A cyber espionage group linked to the Iranian government has been impersonating think-tank employees to phish Middle Eastern nuclear weapons experts, according to researchers at Proofpoint.
The group — called “TA453,” “Charming Kitten” or “APT35,” depending on the threat intelligence service you’re relying on — has a long track record of targeting U.S. and European government officials, politicians, think tanks and entities involved in critical infrastructure.
The latest campaign detailed by Proofpoint dates from March to May of this year and begins with benign emails that seek to establish a rapport with foreign policy researchers in the West.
Those initial emails were later followed by phishing emails that link to a password-protected DropBox URL, ostensibly to access the research. Instead, it executes .RAR and LNK files and run a PowerShell script that installs a backdoor on the victim’s system, before calling out to a cloud hosting provider for additional malware payloads.
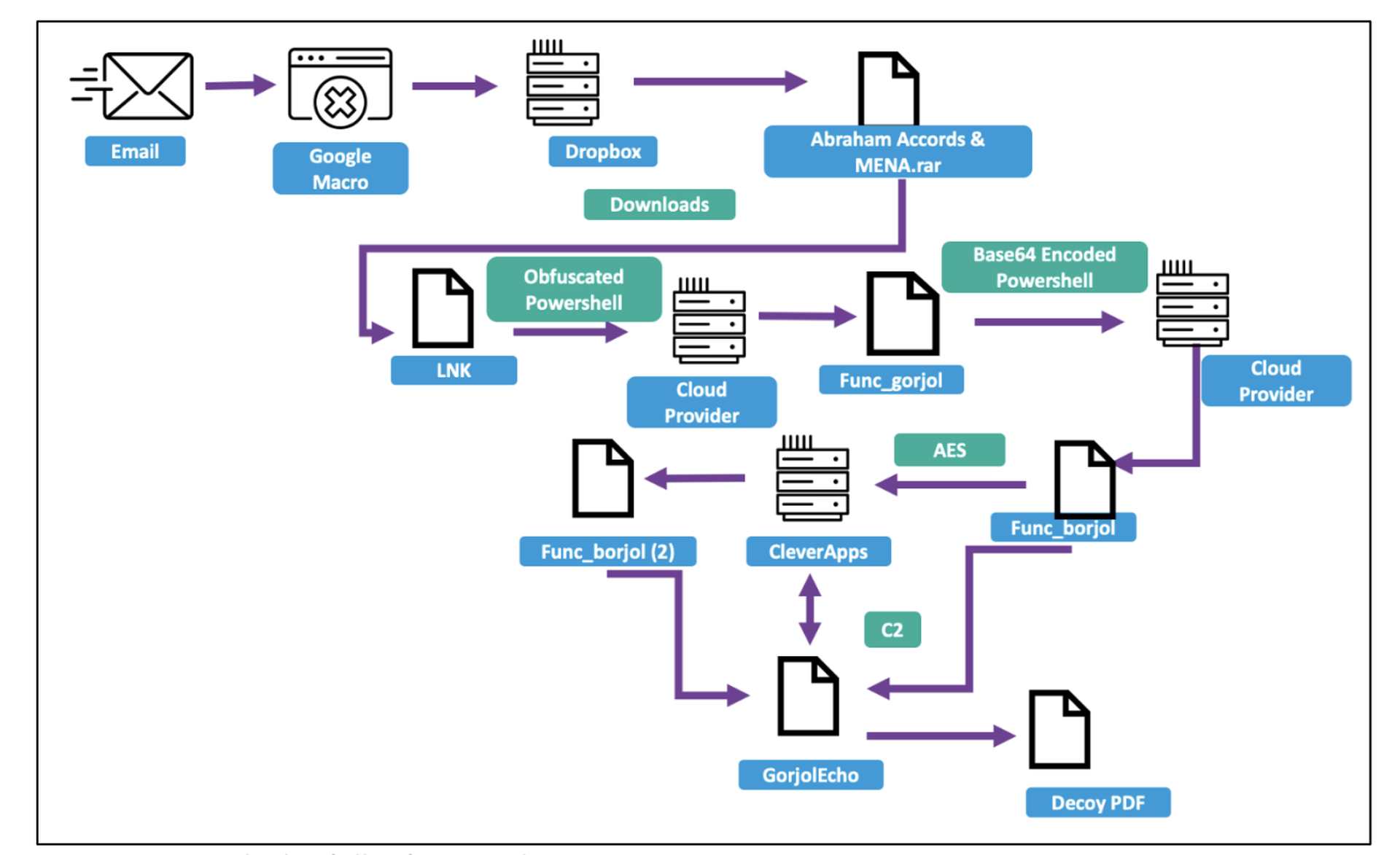
Full infection chain for GorjolEcho, one of the malware payloads deployed by Charming Kitten (Source: Proofpoint)
Joshua Miller, senior threat researcher at Proofpoint, told SC Media the campaign appears to be extremely targeted: thus far they are aware of fewer than 10 individuals who received phishing emails from the group. Miller said their visibility over the campaign is restricted to data and follow-ups culled from Proofpoint customers, and that none were successfully infected.
It’s not the first time Charming Kitten, which U.S. officials have linked to Iran's Islamic Revolutionary Guard Corps' intelligence organization, has targeted think tanks and other research institutions, seemingly in an effort to gather intelligence about Western foreign policy decision-making. While the group has targeted government officials in the past, they may find it easier to obtain some of the same information they’re looking for by targeting and compromising parties at the edge of those discussions.
“When we see them go after think tanks [and] academics, basically they’re informing the policy positions of the West and governments for nuclear sanctions or diplomatic policies. The idea is that that [while] they are trying to get…the official positions, they also want to get the thinking and deliberations behind that,” said Miller.
