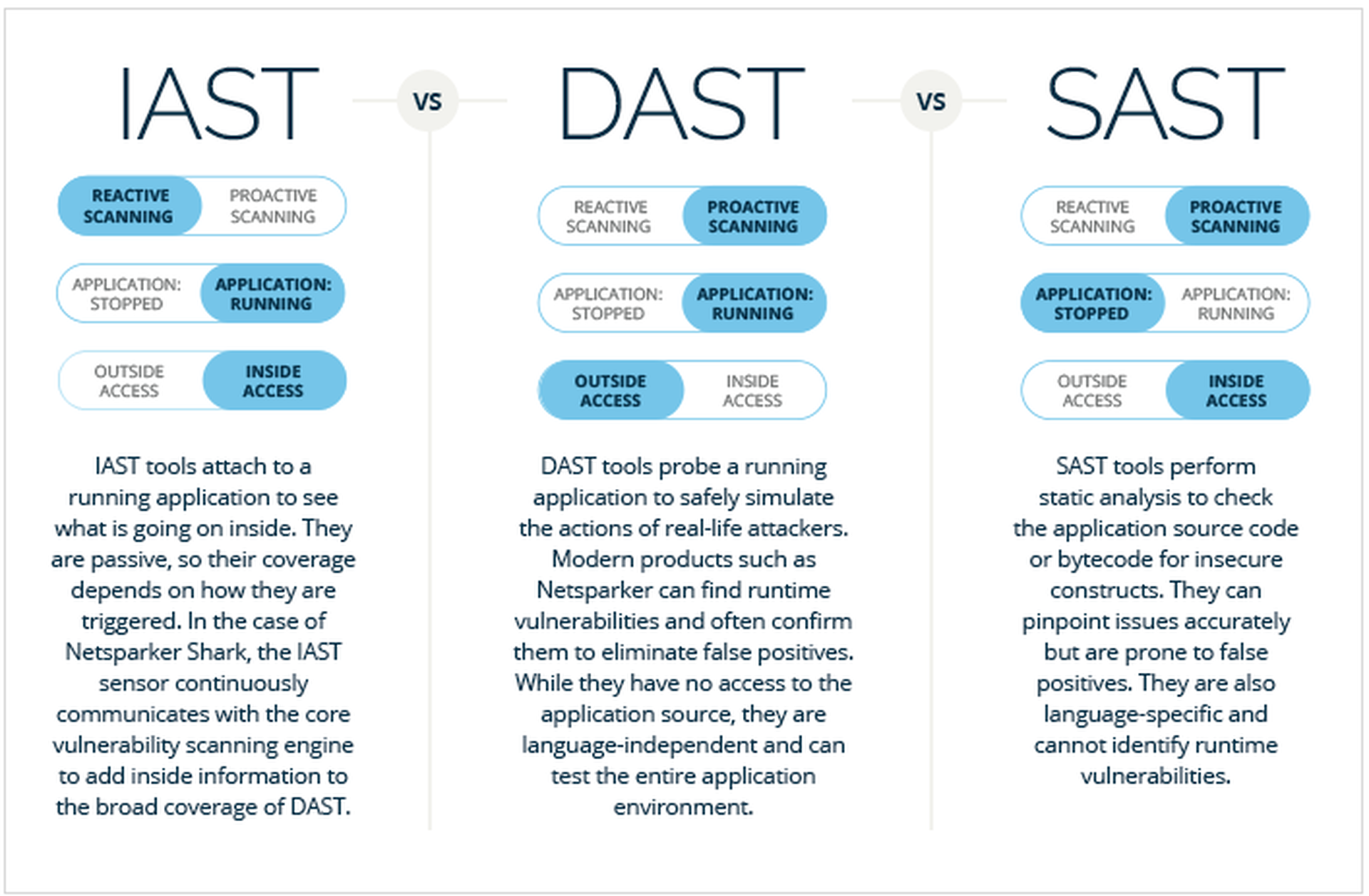
Dynamic Application Security Testing, or DAST, operates by the same logic. Developers might know everything there is to know about an application from the inside, but how can they be sure of its integrity until it responds to an attack from the outside? DAST is a type of application security that seeks to identify vulnerabilities by attacking a web app in the same manner as a hacker would: ruthlessly, through trial and error, without any prior knowledge or access to the application’s underlying source code.
