As news came out over the past several days that the threat actor dubbed AeroBlade conducted espionage by targeting a U.S. aerospace organization via a spearphishing attack, security pros were concerned that American companies still have not learned basic cybersecurity lessons.
"This is a great example of how the world still does not take cybersecurity seriously enough,” said Roger Grimes, data-driven defense evangelist at KnowBe4. “Aerospace is a critical infrastructure industry and it should have cybersecurity as strong as any organization. And yet, spear phishing – which has been around for over three decades – continues to have consistent exploitation success.”
Grimes said the aerospace industry and other critical industries need to take four basic steps to prevent these phishing attacks: aggressive anti-social engineering training, 100% consistent patching, phishing-resistant multifactor authentication, and strong password policies. “If the aerospace industry took just those four steps, threats such as AeroBlade would not see continued success,” said Grimes.
In a blog post Nov. 30, the BlackBerry Threat Research and Intelligence team explained that the spearphishing attack itself was a weaponized document sent as an email attachment that contained an embedded remote template injection technique and a malicious VBA macro code.
The researchers said evidence suggests that the attacker’s network infrastructure and weaponization became operational around September 2022. BlackBerry assessed with “medium to high confidence” that the offensive phase of the attack occurred in July 2023.
Here’s how the researchers said the attack was executed (see illustration below): A malicious Microsoft Word document called [redacted].docx was delivered via email spearphishing, which when executed manually by the user, employs a remote template injection to download a second stage file called “[redacted].dotm.” This file in turn executes "item3.xml,, which creates a reverse shell connecting to "redacted[.]redacted[.]com" over port 443.
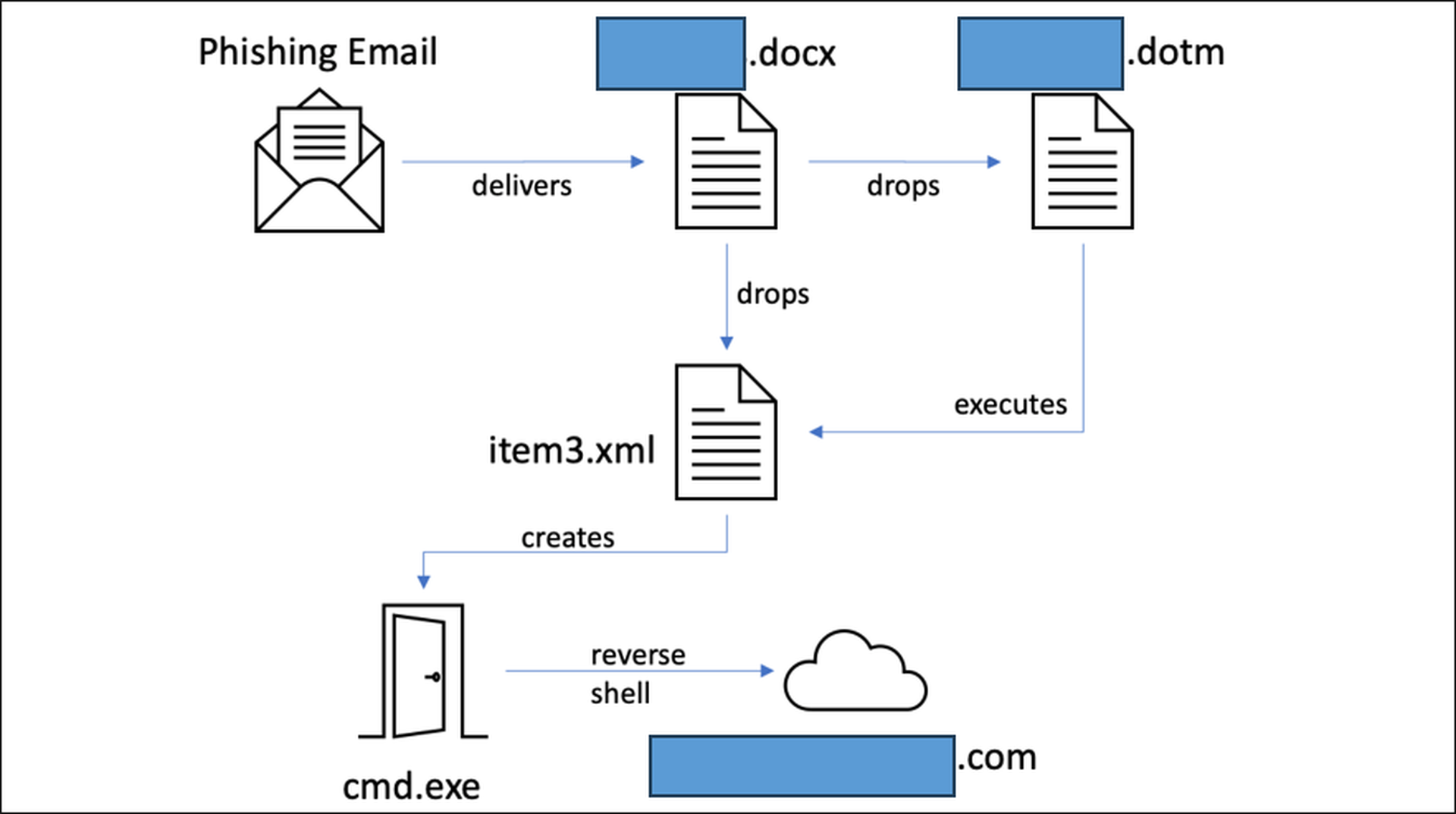
Why these attacks are more sophisticated than they first appear
Callie Guenther, senior manager of cyber threat research at Critical Start explained that the time gap of almost one year between the initial attack and the subsequent offensive phase suggests that the attackers were developing and refining their tools and strategies. Guenther said this indicates a high level of commitment and resources, typical of state-sponsored or highly-organized criminal groups.
Guenther added that the seriousness of these attacks lies in their sophistication, targeted nature, and the potential impact on critical infrastructure and sensitive information. While the initial attack vector was a targeted email scam, the weaponized document used a remote template injection technique, a more sophisticated method compared to traditional phishing attacks. Guenther said this technique involves retrieving a payload from a remote server, which is executed when the victim enables macros in the Microsoft Word document.
