
Organizations respond to tangible losses with efforts to centralize security and ramp up partner collaboration
Large businesses experienced significant damage from breaches in the first quarter of the year, including data losses and system outages, which in turn spurred investment in centralized security strategies and improved coordination with external partners.
The findings emerged from a survey of more than 300 North American and European organizations, conducted in April, which was the basis of the fourth wave of the Cybersecurity Resource Allocation and Efficiency (CRAE) Index developed by CyberRisk Alliance Business Intelligence and underwritten by Ivanti.
Results showed both increased awareness of the threats targeting networks and data, as well as acknowledgement that ongoing efforts to better secure the IT infrastructure were not enough. Financial losses as well as operational downtown spurred many large businesses to better align internal resources and to tackle ongoing security efforts and create more holistic security strategies that integrate third-party partners and suppliers.
“Major breaches of data security have made the impact of the incident on our business devastating,” one respondent reported.
Increased threats produce more breaches and costly fallout
Amid the past year’s security challenges, organizations consistently reported improvement in their security capabilities. And yet, attackers kept pace. Half of all respondents said security threats had increased during the first quarter or 2021, with phishing the top threat (highest among large companies) followed by data exfiltration (highest in the high-tech sector).
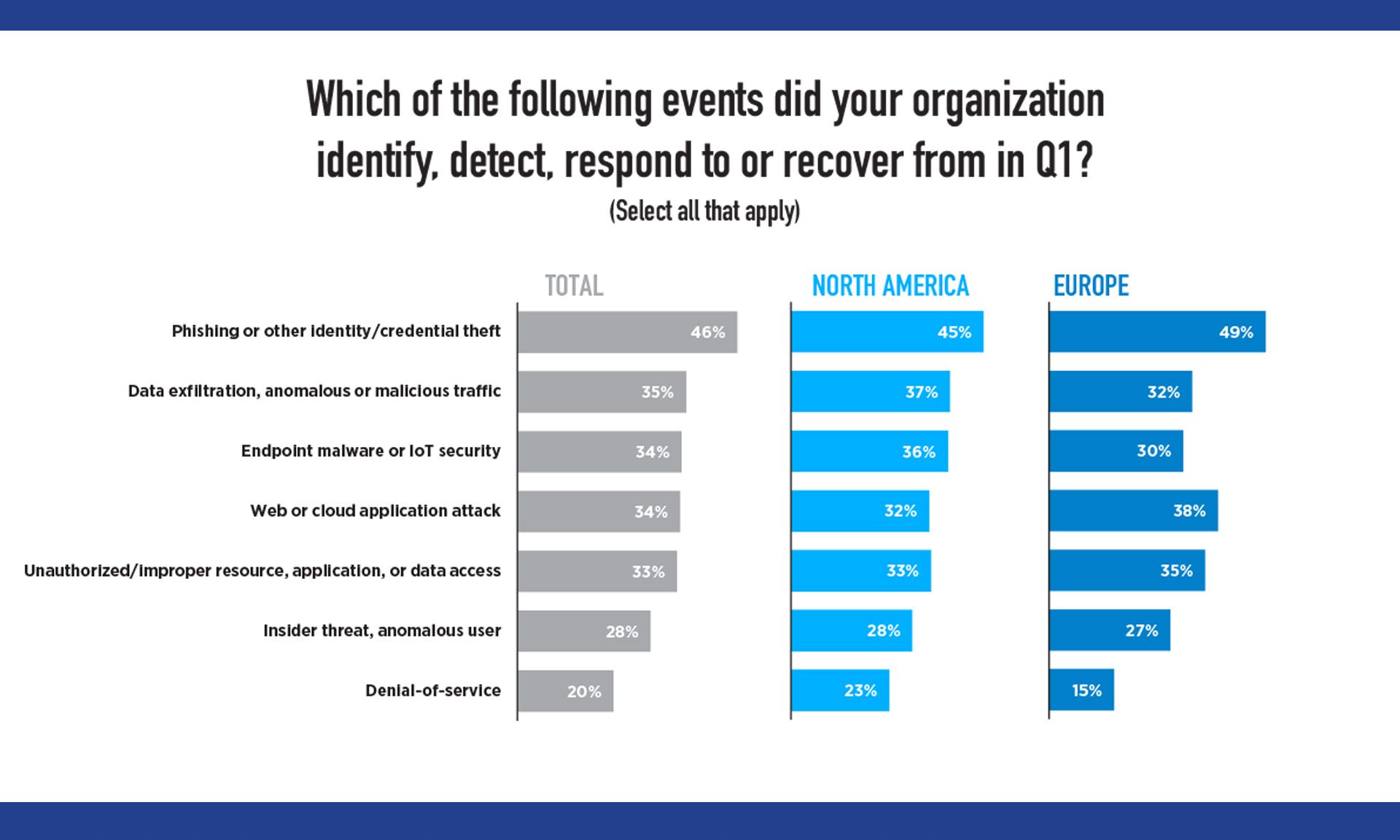
Specifically, 46% of organizations reported phishing as the top threat during the quarter, rising to 54% and 59% for financial services and manufacturing, respectively. But attack tactics are diverse, with 30% or more of organizations also reporting:
- Data exfiltration, anomalous or malicious traffic
- Endpoint malware or IoT security
- Unauthorized or improper resource, application or data access
- Web or cloud application attack
Attacks that succeeded in stealing data, disrupting systems, or nabbing a ransom payment served as a reality check among cybersecurity practitioners, many of whom simultaneously reported confidence in their ability to detect and respond to security events. And much like the threats themselves, consequences of attacks are varied and potentially long-lasting, according to respondents that were victims.
