In a survey CyberRisk Alliance Business Intelligence conducted among InfraGard’s membership last fall, respondents in the healthcare sector cited many headwinds when trying to defend itself against a blistering onslaught of ransomware attacks.
Healthcare's vulnerabilities to ransomware are widespread. Hospitals and first responders use an abundance of internet of things (IoT) sensors and mobile devices. These devices are often interfaced with outdated, vulnerability-laden operating systems. These challenges were further illustrated in a recent eBook CyberRisk Alliance produced in partnership with Sophos:Condition Critical: How Ransomware Gangs Are Targeting Healthcare and How to Fight Back.
Now, a new Sophos report shows that the struggle for healthcare continues.
The State of Ransomware in Healthcare 2022 is a carve out of Sophos’ annual study of the real-world ransomware experiences of 5,600 IT professionals, including 381 in healthcare, from 31 countries.
Ransomware still rising
Among the findings, ransomware attacks against healthcare continues to increase:

Some improvement in response
On the plus side, healthcare organizations are getting better at restoring data after an attack.
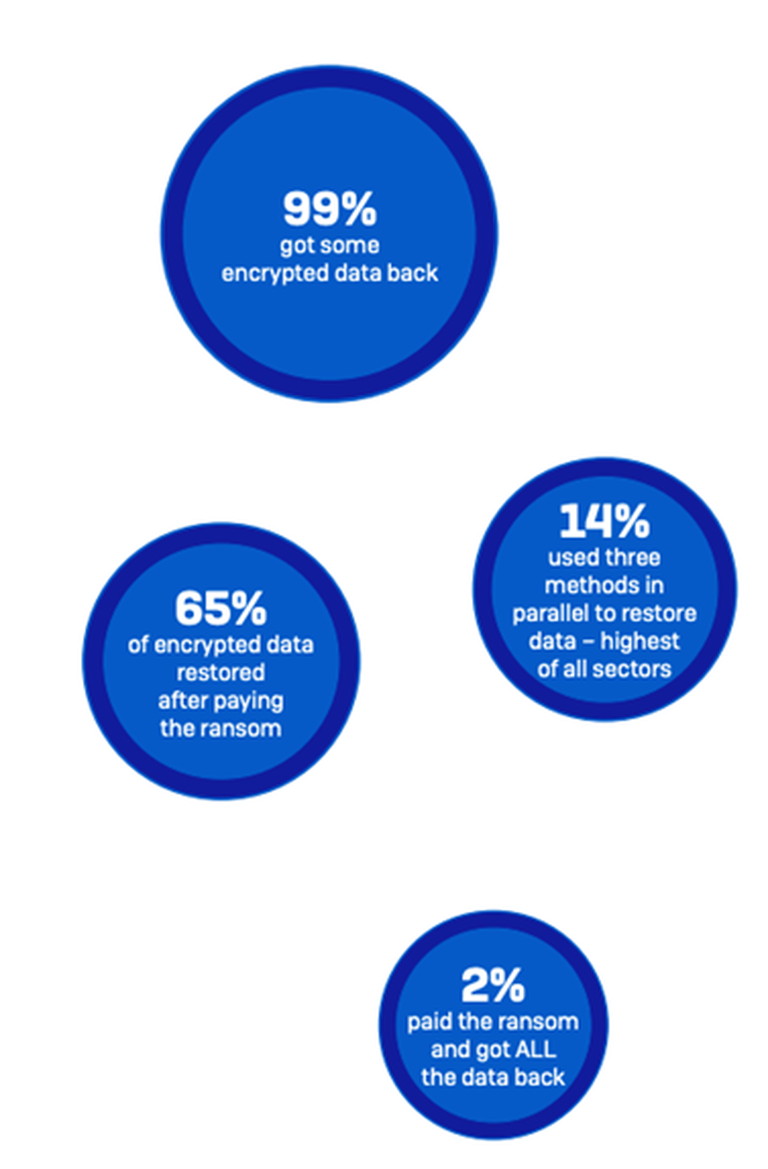
Backups are the number one method used to restore data, used by 72% of healthcare organizations whose data was encrypted.
At the same time, 61% reported that they paid the ransom to restore data, and 33% said they used other means to restore data.
These numbers reflect the fact that many healthcare organizations use multiple restoration approaches to maximize the speed and efficacy with which they can get back up and running. In fact, overall, a little more than half (52%) of the respondents whose organizations’ data had been encrypted used multiple methods to restore data.
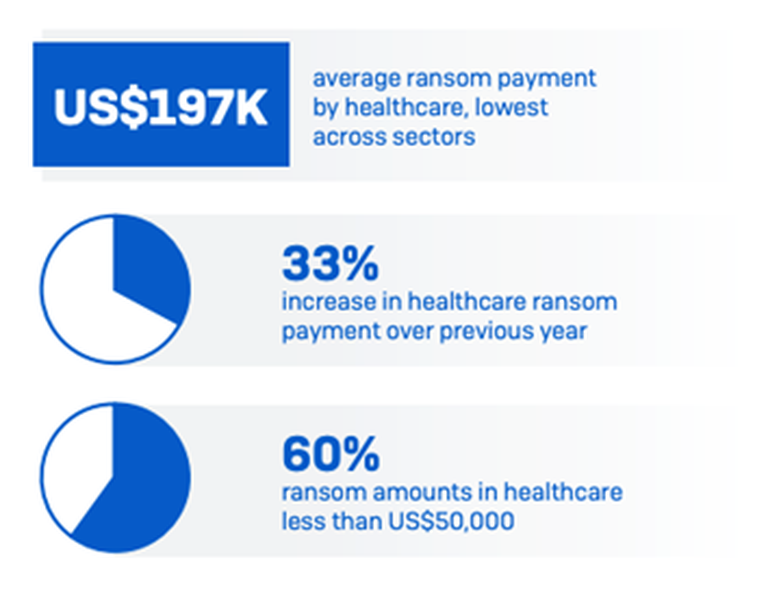
Smaller ransom payouts
While healthcare is at the top of the list for volume of payments, it’s actually at the bottom of the list for the amount paid. Overall, healthcare had the lowest average ransom payment (around US$197K) of all named sectors.
So, while there is a high occurrence of healthcare paying the ransom, the ransom amounts are relatively small. These low ransom payments are likely driven by the constrained finances of many healthcare organizations, particularly those in the public sector. They simply don’t have more money for the attackers to squeeze out of them.
The role of cyber insurance
The report also revealed that cyber insurance is driving healthcare efforts to improve their defenses: 97% of healthcare organizations with cyber insurance have upgraded their cyber defenses to improve their cyber insurance position.
Meanwhile, cyber insurance is almost always paying out: in 97% of incidents where the healthcare organization had cyber insurance that covered ransomware, the insurer paid some or all the costs incurred (with 47% overall covering the ransom payment)
For more information, download the full State of Ransomware in Healthcare 2022 report.