“It's is a clever way to bypass some security measures that might catch more straightforward malicious attachments,” said Guenther.
The remote template injection involved deploying a DLL that functions as a reverse shell, explained Guenther. It’s a method used to gain control over a system by forcing it to open a port and communicate with a command-and-control server that lets attackers remotely execute commands on the victim's machine. Guenther said the malware had capabilities to enumerate directories, indicating a reconnaissance effort.
“This is typical in espionage operations where the attackers first assess the value of the data available on the infected host before deciding on their next steps,” said Guenther. “The DLL used in the attack was heavily obfuscated and equipped with anti-analysis and anti-disassembly features. This makes it difficult for cybersecurity professionals to analyze and understand the malware, a common tactic to delay detection and mitigation. They also used a Task Scheduler for persistence, naming a task ‘WinUpdate2’ to run daily. This tactic ensures the malware remains active and undetected on the infected system for a prolonged period.”
Donovan Tindill, director of OT cybersecurity at DeNexus, added that the threat actor was patient, having spent nine months in a testing phase before escalating their offensive attack in July 2023. In these more sophisticated campaigns, Tindill said threat actors will seek to learn as much as possible about the organization, including their strengths, weaknesses, financial data, cyber-technical data, vulnerabilities, and passwords.
Tindill said although BlackBerry claims commercial cyber espionage with “high confidence,” there’s no assurance that the threat-actor will not escalate to ransomware, data encryption, and demand extortion payment in the future. The aerospace sub-industry has also not been identified, such as an airline, airport, or an aircraft manufacturer.
“Each of these subindustries could have a different impact on the aerospace supply chain,” said Tindill. “Aerospace organizations are generally very large and have more mature cybersecurity programs. A highly-motivated threat-actor would need to be patient, gather data, and take careful steps to avoid detection to ensure long-term mission success.”
Anurag Gurtu, CPO at StrikeReady, called the AeroBlade attack serious because of the sensitive nature of data held by aerospace companies, including national security details and technology patents. Gurtu added that the techniques employed often involve well-crafted emails and social engineering tactics designed to extract sensitive information or spread malicious software.
“To counter such threats, it's essential for organizations to not only strengthen their cybersecurity defenses, but also to emphasize employee training in identifying and responding to phishing attempts,” said Gurtu. “This dual approach is crucial in safeguarding against potential breaches that could lead to significant intellectual property loss and national security risks.”



