Implementing an extended detection and response (XDR) solution can be a force multiplier for security staff already stretched thin by the pandemic, the move to remote working and the resulting expansion of a threat landscape that’s increasingly difficult to read. But for a market juggling an onslaught of tools to manage incident response, lack of clarity about XDR benefits and implementation remains a challenge.
Data proves that point: only 12% of respondents in a recent CyberRisk Alliance (CRA) survey of 300 security professionals said they were using XDR. And yet, a whopping 77% did say that they planned to implement it within the next 24 months to deal with current problems around visibility.

Outside of the CRA survey, there is some skepticism about the usefulness of XDR. A recent Gartner report said XDR would best benefit smaller operations that did not have full-fledged security information and event management (SIEM) or security orchestration automation and response (SOAR) solutions in place.
Cisco is more bullish on XDR, but in a recent report of its own, the company stressed that XDR is not a turn-key solution. XDR must be integrated with other security tools, Cisco said, including SIEM and/or SOAR, to provide the data XDR needs and to make up for what XDR does not cover.
What is XDR?
XDR can be seen as the logical evolution of endpoint detection and response (EDR), which generally analyzes data from a single endpoint at a time and launches investigations into possible security events on those endpoints. EDR can be very useful, but it often doesn't provide the whole picture.
As a SANS white paper from 2019 pointed out, a traditional EDR system would likely miss a password-spraying attack that targeted multiple systems and accounts with a single set of credentials one by one. Without the holistic overview provided by a SIEM or an XDR system that showed the same attack occurring across multiple systems, the individual pings on EDR systems might be ignored.
What XDR does is look at the entire system — endpoints, networks, software, firewalls — by gathering data from front-end security tools such as EDR, identity access management (IAM) and network detection and response (NDR). It can also sift through SIEM logs and present that data as well.
An XDR solution will contextualize and correlate the data received from all these sources and present it to security teams in the form of a dashboard or other quickly digestible format. XDR will also carry out a lot of the low-level security tasks and investigations that might otherwise be carried out by human personnel, freeing up those staffers to attend to more urgent tasks.
Core XDR functions, as defined by Cisco, are flexible integration with existing security tools; a centralized display or presentation that lets users see everything important at once; machine-learning functions that can automate simple analysis; and automation of simple tasks.
As the CRA report "XDR Poised to Become a Force Multiplier for Threat Detection" states, XDR solutions "are designed to give organizations the needed visibility to root out adversarial threats without disrupting users or invoking alert fatigue.
"This allows security teams more time to perform solid investigations and improve their threat response posture whether an attack comes through a network, endpoint, email, or the cloud."
What XDR is not: SIEM, SOAR, EDR, NDR
It's important to understand that XDR does not replace SIEM, SOAR, NDR, EDR or other security solutions that your organization may already have in place — or may put into place in the future.
Rather, XDR gathers telemetry from and alongside those tools to give you a more complete picture of everything that's going on in your systems so that you can identify and remediate threats more quickly.
"XDR isn't a bully who has come to steal your SIEM's lunch money," said Cisco. "It's a platform that plays nice with many security tools you're already using."
Various efforts are underway to help guide organizations in potential XDR implementation in conjunction with existing tools. In August 2021, for example, came the launch of the XDR Alliance — an organization formed to create a uniform framework and architecture for XDR. Two months later CrowdStrike announced a separate coalition of cyber, SaaS and IT solution providers with the shared goal of creating a "shared schema" for XDR data exchange, while providing users with an XDR platform that features a variety of integrated solutions.
Benefits of XDR
This bigger picture can be of immense value to security teams that worry they've been missing things. In fact, nearly half — 47% — of the respondents in the CRA survey said that they had missed at least one threat in the past 12 months due to lack of visibility. Only 17% said they were very satisfied with what their existing security solutions could deliver.
Many respondents indicated that they had low visibility into employee-owned endpoints, software vendors and third-party partners. These three categories were ranked last in terms of items that security practitioners said they could "see" with their existing tools. An XDR solution coupled with a SIEM could provide greater insight into those categories.
As indicated above, XDR also does a lot of the "grunt work" in correlating, contextualizing and even investigating what may appear to be routine security events. That can be a great benefit to security teams that may be understaffed or overworked, providing those teams more time to deal with more important issues.
