Keeping tabs on all of an organization's assets can be a challenge. Cloud service adoption, remote work and the occasional BYOD have changed (and expanded) what constitutes an organization's attack surface. But how do we secure the new perimeter?
"Without a full, detailed inventory of all your IT assets," said cloud-security firm Qualys in a recent white paper, "your infosec team won't be able to properly protect your organization because the things that pose the highest risk are the ones that you don't know are there."
There's no single-bullet solution for discovering and inventorying assets in the cloud. But combining different types of scans will give you as complete a picture as possible of your organization's assets, and your organization's security posture.
Different ways to penetrate the cloud
You need to scan your organization's cloud and what's left of the on-premises network. Unfortunately, there's no single scanning method that provides perfect clarity. Let's quickly go through the pros and cons of each.
The most basic method is an unauthenticated external scan that shows what your network looks like to an outside observer — or an attacker. This is a good way to find internet-facing weak spots, but it only gives you the surface view.
Next up is an authenticated scan, one in which the scanning tool is given authorization to enter the company network and probe it from the inside. This is more comprehensive than an unauthenticated scan and can detect flaws and misconfigurations, but it takes longer and may have blind spots if it can't gain access to certain areas.
There's also API-based scanning, which uses APIs provided by public cloud service providers (CSPs) such as Amazon, Google or Microsoft. This gives you a view of your organization's cloud instances from the CSP's perspective, but its reach is limited as it has trouble detecting flaws in open-source software.
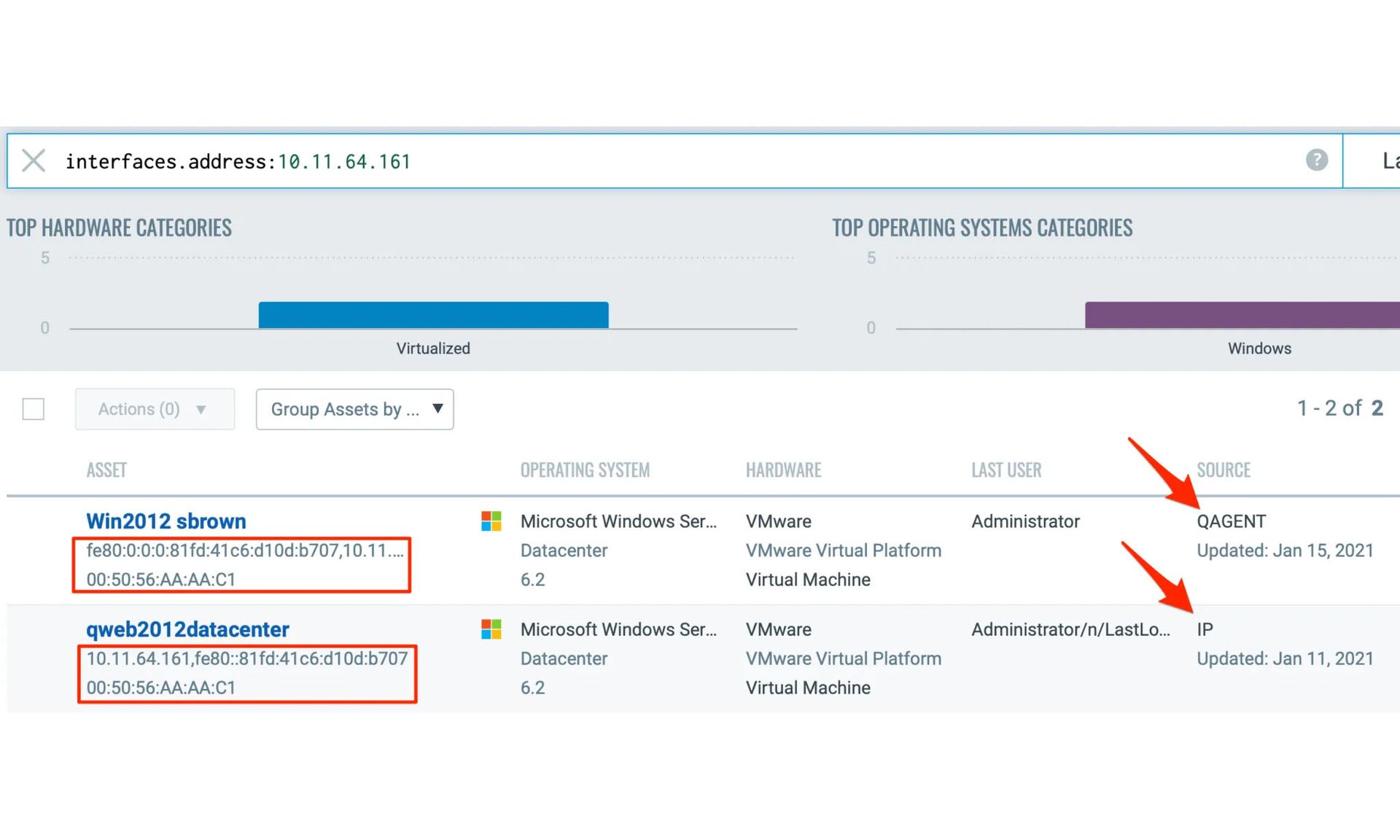
