After falling victim to two confirmed cyberattacks, and a possible third, since 2019, Carnival Corporation & plc has experts suggesting that the cruise operator – already imperiled by COVID-19’s impact on the travel industry – may need to institute major reforms to its security program and policies before suffering further damage to its reputation.
Earlier this week, the $20.8 billion corporation acknowledged in a news release and an 8-K filing with the Securities and Exchange Commission that one of its cruise brands suffered an Aug. 15 ransomware attack during which the threat actors “accessed and encrypted a portion of one [cruise liner] brand’s information technology systems” and also exfiltrated sensitive customer information – potentially for extortion purposes. The disclosure came just months after the company separately announced last March that its Princess and Holland Cruise Line operations in 2019 experienced a malicious data breach stemming from a phishing campaign.
To compound matters, cyber intelligence company Prevailion is now claiming that it saw evidence of a network compromise and malware infection at Carnival for a period spanning from Feb. 2 through June 6, 2020, and attempted to alert the company, but never received a response back. The intrusion theoretically could be tied to the just-acknowledged ransomware attack – though the time frames of both events don’t appear to sync up – or it could be its own separate incident.
Any company can potentially be breached, but this convergence of troubling news over the last few months has caused some cyber experts and observers to come down hard on the organization.
Cybersecurity intelligence firm Bad Packets told BleepingComputer that the attack was “not surprising given they had multiple Citrix servers” that were vulnerable to exploits that could allow a ransomware operator to gain access to the network.
“This is another case of a company not taking the steps to properly defend their networks against the bad actors of the world,” said Chris Hauk, consumer privacy champion at Pixel Privacy. “…Carnival failed to patch its edge gateway devices and firewalls, even though patches have been available to fix both issues since earlier this year.”
“As for Carnival customers, they will need to keep their eyes open for phishing attempts and other attacks designed to separate them from their personal information and hard-earned money,” Hauk continued, “as bad actors may attempt to take advantage of the data gleaned from this attack and the data breach that occurred earlier this year.”
"Any organization that is not equipped to locate and patch vulnerable systems in under a week is at significant risk of compromise from organized hacking groups,” said Chris Clements, VP of solutions architecture at Cerberus Sentinel. “Once the network perimeter is breached, it can take skilled hackers little more than a few hours to gain complete control of the victim’s internal network and deploy their ransomware.
“Carnival states that they detected the ransomware attack on Aug. 15, but it’s likely that the attackers had access to their network and data for weeks or months prior searching and exfiltrating any sensitive data they could find,” Clements added.
Case in point: the systems breach that Prevailion detected apparently went on for a little over four months. During that time, the malware beaconed to a command-and-control server roughly 46,000 times, with the peak of activity taking place between April 11 and June 6, the company reported in a blog post.
In an interview with SC Media, Prevailion CEO Karim Hijazi said his company regularly monitors for command-and-control activity over the internet. Carnival’s March 2020 disclosure of the initial breach prompted Prevailion to sort through its data related to Carnival. In so doing, analysts discovered malicious program residing on Carnival’s network actively beaconing to an attacker's C2 infrastructure. Hijazi said that after Prevailion's efforts to warn Carnival went unanswered, his company decided to come forward with its findings once news broke of the latest ransomware incident.
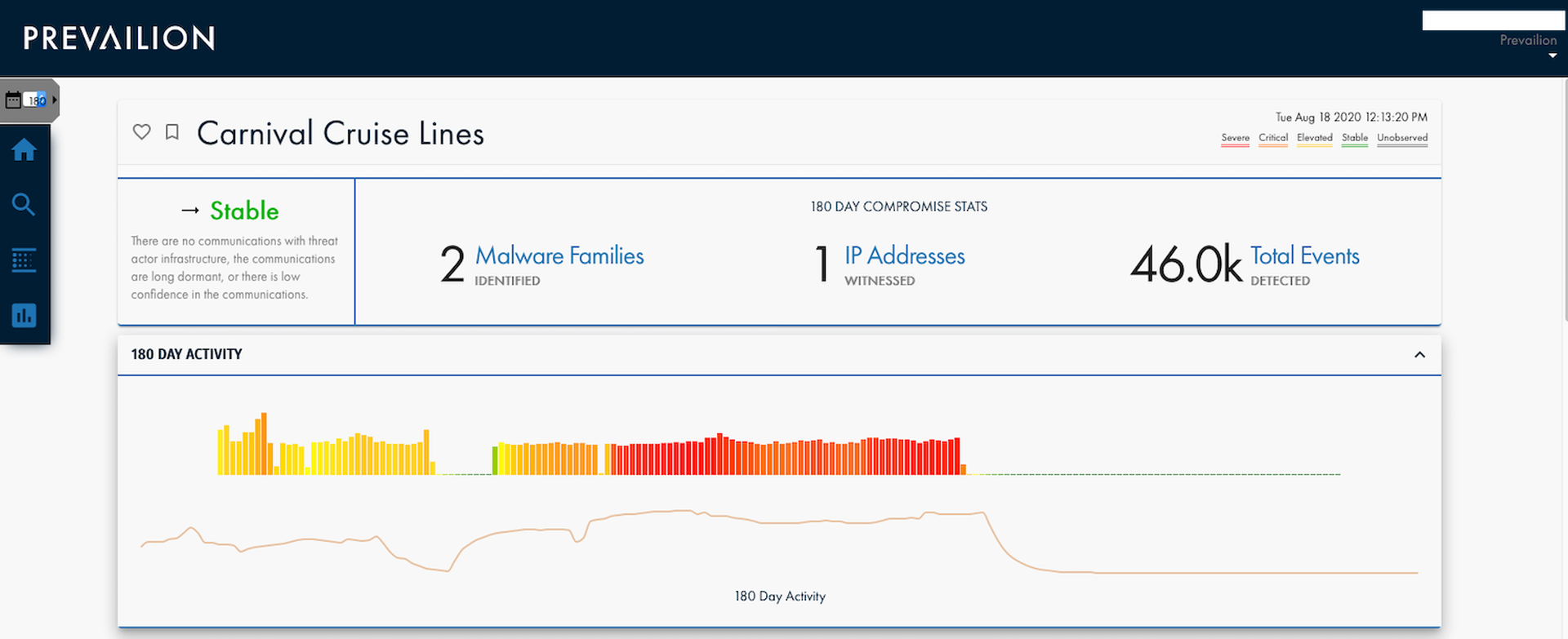
The malware activity Prevailion spotted appeared to be the work of a trojan with C2 communication capabilities allowing for possible data exfiltration or delivery of payloads and updates – including perhaps ransomware, Hijazi told SC Media.