"We are so shorthanded that tasks are sometimes not carried through with the same level of care," one respondent in the CRA survey said. An XDR solution would act as a force multiplier and help relieve that burden. XDR can also help separate true threats from background noise. The sheer amount of log data generated by a SIEM tool or another security tool can be overwhelming.
"Too many tools are not identifying the real threats but are identifying false threats," said one respondent to the CRA survey. Some 35% of respondents said it would take their security teams at least 24 hours, and possibly as long as six months, to detect and identity true cyberthreats.
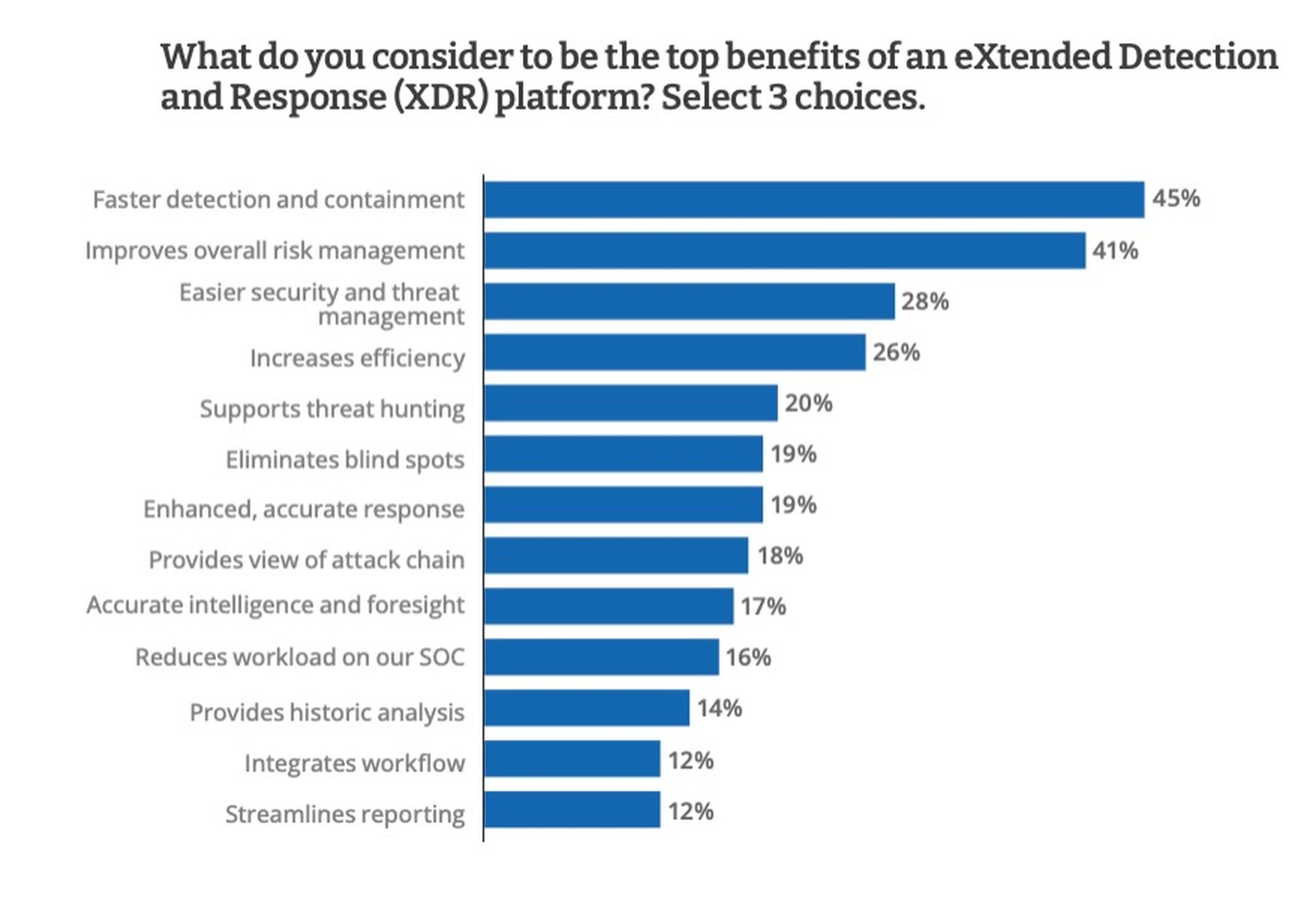
But XDR can do a lot of the processing for you, correlating disparate events to give you greater and more rapid insight into the real threats.
