About this series
In 2023, the cybersecurity landscape changed in three significant ways. The Securities and Exchange Commission cut the allowed reporting period following a security breach to just four days. Artificial intelligence began to be used in cyberattacks. And after retreating in 2022, ransomware came back stronger than ever.
In response to these threats, cybersecurity buyers, vendors, influencers and decision makers worked to improve their practices around ransomware prevention, privacy and third-party risk, vulnerability management, cloud security, and identity and access management. Yet respondents in several CyberRisk Alliance Business Intelligence surveys reported more than a few challenges in meeting these goals.
The following is the third of a five-part series about how security practitioners struggled or, in some cases, made significant headway throughout 2023. Here, we focus on vulnerability management and what happens when you don’t patch flaws quickly – and why it’s often very hard to do so.
***
Vulnerabilities were not limited to third parties in 2023. Hundreds of organizations using MOVEit file-transfer software learned that the hard way when a zero-day flaw was disclosed May 31, along with a patch that MOVEit maker Progress Software had created in 48 hours.
The Cl0p ransomware group, which had earlier in the year targeted flaws in Fortra GoAnywhere MFT and PaperCut software, quickly exploited the patch lag among MOVEit customers. The group was apparently so successful with MOVEit that it abandoned its old business model and moved to old-fashioned blackmail without encrypting any data.
"They use the stolen files and information as leverage against the victims, with the threat of having customer PHI/PII or other details publicly published online being enough of a risk for organizations to pay," a Huntress researcher told SC Media.
Cl0p hit at least 369 MOVEit clients, including Siemens Energy, UCLA, U.S. government contractor Maximus and several U.S. government agencies. In June, MOVEit maker Progress Software was hit with the first of several class-action lawsuits, although its CEO later said most customers were "really happy" with the company's handling of the vulnerability. By November, Cl0p had moved on to targeting a zero-day flaw in SysAid servers.
Less well noticed were a clutch of severe software flaws in Microsoft Azure disclosed in January and March, and an exploited zero-day critical vulnerability in Cisco's IOS XE software in October that may have affected tens of thousands of networking devices.
Why it can be nearly impossible to patch in time
In an ideal world, all these flaws would have been patched immediately by software users. But the reality is that many organizations can't quickly fix even the most severe vulnerabilities due to legacy technology, incomplete inventory of assets, lack of a formal vulnerability-management program, or insufficient budget, staffing or support from management.
In an April 2023 survey carried out by CyberRisk Alliance Business Intelligence, only half of 210 IT and security professionals said their organizations' vulnerability-management programs had strong leadership support. Only 27% strongly felt that their VM programs had enough budget and dedicated personnel to do an effective job.
Vulnerability management resources
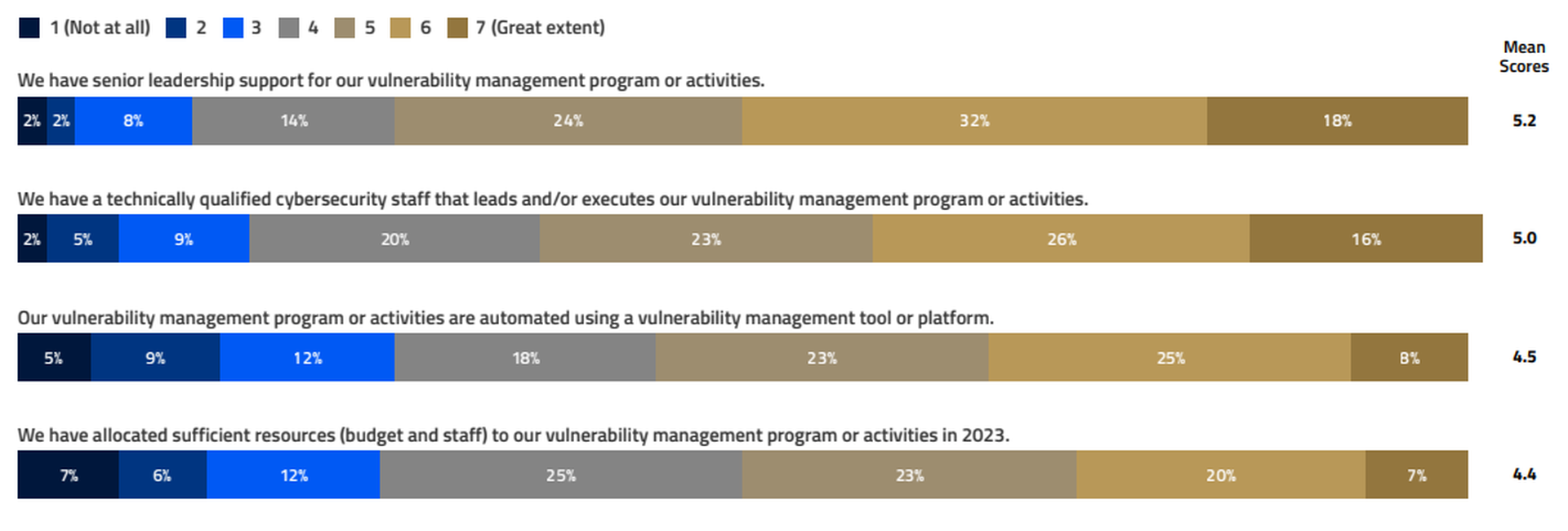
"We don't have the time, money or staff for these activities, and leadership is not supportive," said one survey respondent.