DAST integration benefits organizations
Why should organizations consider implementing dynamic application security testing? Because attacks on web apps are not going to stop any time soon.
A 2021 study by NTT found that 50% of all sites had at least one exploitable vulnerability. Critical vulnerabilities are an enticing entry point and are a key target for threat actors.
The 2022 Verizon Data Breach Investigation Report yielded similar findings: web applications led the list of attack vectors, with nearly 20% of hacks perpetrated through exploitable vulnerabilities. Specifically, attacks on mail servers by way of exploits shot up from 3% in 2020 to 30% in 2021. Without safeguards like DAST in place, why would hackers consider another way in so long as these vulnerabilities persist year after year?
DAST vs. SAST
DAST is not the only option for application security. Static Application Security Testing (SAST) is another approach that many professionals choose to employ.
In SAST processing, scans are conducted with full access to an application’s internal workings. This approach contrasts with DAST processing, which utilizes an outsider’s perspective and has no access to the underlying source code.
Another difference is that DAST tests an application while it’s running to see how it reacts to changes in real time.
Conversely, SAST tests apps that are at rest – since it’s focused exclusively on weaknesses in the source code itself.
DAST is not to be confused with penetration testing. Whereas pen testing generally tasks a human to manually identify vulnerabilities, DAST does not require human input. Instead, it automates the process of identifying and reporting vulnerabilities, which then gives developers more time to make fixes earlier in the software development lifecycle.
How DAST can improve web app security
As companies face increasing pressure to secure their web applications from attacks, it’s not surprising why cybersecurity experts recommend integrating DAST early in the software lifecycle. Here are some of the top reasons why implementing DAST in the SDLC can improve web app security:
#1: Reduce false positives
Dynamic web app testers significantly reduce the number of false positive alerts by helping to distinguish vulnerabilities from benign lookalikes. DAST working in tandem with IAST is especially powerful, as their combined search adds precision in confirming which vulnerabilities are real.
#2: Identify vulnerabilities that can only be found in runtime/production environment
Some vulnerabilities are only identifiable when an app is running. Vulnerabilities in software libraries, server misconfiguration, or improper validation of user input can all evade static and manual testing.
#3: Can address complexity of microservices/containers
More organizations are utilizing distributed microservices architectures, which can raise the attack surface and range of vulnerabilities that crop up in the SDLC. DAST can observe interactions of microservices and help developers triage exploits as they surface in runtime.
#4: Integrates well with other web app scanners, like IAST
To get a robust 360-degree view of their web app’s possible vulnerabilities, organizations can’t do better than integrating DAST with other app security testing tools. For example, software vendor Invicti integrates DAST with IAST: the IAST uses crawlers to access all corners of the application, while working with the DAST to pinpoint the exact location of vulnerabilities
#5: Can reduce reporting times, accelerate remediation
Integrating DAST early in the SDLC allows for faster reporting times and more intelligent remediation. Instead of identifying weaknesses in production or even later, DAST allows developers to quickly spot and fix blind spots before they surface as a security issue further down the pipeline.
Closing Thoughts
The ancient Chinese military philosopher Sun Tzu writes: “If you know yourself but not the enemy, for every victory gained you will also suffer a defeat.”
As anachronistic as it may be to re-gloss Tzu’s teachings for the modern era, it’s difficult to dispute their relevance. Consider an example from another industry: auto manufacturers know every bit of machinery that goes into the making of their cars. And yet they still run crash tests to see how the car’s structural integrity performs under pressure.
Success on the cyber battlefield also requires observing, anticipating and even simulating the dangers that encroach from the outside, so that one can be prepared to stop the real attack when it happens. DAST provides organizations an effective way to measure how their apps respond to intrusion attempts early in the SDLC, but without any of the consequences that accompany a real-world attack. By integrating DAST alongside other scanning methods, organizations can increase visibility of their attack surface and resolve blind spots before it’s too late.