"We made the decision to implement XDR after a data breach, and I think it was the right call," one survey respondent told CRA. "Our organization is more secure than ever."
Drawbacks of XDR
This does not mean that XDR is ideal for all organizations. Gartner’s report from November 2021 was notably skeptical about the value of XDR when compared to more established solutions, especially for larger organizations.
"XDR is expected to see the biggest initial adoption by smaller security organizations that likely don't have security information and event management (SIEM)/security orchestration automation and response (SOAR) solutions in place today," said the Gartner report. "No XDRs currently meet the full needs of mature large enterprise security operations because XDR will not displace SIEM functionality for all use cases."
Instead, Gartner said, XDR "will appeal to pragmatic security leaders that do not have the resources to integrate a large portfolio of best-of-breed security products and/or struggle to get full value from SIEM and SOAR tools."
Gartner also worries that some solutions presented as XDR may not in fact include the core XDR functions: integration with other security tools, dashboard presentations, automated analysis and automated tasks.
"By 2023, at least 30% of EDR and SIEM providers will claim to provide XDR, despite them lacking core XDR functionality," the Gartner report foresees. "We recommend that security leaders hold XDR vendors to a high standard on their claims."
Yet overall, Gartner agrees that XDR can tremendously benefit smaller security teams and indeed be a force multiplier for such organizations.
"XDRs are further refining technology to be more integrated and comprehensive within a provider's converging platform offerings," said the Gartner report. "This means that smaller teams in security operations can run fewer tools that do more in one console, which is a key value proposition for XDR for security teams of this size."
Implementation: Open or closed XDR?
If your organization chooses to go forward with XDR, the next decision will be whether to integrate the XDR solution with your existing security tools or to instead "rip and replace" those tools so that all your security solutions end up coming from a single vendor.
Broadly speaking, there are two types of XDR implementation. "Open" or "hybrid" (although not open-source) XDR solutions work with security tools from dozens of different vendors and have built-in APIs for easy integration. Some of the best-known "open" XDR tools come from Exabeam, Netskope and VMWare.
"Closed" or "native" XDR works only with those security tools from a single, usually major, vendor. Cisco, Microsoft and Palo Alto Networks (the latter of which coined the term XDR in 2018) are among the top providers of closed XDR solutions.
If your organization already gets all or most of its security tools from a single vendor, and you're happy with what that vendor provides, then going with that vendor's closed XDR solution would be a no-brainer.
However, if your existing tools come from several different vendors, and you feel that those tools are indeed best-of-breed, then it would be best to choose a "open" solution that works well with all those different tools. This hybrid approach would also let you replace individual front-end tools in the future without having to overhaul everything that feeds into your XDR solution.
Both these scenarios assume that you are already happy with the tools you've got, whether it comes from a single vendor or multiple vendors, and you just want an XDR solution to gain more insight into what your existing tools gather.
But if that's not the case, and you're not satisfied with the solutions you have now, then it might be worth replacing them all with a single-vendor slate of tools as part of a package deal that includes an XDR tool. That approach may end up costing less overall, although it also would give you less flexibility to mix-and-match tools in case a better individual EDR, IAM or NDR tool comes along later.
In the CRA survey, 43% of respondents considered the flexibility to choose best-of-breed tools to be a top benefit of an open XDR infrastructure, while only 30% said the same about closed XDR. By smaller margins, open XDR was also perceived to have the advantage over closed XDR in terms of deployment (50% vs. 43%), price (48% vs. 44%) and the skills needed to operate (48% vs. 45%).
