To help organizations better conduct risk assessments, the Cybersecurity Collaborative (CSC), a division of CyberRisk Alliance, has created a guide to cybersecurity-based risk-assessment best practices and introduced what it calls the CSC Risk Assessment Maturity Model.
"Risk assessments are a foundational part of every cybersecurity program," states the guide. "Comprising three tiers and nine components, the CSC Risk Assessment Maturity Model is a tool for CISOs to make risk assessments an effective part of the cybersecurity program."
Origins of the risk-assessment guide
The genesis of the risk-assessment guide, formally titled "Risk Assessments: Best Practices Guidance Document 2023," lies with a task force created by the Cybersecurity Collaborative in February 2023.
"Challenges with using industry-based methodologies, like ISO 27005, NIST SP 800-30, and FAIR, motivated members to collaborate on finding the most effective strategies for selecting a methodology and successfully engaging management and stakeholders in risk assessment and decision-making processes," the finished guide states in its introduction.
The Cybersecurity Collaborative is an organization of CISOs and other cybersecurity managers and executives to provide mutual support, services, tools and other resources, both to enterprise-level security teams and to teams in smaller organizations.
Twenty CSC members shared their own risk-assessment documents and processes and participated in weekly meetings to help shape this risk-assessment best-practices guide, which is an example of the CSC's resource offerings. (To read the entire document, log into your CSC member account or apply to become a member at https://www.cyberleadersunite.com/contact-us.)
Challenges to conducting risk assessments
Managing risk and meeting compliance requirements are a large part of enterprise governance, and one of the most significant categories of organizational risk is cybersecurity.
"Entities are often obligated to perform risk assessments by customer contracts, government and business regulations, and security standards," the CSC risk-assessment guide observes.
Many industry regulations, standards and frameworks require periodic risk assessments, the guide points out. These include HIPAA (the Health Insurance Portability and Accountability Act of 1996), ISO 27001 (2022 revision), PCI-DSS (the Payment Card Industry Data Security Standard) v4.0, SOC 2 (System and Organization Controls Trust Services Criteria) and various state laws such as Regulation 203 of New York state's Department of Financial Services.
However, conducting assessments can be complex, confusing, and time-consuming. The CSC guide lists conflicts among stakeholders, the difficulty of selecting and structuring methodologies, and reluctance on the part of management to accept results or to make decisions as common challenges facing organizations that are beginning the process of risk assessment.
Establishing commonalities and definitions
To provide a firm foundation on which to launch a successful risk-assessment program, the guide notes, it's necessary to agree upon a common set of components and definitions.
The guide presents a table listing a dozen common terms and definitions, such as "Assets," "Event" and "Risk Value."
For example, risk value is defined as "the calculation of likelihood x impact. This can be expressed in qualitative (e.g., high, medium, low) or quantitative (costs) terms.
Assets are defined as "the target of threats" and are categorized as "information or technology." Information assets can include intellectual property and personal information. Technology can assets include systems and operational technologies.
The guide also delves into the differences between qualitative and quantitative methodologies in estimating cybersecurity risk.
Qualitative methods classify risk impacts and probabilities as "high", "medium" or "low" relative to one another. These can be used to create a simple risk register, or grid of various risks plotted out on a two-dimensional chart where one axis represents probability and the other impact, along with contingency plans and responsibilities for mitigation.
Risk registers can be tailored for management consumption. The CSC guide recommends having two risk registers — a simple, abridged one for management and other stakeholders who are not technically inclined, and a fully detailed one for the team conducting the risk assessment and implementing mitigations. CISOs should serve as the "translators" explaining technical terms to management.