The most sophisticated method is agent-based scanning. A small piece of software is installed on every endpoint, server, database and other piece of hardware and in every software asset. The agent checks the asset for vulnerabilities and outdated software, installs patches if necessary, and monitors the asset continuously. The agent also profiles the asset and sends the profile back to a central program for inventorying.
Agent-based scanning is very thorough, but it doesn't tell you what the network looks like from outside and can't find many external vulnerabilities. Nor can it monitor "shadow IT" devices and software that may have been installed or used by employees without authorization.
"Agent-based scanning has one major disadvantage: its inability to provide the perspective of the attacker," said Spencer Brown, security solutions architect at Qualys, in a 2021 blog post. "These network detections are vital to prevent an initial compromise of an asset."
Comprehensive scanning for cloud visibility
The most comprehensive way to get a good picture of your organization's assets is to combine all these scanning methods and feed the results into an intelligent program that can combine the information and present it coherently.
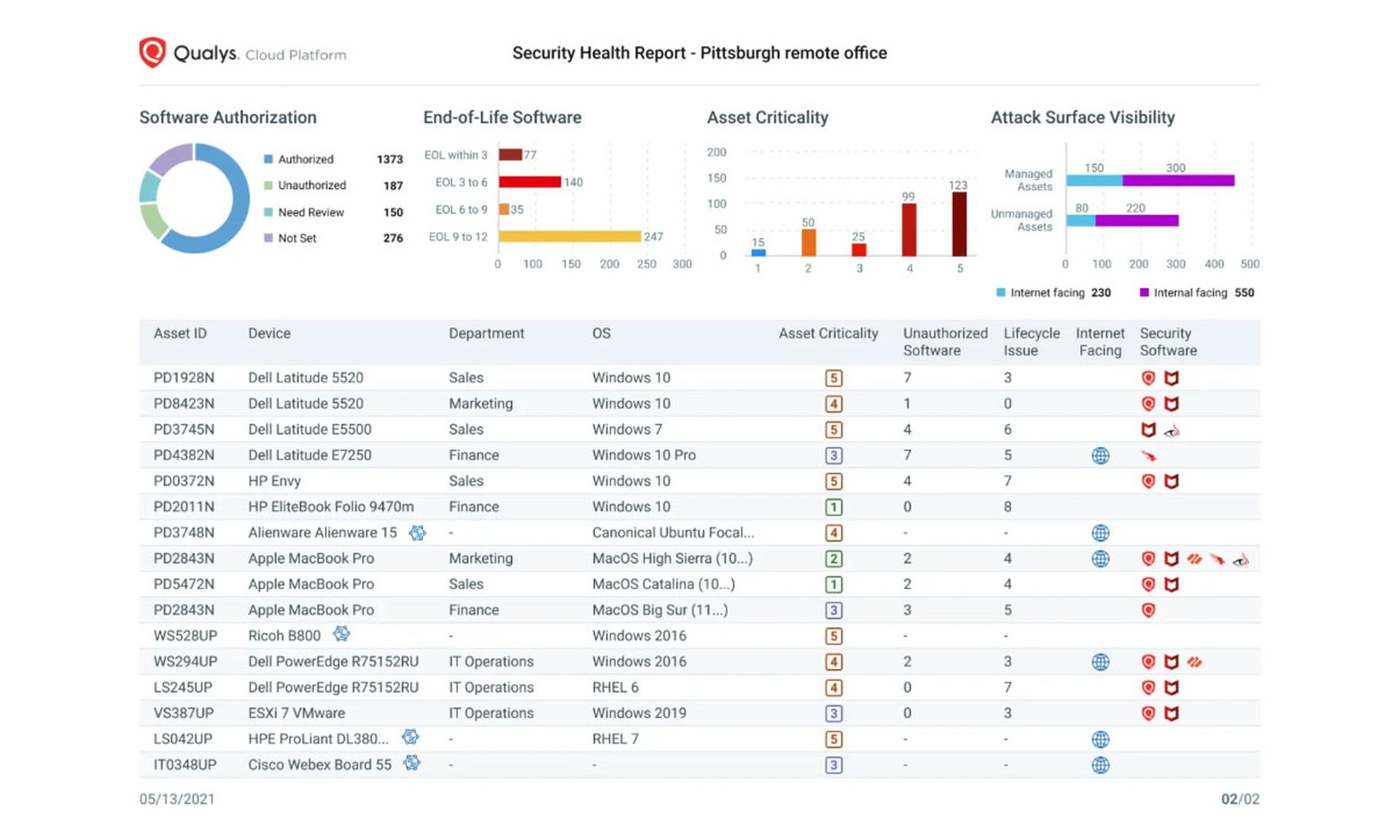
The Qualys Cloud Platform builds such a picture using unauthenticated, authenticated and agent-based scans. Its most basic feature, Qualys Global AssetView, is entirely free.
"Global AssetView automatically discovers and classifies all IT assets including software, on-prem devices and applications, mobile, clouds, containers, and enterprise IoT devices using both agent and agentless methods," said Ed Rossi, former vice president of product management at Qualys, in a 2021 blog post.
The Cloud Platform can even label assets on different public clouds using consistent metadata, and merge duplicate asset-inventory results from agent-based and unauthenticated scans.
Paid additional modules build in threat protections, vulnerability management, endpoint detection and response, compliance monitoring and other features, but the basis of it all is free asset discovery and management.
