A newly discovered and heavily exploited Docker host vulnerability has allowed hundreds of websites to be illegally accessed and injected with a cryptocurrency miner.
The flaw, CVE-2019-5736, allows an attacker to gain host root access from the Docker container through the remote Docker API. Normally, the Docker API allows admins to control a remote Docker host, including automating the deployment process, control and get the state of your containers, but if this is accessed by an attacker a network can be compromised, said Imperva researchers Vitaly Simonovich and Ori Nakar in a new report.
In this case Imperva found the exposed Docker remote API is has been taken advantage of by hundreds of attackers with many using the access to mine Monero while others are running production environments of MySQL database servers, Apache Tomcat, and others.
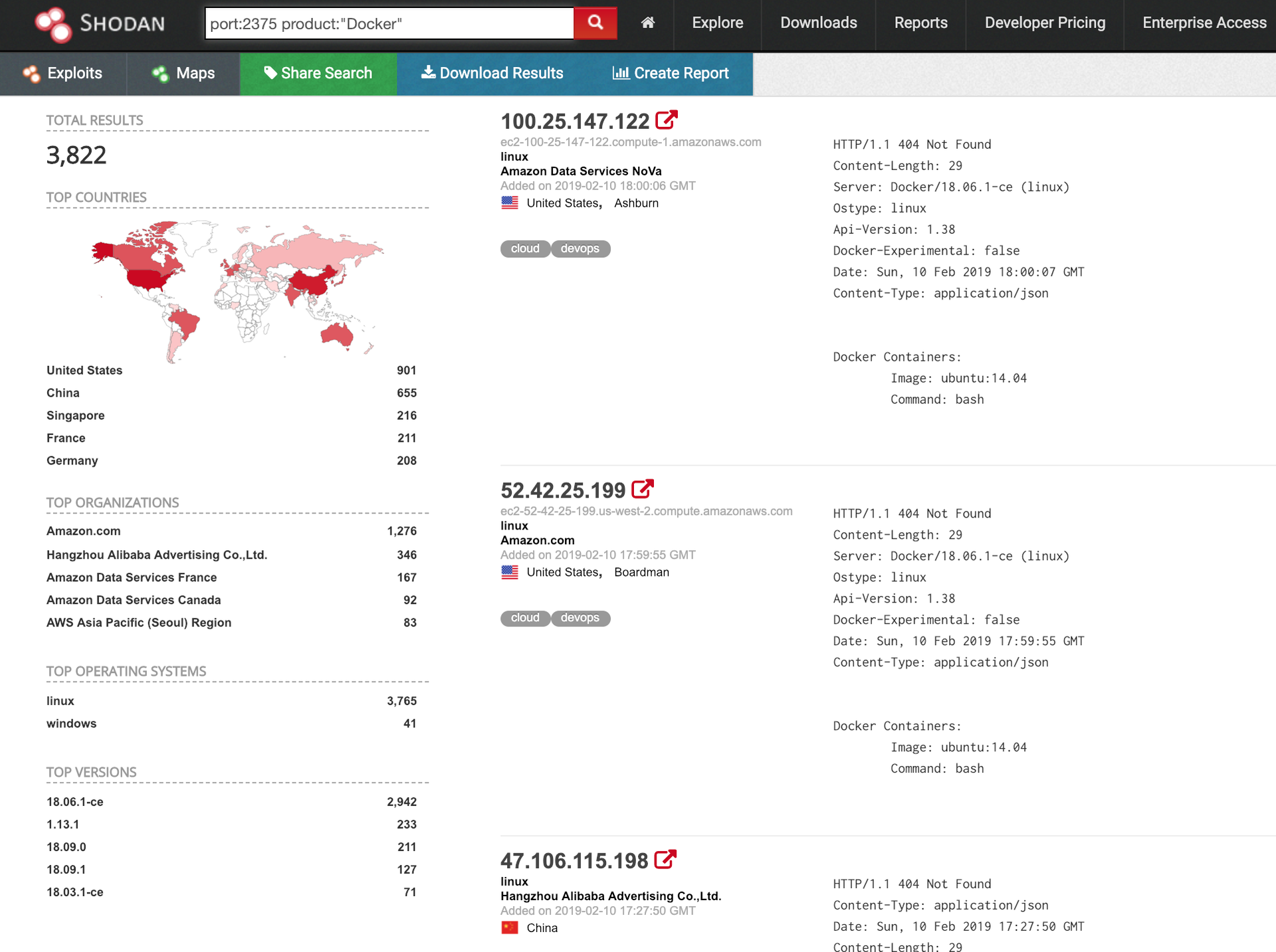
“We found 3,822 Docker hosts with the remote API exposed publicly. We wanted to see how many of these IPs are really exposed. In our research, we tried to connect to the IPs on port 2735 and list the Docker images. Out of 3,822 IPs, we found approximately 400 IPs are accessible,” the researchers wrote.
Besides mining cryptocurrency this level of access potentially allows an attacker to launch additional attacks with masked IPs, create a botnet, host services for phishing campaigns, steal credentials and data, and pivot attacks to the internal network.