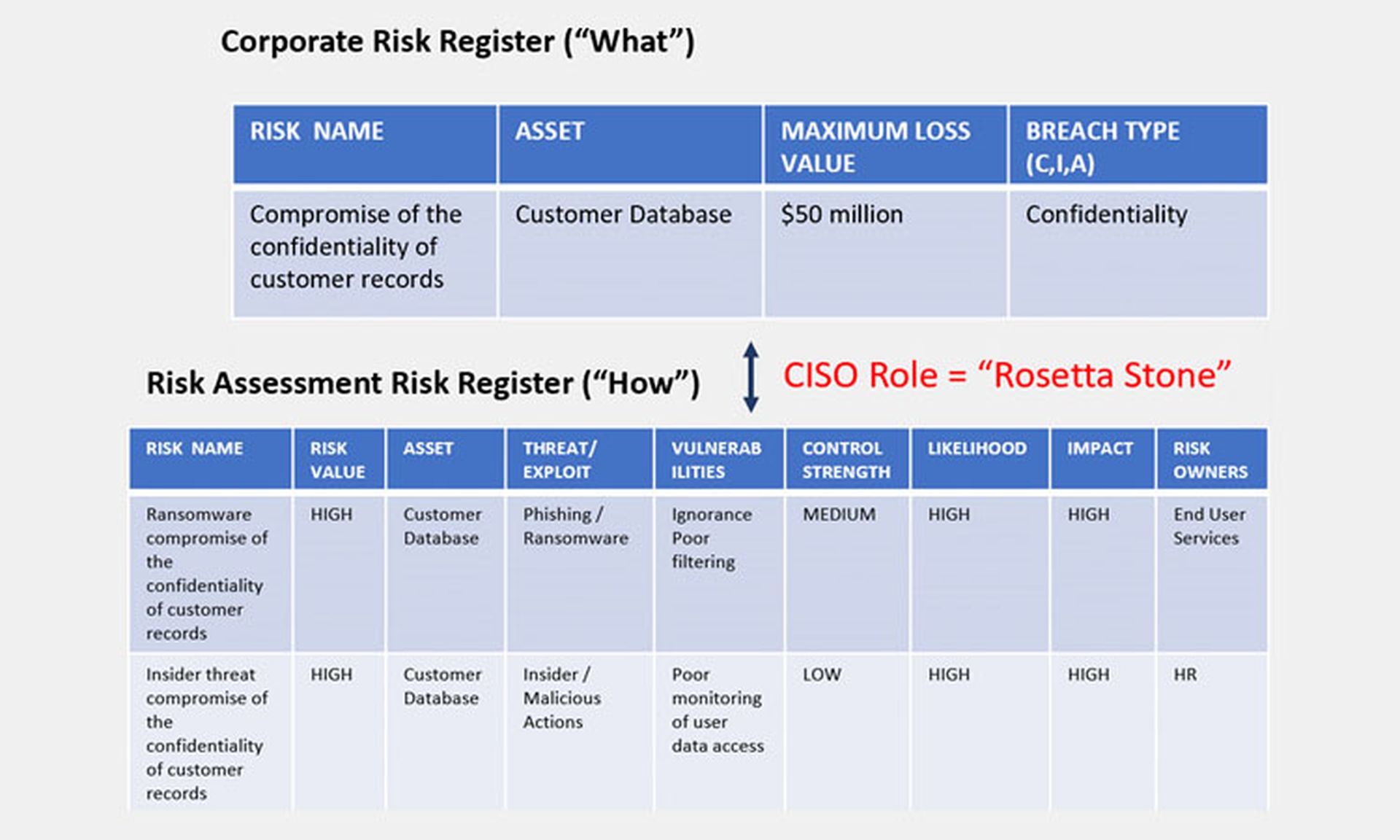
Credit: Cybersecurity Collaborative
In general, the guide notes, "security risk is hard to describe and communicate to non-security professionals. ... [R]isk definitions may need to be abridged for management consumption but will still need to include all the components in a risk assessment."
Quantitative methods, such as those based on the FAIR (Factor Analysis of Information Risk) framework, place a fixed cost on the impact of cybersecurity risk. This is more difficult to achieve than a qualitative estimate because it requires research into a business's earnings, exposure, and expenses. The guide also notes that quantitative estimates may be easier to explain to the C-suite.
"Because they represent loss scenarios in financial terms, quantitative methodologies have the advantage of facilitating risk assessment and treatment decisions," the guide states, "management more readily understands risks in terms of potential loss than as a representation of risk points."
The guide recommends that an organization only begin to use a quantitative method after having had success with the qualitative method.