In one instance, the actor reached out several times in mid-May to a media relations contact for an unnamed U.S.-based think tank focused on foreign affairs.
The first email, purporting to be from Karl Roberts, a senior fellow and deputy director of terrorism and conflict at the Royal United Services Institute, asked for feedback on an Iranian-themed piece of research.
“We are studying security issues and working on a project called ‘Iran in the Global Security Context,’ which evaluates the impact of the Abraham Accords on Iran's regional role and MENA security now,” the actor wrote in a screenshot of an email provided by Proofpoint. “I've been making the rounds with a few experts about our new project. We've written a bit on this, and it would be, no question, our pleasure to have you read it.”
Shortly thereafter, that message was followed up by “Emily Winterbotham,” Roberts’ superior, who relayed that “Prof. Karl…informed me that he sent you the completed parts of the project and how to access the shared folder, but unfortunately, he has not received any response from you yet.”

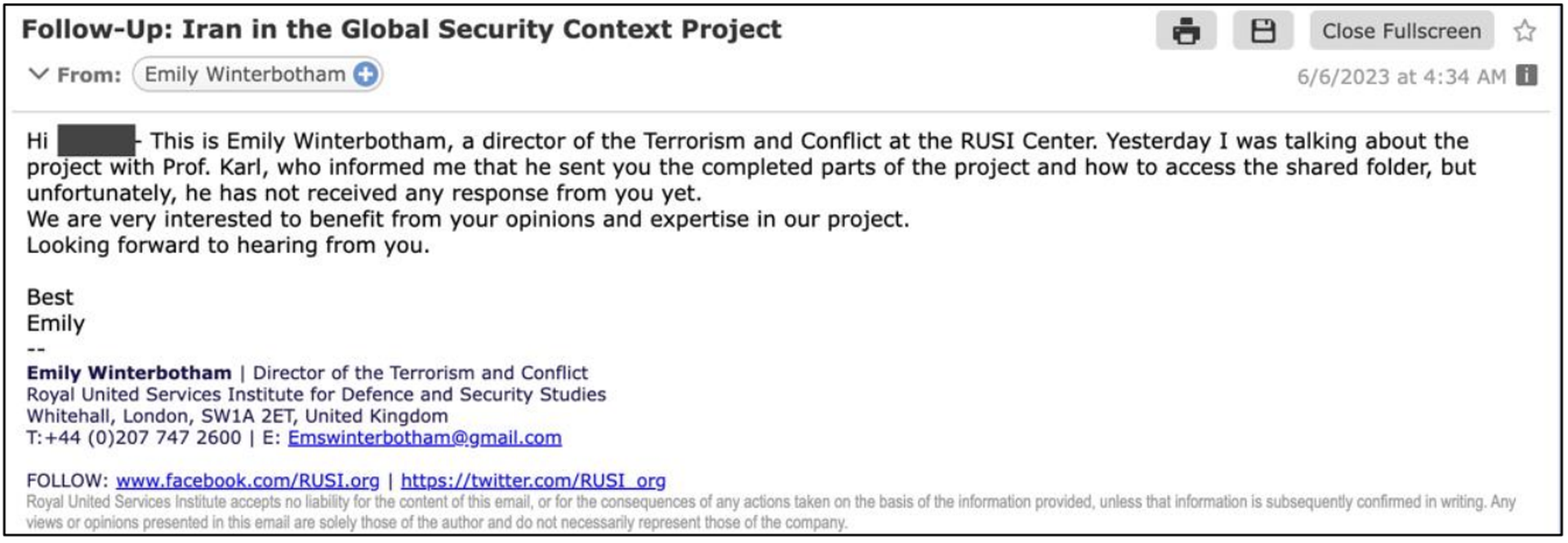
Charming Kitten actors send fake emails to targets pretending to be nuclear experts at the Royal United Services Institute. (Source: Proofpoint)
Anyone running a search on the internet would find that Roberts and Winterbotham are indeed real researchers employed at RUSI, but the emails were spoofed using other services like Gmail and Yahoo to trick victims into believing they were coming from the real experts. Miller said Proofpoint has contacted RUSI about the activity and also passed information along to the NGO Information Sharing and Analysis Center.
While Proofpoint has observed different variations of the backdoor used by Charming Kitten, this is the first time they’ve seen it used for Macintosh computers.
In at least one instance, the group ran the infection chain on a victim, only to realize their malware didn’t work on the employee’s Apple Mac computer. A week later, they reached out to the same victim again and re-ran the exercise, this time deploying Mac-compatible malware via a password protected Zip file pretending to be a RUSI-themed virtual private network program.
Miller said it offered a window into the level of effort Charming Kitten was throwing into the campaign by developing an entirely new infection chain just to reach one target.
“I think one week is a decently quick turnaround to go from a completely Windows-based PowerShell backdoor to a fully functional Mac backdoor [while] also setting up additional infrastructure,” he said.
Western think tanks and the research communities they support are increasingly the subject of hacking and phishing campaigns from nation state actors that seek to gain insight into the thinking or Washington policymakers and its allies.
North Korean hacking groups have attempted similar campaigns in recent years targeting think tanks for their foreign policy knowledge, while in 2018 Russian APT Fancy Bear — the same group U.S. officials accused of conducting a hack and leak campaign targeting the 2016 U.S. presidential election — was observed by Microsoft levying cyber attacks against think tanks like the Aspen Institute in Europe, the German Council on Foreign Relations and the German Marshall Fund in the months leading up to EU parliamentary elections.