Likewise, only 36% of respondents strongly felt that their organizations had a complete inventory of IT assets, and only 34% believed that their VM programs had eliminated gaps that could be exploited.
Vulnerability management outcome or results
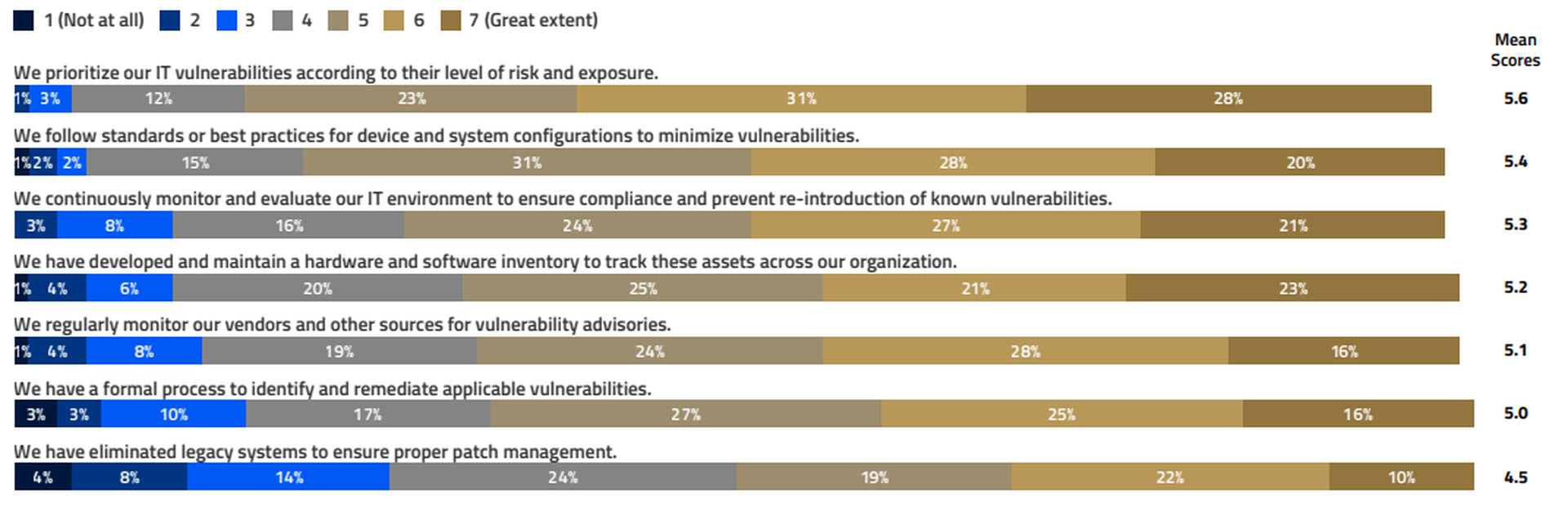
"Staying ahead of the constantly changing threat environment is by far the most difficult aspect of our cybersecurity management, even with the advanced tool set that we have," said a survey respondent.
In-depth interviews with a CISO and a CTO from two different organizations revealed concerns about legacy technology and automating vulnerability management, as well as how 2021's Log4j supply-chain vulnerability led to better planning about patch lag time.
"Where we're still struggling, and I think a lot of companies are struggling, is automating vulnerability management to pair up with the business value or materiality or context," the CISO noted.
But one of the interviewees added, "within any vulnerability management program — no matter how close you're automating — there's still a limit to how many changes engineering teams want to have to their production systems in a short period of time."
Vulnerability-management software should become more rapid and efficient as its automation is augmented by AI and machine learning. Yet those features may not be immediately affordable to security teams with limited budgets.
For in-house software development, AI is well suited to help detect vulnerabilities, such as in static or dynamic application-security testing (SAST and DAST). It is less reliable when writing code from scratch, and it often creates software vulnerabilities on its own.
It’s worth noting that the SEC’s recent fraud charges against SolarWinds involve vulnerability management. They allege that while SolarWinds portrayed itself as a security-minded company, it knew of internal risks and vulnerabilities that were not being properly addressed. Compliance with the SEC’s new four-day reporting rule would not have changed that perception.
2024 to-do list:
Includes guidance from the Cybersecurity Collaborative’s Task Force on vulnerability management.
- Look into vulnerability-management software that uses AI/ML.
- Incorporate AI and machine learning into application-security tools wherever possible.
- Develop procedures to apply critical software updates quickly. The Cl0p group exploited the MOVEit flaw just a couple of days after its disclosure.