The CSC Risk Assessment Maturity Model
The introduction to the CSC Risk Assessment Maturity Model presents us with a stunning visual: a three-tiered pyramid composed of nine components ranging from "Management acceptance" at the bottom to "Risk mitigation activities" at the apex. See below:
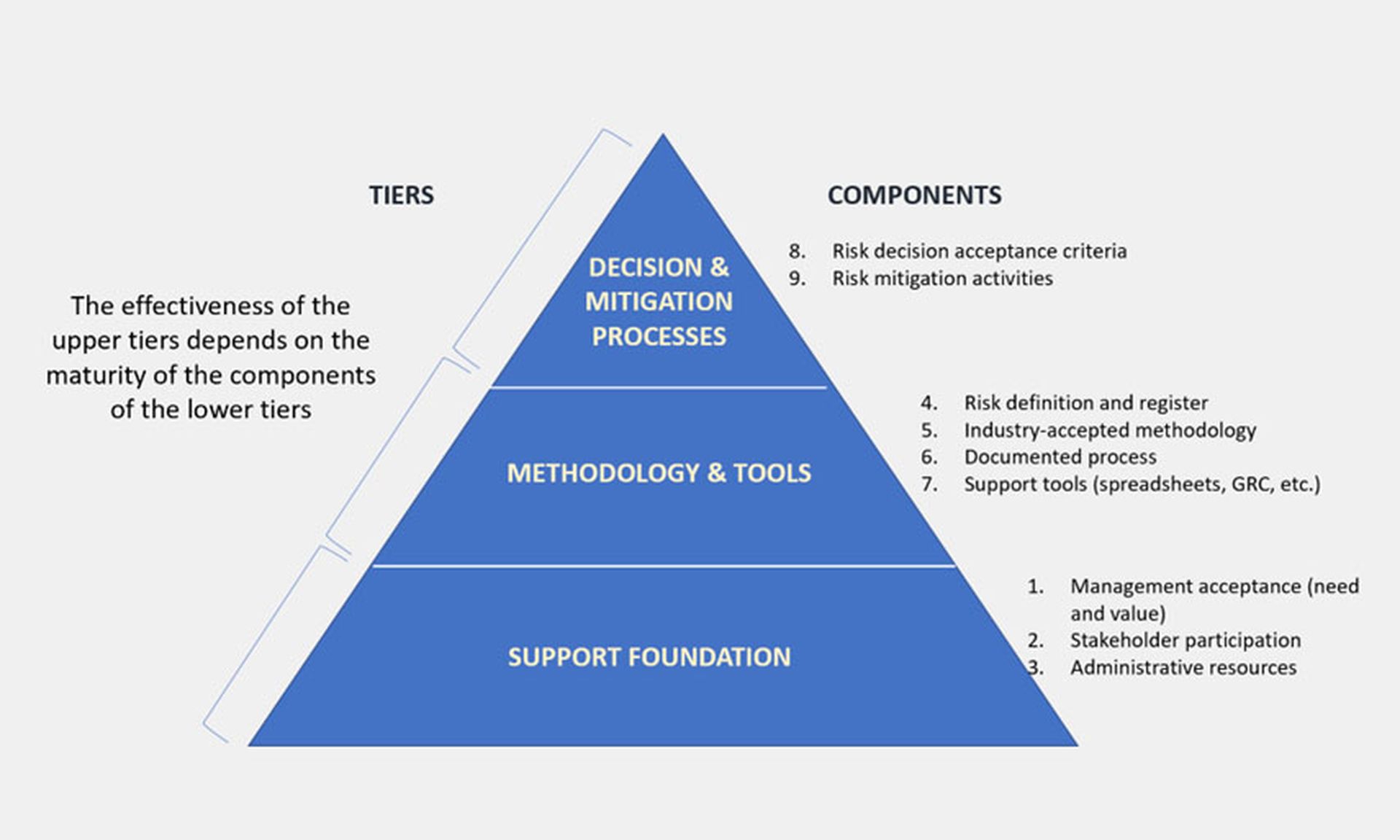
Credit: Cybersecurity Collaborative
The guide helps characterize implementation of each component into categories of "Not in place," "Basic," "Advanced" and "Exceptional." It also provides guidance for each component on how to get from one level to the next, such as from "Basic" to "Advanced," as well as a general overview of each aspect.
For example, the component "Administrative Resources" is described optimally as "Individual(s) have been assigned by the CISO to administer risk assessment processes and funding has been provided for tools and systems to support the risk assessment methodology."
Of course, different organizations will be at different stages of their progress toward realizing this goal. Hence the different maturity characteristics, which the CSC guide lists as:
- Not in place: "No administrative human or budgetary resources."
- Basic/good: "Risk assessment administrator assigned as partial duty."
- Advanced/better: "Risk assessment administrator assigned full time with funding."
- Exceptional/best: "Risk assessment function within CISO org. with leader and defined budget."
The guide also provides guidance on moving along from one stage to the next regarding administrative resources:
- Not in place to Basic: "Assign risk assessment administration responsibility to an existing staff member (e.g., GRC area under CISO)."
- Basic to Advanced: "Make the risk assessment administrator a full-time position supported by funding for tools and systems."
- Advanced to Exceptional: "Create a risk assessment function with support staff and a defined budget."
Additional features
The Cybersecurity Collaborative risk-assessment best-practices guide also provides links to other resources created by the CSC, including an explanation of risk assessments, an analysis and guide to implementation of the ISO 27001:2022 standard, and a workbook of risk-assessment-spreadsheet templates.
It concludes with a brief section of frequently asked risk-assessment questions, answered by CSC members, as well as an appendix of external resources and another appendix of tips for defining risk components and calculating risk scores.
Once again, to read the entire Cybersecurity Collaborative risk-assessment best-practices guide, log into your CSC member account or apply to become a CSC member at https://www.cyberleadersunite.com/contact-us.