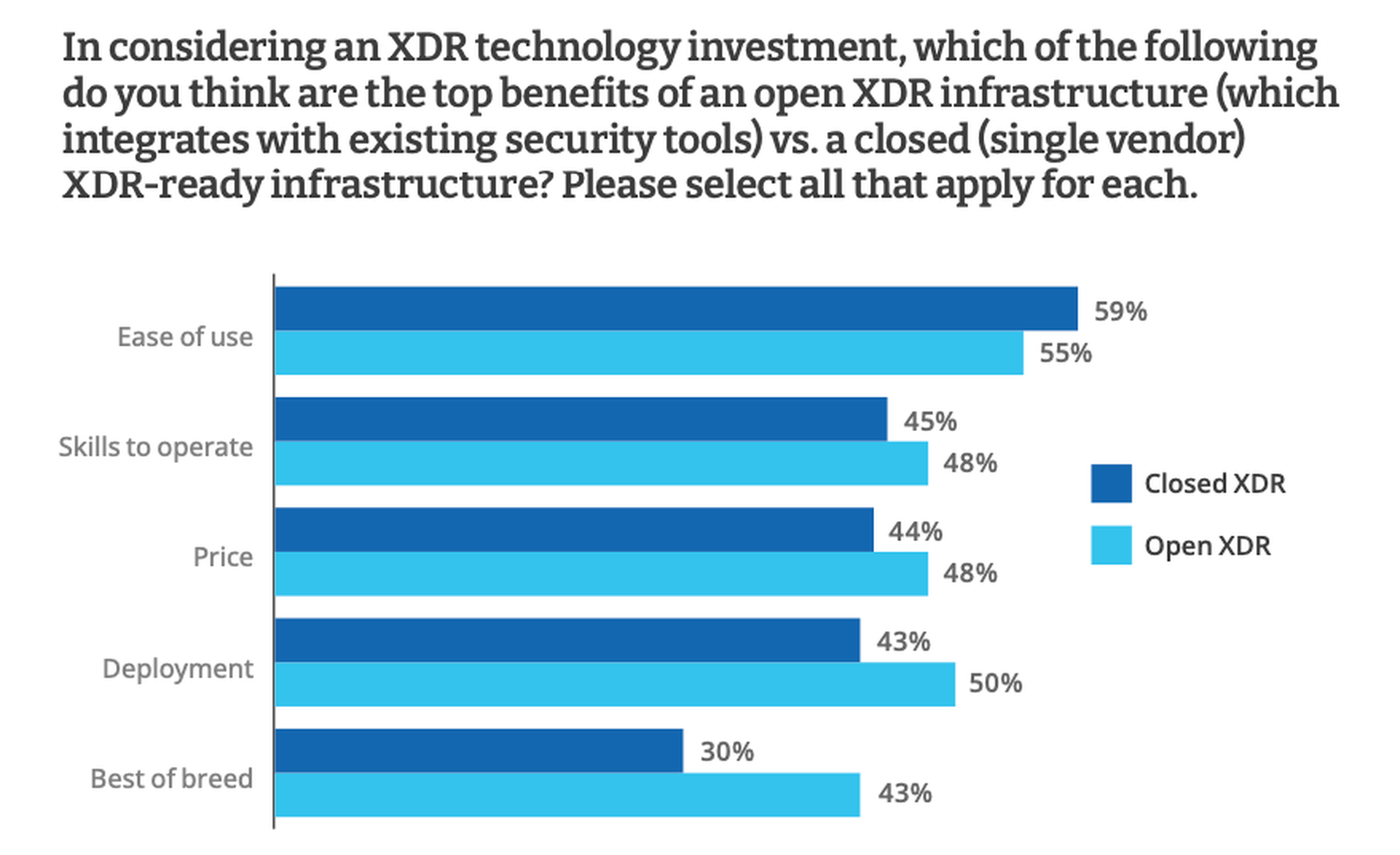
However, 59% of respondents considered ease-of-use to a be chief selling point of closed XDR. And 55% also said the same about open XDR, indicating that ease-of-use is a key appeal of XDR system no matter the type of implementation.
Whatever the pros, cons and different implementation options of XDR solutions, few of the survey respondents who had already rolled out XDR in their organizations had regrets.
"It runs smoothly with other software we are using and catches almost every threat and issue," said one respondent. "It is easy to deploy, easy to update, can make changes as needed quickly, and our employees are able to get up to speed quickly."