"The starting point of security programs is to know what you have," said Sumedh Thakar, CEO and president of Qualys, in a 2021 blog post. "By combining agent-based and agentless data collection, active scanning to track known assets, passive scanning to identify unknown assets, and APIs for automation, the Qualys Cloud Platform provides comprehensive asset discovery across your entire infrastructure, including on-premises, cloud, container, OT, and IoT."
Why on-prem tools no longer cut it
Keeping track of assets was once simpler. Servers, databases and most endpoints were on the premises, and the network map was generally static. Security involved putting a perimeter around the office network, putting antivirus software on endpoints and making remote laptops log into the company VPN.
"Network perimeters were well-defined and IT environments were tightly encapsulated," said the Qualys white paper. "Accounting for and monitoring all the hardware, software and networking elements in these self-contained and sealed IT environments was straightforward."
Now many or most of your systems are in the cloud. Employees connect to the network from anywhere using their own laptops and smartphones as well as company-issued devices.
The network map, if you can still call it that, is dynamic. Endpoints continually log on and off and change locations. Cloud instances are spun up and wound down, while data is scattered over an array of servers, few of which your organization may control.

"Many organizations are finding that ... they have lost the visibility they once had over their IT assets," warns the Qualys white paper. "As these blind spots multiply within an IT environment, so does the risk of hacker intrusions, data breaches, malware infections, internal IT policy violations and regulatory non-compliance."
The old on-prem network-scanning tools don't work well in the cloud, and the perimeter has vanished. So how are you supposed to know about everything that's on your network at any given moment?
It's a brave new world. Organizations that are interested in keeping their cloud components secure would do well to consider the employment of newer technologies geared for the modern digital landscape.