“This is an organization that needs to really, really take a deep hard look at their, their protocols,” said Hijazi. “We're able to see the systemic success or failure of the organization over time. And the fact that they don't seem to be managing or remediating, the problems they have in a timely matter."
“We're not blaming organizations… for getting compromised or breached, because it happens – even the best effective ones still fall victim to this kind of thing. What is unfortunate is the dwell time and the length of time that the malware was able to reside within that organization."
“It is a disappointing situation to see an organization that is harboring and holding information of people who trust them with that data, lose [that data], and then continue to have that failure happen," Hijazi continued. “While there's no perfect cure or panacea to the problem, good practice and protocol with addressing the problem is key. It doesn't appear that they even have knowledge of some of these compromises happening to them. If they did you would have, we would assume we would see the beaconing desist, and it [did] not.”
At least, not until June 7, when the beacon activity suddenly stopped. It would seem like that would mean there is no connection with the ransomware attack that occurred more than two months later. But not necessarily -- Prevailion said that while the compromise might have been remediated, the malware also simply may have gone temporarily silent.
"We're seeing a lot of malware that will go dormant, and then come back to life. So it'll evade detection," said Hijazi. Security teams or incident response teams "assume it's cleaned up, they'll leave, and... then the dorsal fin will come back out of the water, and it'll resurge or it'll reinfect."
Regardless of whether or not the incidents are connected, the latest attack will carry ramifications, which will only be exacerbated by the combined effects of the previous incidents. But how severe will the consequences be? For its part, Carnival said in its 8-K filing that it “does not believe the incident will have a material impact on its business, operations or financial results.”
However, “we expect that the security event included unauthorized access to personal data of guests and employees, which may result in potential claims from guests, employees, shareholders or regulatory agencies,” Carnival stated. And unfortunately for breach organizations, that still counts toward the bottom line.

“The repercussions of a cyberattack now extend far beyond data loss and ransom payments – operational downtime, reputational damage, and the cost of installing new systems can cripple businesses, so yes, attacks have the potential to lead to significant damage, financially, operationally, and of course reputationally,” said Justin Fier, director of cyber intelligence and analysis at Darktrace.
With that said, Fier believed Carnival dodged a bullet, noting that the damage would have been far worse if the encryption attack had disrupted operations – something that’s not really possible right now with cruise ships largely docked during the pandemic.
“Today, we are seeing consumers’ opinions of an organization much more affected by operational downtime due to a cyberattack rather than compromised personal data,” explained Fier, noting that ultimately “I do not think this breach will impact who consumers travel with.”
“Still, it’s troubling for the travel industry as a whole,” he added. “The travel industry is struggling financially amidst the ongoing pandemic, which may lead to budgets for security being cut. In today’s technology-dependent world, cybersecurity is crucial to an organization’s survival and must remain a top priority.”
In fact, Proofpoint just released a report on the travel industry, noting that of the 296 airlines that are members of the International Air Transport Association (IATA), 61 percent lack a published DMARC (Domain-based Message Authentication, Reporting & Conformance) record, which makes the potentially more vulnerable to email spoofing scams. And 93 percent lacked the most secure and recommended DMARC policy, “Reject.”
So far, it doesn’t appear that the stolen data has been leaked, but Erich Kron, security awareness advocate at KnowBe4, said that doesn’t mean the information won’t wind up for sale on the dark web.
“Carnival is understandably withholding statements at this time as they work to find out the extent of the incident and the potential impact to customers or the organization, a process that does take time," said Kron. "I am hopeful that Carnival will share the information discovered during the investigation, even if it is through an anonymous data sharing entity, in order to help other organizations protect themselves from these types of attacks."
SC Media reached out to Carnival, which had no comment. However, in its 8-K filing, the company said that it “has implemented a series of containment and remediation measures to address this situation and reinforce the security of its information technology systems.”
Experts had their own ideas of what the company could do to improve its cyber standing in the future.
“The first thing is to do a really good assessment of exactly where things have failed," said Hijazi. What exactly is the organizational structure here? Is there a central understanding of how security should be mandated across the entire brand ecosystem? And if not, get that."
It's a little bit more of a change management effort at this point -- if it's indeed a failure on the security teams front versus a cyber problem," Hijazi continued. "I think more and more we hear about how cyber is really more of a business issue, not just a cyber issue... So I think the first thing is a deep assessment of where things have failed. Second is to start working toward a continuous monitoring an understanding of what's going on, rather than a postmortem approach to the problem. [And] understanding what's happening in a third-party ecosystem and a partner ecosystem."
Clements from Cerberus Sentinel added: "Organizations seeking to protect themselves from ransomware attacks must adopt a culture of security that includes regularly scanning for serious security holes and patching within a week’s time, ensuring that internal controls and monitoring exist to quickly detect and limit a potential attacker’s access, and ensuring that any recovery operations are effective at a mass scale."