Among the specific incidents noted by respondents were a cyberattack that resulted in “a breach of company data and the theft of important information,” a ransomware attack that forced the organization “to pay a substantial amount of money,” a cyber threat that led to a “blackout of electrical equipment," and a large-scale system hack that shut down operations for half the organization for a day.
In some cases, respondents claimed to still be recovering from the incidents.
Organizations shift to centralized security strategy
With losses fresh, organizations recognize that product investments and employee training are only part of the solution. They also need a holistic security strategy, uniting stakeholders to monitor and coordinate infrastructure, policy, best practices and communication. This may take the form of an internal “center of excellence” that helps to develop, implement and fine-tune strategies and structure.
In some cases, a push for centralized coordination is driven by the need to provide reassurance to customers about cybersecurity concerns, particularly in the wake of an attack. Formation of a center of excellence demonstrates a commitment to best practices and to strong security management — a powerful message both internally and externally.
“We had a security breach, which was bad for our name and reputation as a company, so it drove us to invest more in cybersecurity to stand firm and protected.”
U.S.-based cybersecurity professional
Centers of excellence also minimize communication breakdowns, which one respondent identified as a contributing factor to a recent incident: “A lack of clear communication between several departments caused some minor security risks due to the fact that no clear direction was conceived from the outset.”
Distributed workforces made centralized coordination and communication even more critical, a challenge cited by several respondents. When security incidents did occur, 50% of organizations increased their coordination of communications during recovery activities, with 47% maintaining their level of coordination.
In addition to creating formal centers of excellence, more than half of respondents increased their resource allocation to develop or modify a risk management strategy (52%) and to develop or modify a cybersecurity policy or governance program (53%). These investments complement increased allocations for employee training, process improvement and technology solutions.
Respondents also display a continuous improvement mindset when it comes to security. More than half (54%) will invest more resources to collect and analyze data related to security incidents, and 52% will increase resources to identify and implement lessons learned after an attack.
External partners pose distinct security challenges and opportunities
In addition to building more substantial internal structures, organizations also are looking outward. There is a growing recognition that external partners are an important consideration in risk mitigation — as both allies and potential points of exposure. For some respondents, managed services became the strategy of choice, with the added benefit of a predictable cost structure.

Download the full index report for a detailed breakdown
External support may be even more critical for companies with reduced IT staffs, a challenge cited by multiple respondents. “Our cybersecurity activities have been significantly affected by the lack of critical technical personnel,” one respondent said.
Equally pressing is the need to improve security in relation to external vendors, suppliers and other partners. Asked to identify factors affecting the ability to detect and respond to cyber threats, one respondent said “third-party vendor interactions and services [and] cloud security for existing implementations.”
Many organizations know they need better assurance of partners’ cybersecurity protections, but are unsure how to assess and manage these potential vulnerabilities. Although due diligence may be practiced at the start of an engagement, maintaining long-term confidence and visibility in partners’ extended networks is a challenge. Cloud services, in particular, can be difficult for organizations to manage from a security perspective.
As they strive to mitigate these risks, 47% of organizations are increasing their coordination of incident response with external parties, including customers and vendors. On the other hand, 48% of organizations are maintaining their level of coordination. Similar percentages are in place for organizations’ coordination of incident recovery with external parties.
For more information on how you can partner with CRA Business Intelligence, please contact Dave Kaye, Chief Revenue Officer.



