The cybersecurity community paid close attention to ransomware actors’ escalation of business tactics in the last year, including double extortion, forming cartels and contacting individual victims directly.
But one must not overlook some of the newer tools and technical strategies that these adversaries recently added to their repertoires in order to hinder and complicate forensic investigations. A panel of IT experts discussed some of these latest challenges in a ransomware session held last week at the 2021 Incident Response Forum Masterclass.
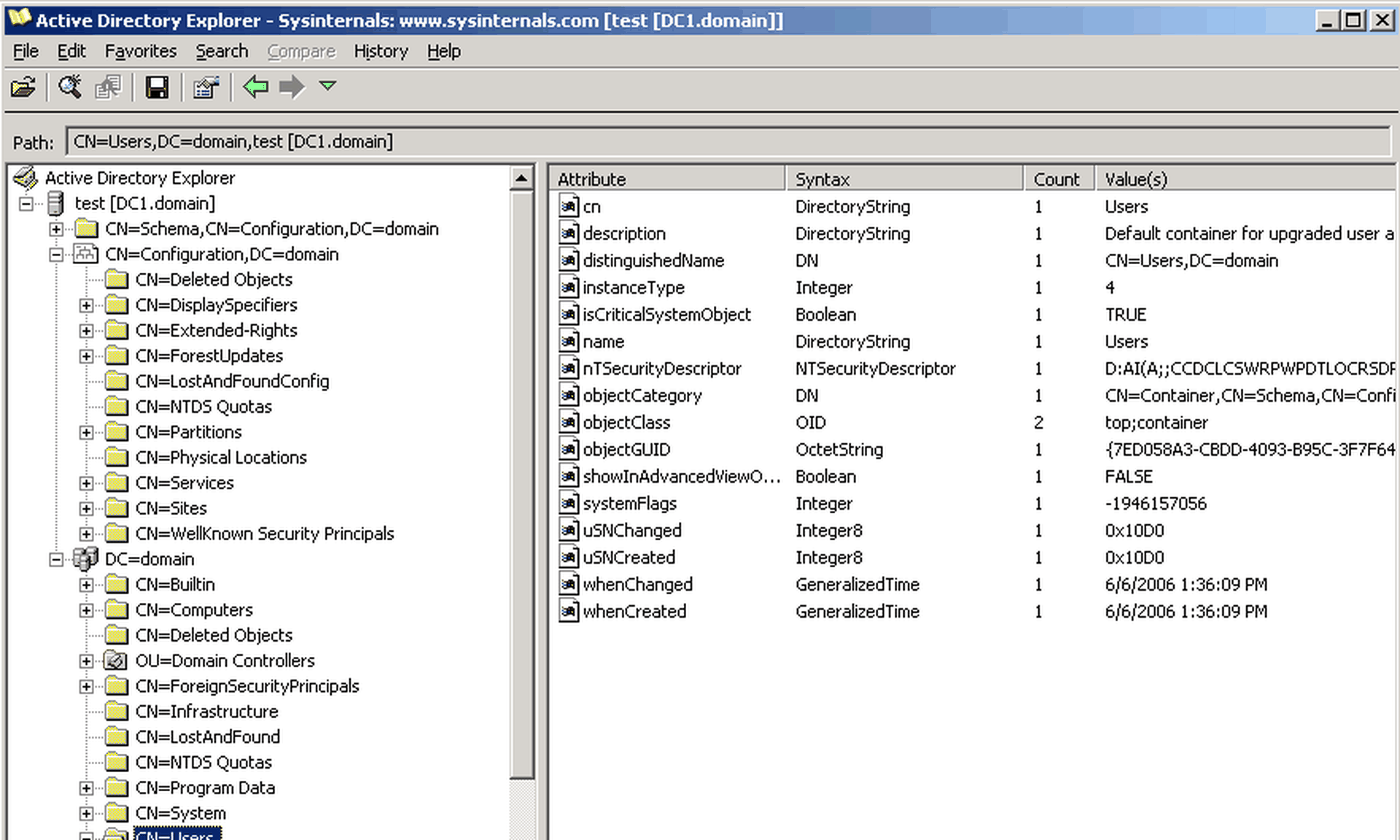
For instance, Aravind Swaminathan, partner at the law firm Orrick, noted an uptick in sophisticated ransomware intrusions where the Active Directory is compromised, which “makes the investigations not only more complicated but also take a lot longer period of time, because they have oftentimes been spending… long periods in the environment looking at a lot of different multiple systems.”
And in situations where the Active Directory and domain controller are set up on a virtual machine, the attackers are holistically encrypting the VM environment, noted Bret Padres, group vice president with Crypsis, a Palo Alto company.
This gives the adversaries an upper hand, he added, because it further slows down forensic analysis, which would normally be transpiring even as negotiations with the actors are taking place. “This stalls us a little bit because we have to wait ’til we get the decryption key to be able to determine what forensic evidence is on that domain controller,” he said.
Another problem is malicious’ actors adoption of Rclone, a legitimate, open-source, command line-based file synching tool that businesses often use to back up assets to the cloud. “Whereas before we saw a lot of FileZilla, Megaupload and those types of things, Rclone [now] is being used. And it does make forensics a little bit more difficult,” including looking for and identifying indicators of compromise, said Padres.
Experts at SpearTip last year reported that Rclone was emerging as a new tool for data exfiltration in ransomware attacks. SentinelOne reported that presumed Maze ransomware successor Egregor leverages Rclone as well.
The use of Rclone, said Swaminathan, makes “understanding what data was actually exfiltrated… even trickier, largely because if you look at the way Rclone works and the threading that it that it applies, it's really difficult to map what data they actually got access to or acquired… And so that actually has been a huge stumbling block in our investigation[s].”
With that said, Padres noted that negotiations with the hackers will often reveal to you what they stole. (It’s just up to the organization what to believe.) “If you ask them, ‘What data did you take?’ they're sharing directory listings or in some cases they're even making that data available to the victim, to be able to say, ‘Okay, here's a copy of your data; you can log in and look at it if you want,’” Padres said.
Kari Rollins, partner at Sheppard Mullin, also noted that attackers have been aggregating data from multiple sources, making it difficult for investigators to pinpoint precisely which systems, and how many data sources, the perpetrators were able to compromise and access. “I think that complicates the factors, and the risk and the decision-making when you have to assess whether you have an obligation to notify,” she said.