In 2022, security practitioners struggled to address the growing attack surface created by their rapid push to remote work and cloud-based operations during the previous two years. Cyber criminals exploited new vulnerabilities – including those introduced by the growing use of third-party software – to launch ransomware and other attacks.
But with tools like zero trust, XDR and more automated threat intelligence tech to bolster vulnerability management, cloud, email and endpoint security, organizations fought back – and established plans to invest more to secure networks and data in the next two years.
Click here to download the full 2022 Cybersecurity Year in Review Report from SC Media.
The following is the sixth of a seven-part series about where security practitioners struggled and, in many cases, made headway throughout 2022. Here, we focus on their efforts to bolster defenses with new threat intelligence tools.
Threat intelligence used to educate execs
Amid the heightened fear of ransomware in 2022, threat intelligence emerged as a core requirement of doing business in a world gone mad.
A sizable amount of interest in the historically tech-centric discipline was fueled in part by fear of cyberattacks tied to the war between Russia and Ukraine. In one example, the Ukrainian government warned the world that the Russian military was planning for multi-pronged attacks targeting the energy sector. Other nation-state cyberattack operations also contributed to the demand, including one June 2022 incident were Iran’s Cobalt Mirage exploited PowerShell vulnerabilities to launch ransomware attacks.
And of course, headlines of data breaches tied to vulnerabilities that organizations did not even know existed within their networks caught the attention not just of security teams, but the C-Suite and corporate board. A misconfigured Microsoft server, for example, wound up exposing years of sensitive data for tens of thousands of its customers, including personally identifiable information, user data, product and project details and intellectual property.
Indeed, according to 183 security pros surveyed by CyberRisk Alliance Business Intelligence in June 2022, threat intelligence has become critical in arming their security operations centers (SOCs) and incident response teams with operational data to help them make timely, informed decisions to prevent system downtime, thwart the theft of confidential data, and protect intellectual property.
Threat intelligence has emerged as a useful tool for educating executives. Many also credited threat intelligence for helping them protect their company and customer data — and potentially saving their organization's reputation.
“Without threat intelligence you would be chasing ghosts,” said one CRA survey respondent.
Respondents reported their top use cases for threat intelligence are vulnerability management (68%), security operations (66%), and incident response (62%). Technical (73%) and operational (71%) threat intelligence are more common than the more difficult strategic or more basic tactical use cases. Only 5% said they did not use any threat intelligence.
Many respondents pointed out that having access to early and credible intelligence is a core requirement for their organization. About six in 10 participants said they had subscribed to up to 10 threat intelligence feeds while another quarter gathered their intelligence from 11 to 50 feeds. The largest shares of respondents were using threat data from malware analyses or indicators of compromise (IOC).
Challenges of threat intelligence
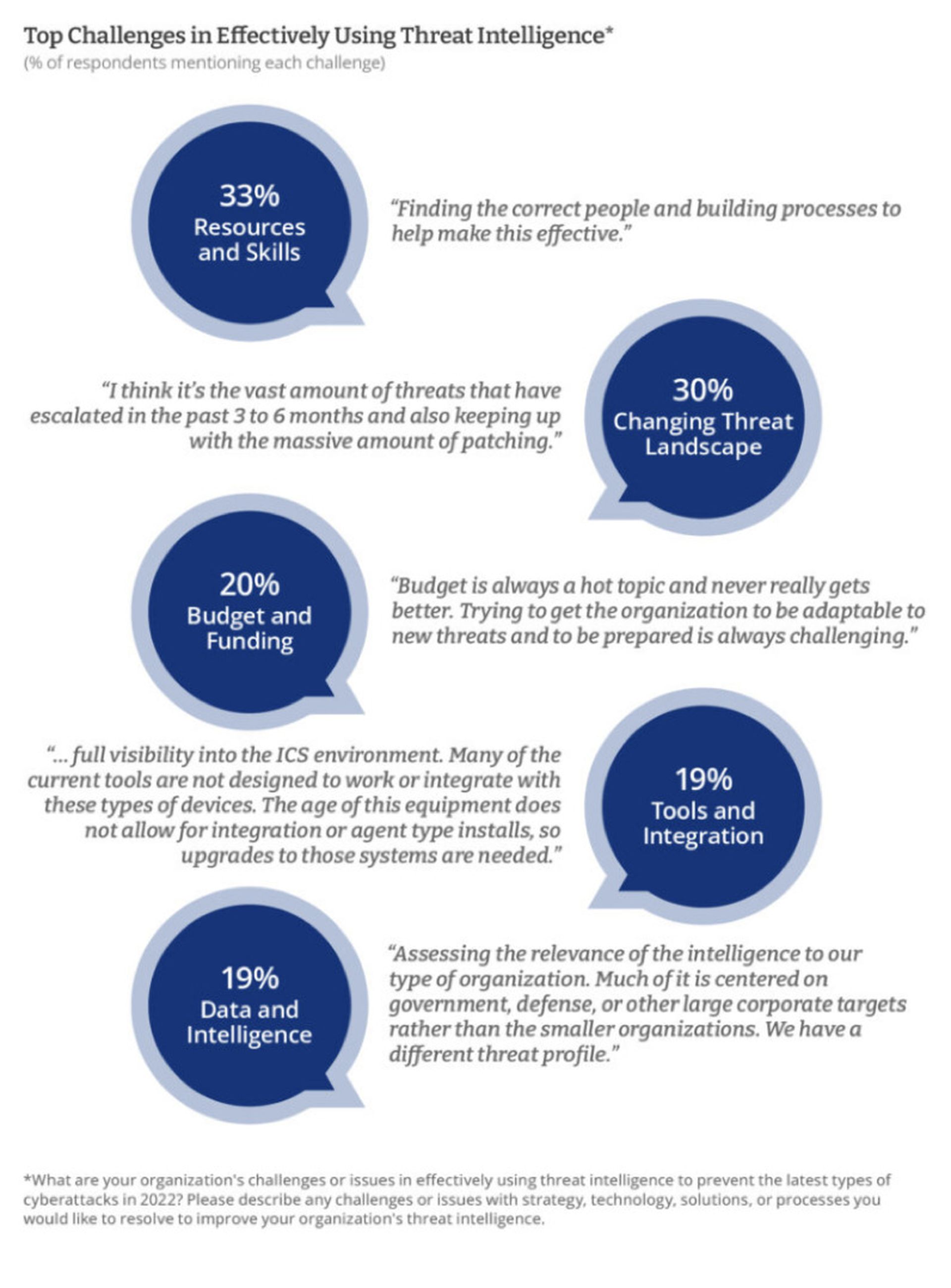
Effective implementation of threat intelligence isn’t without its challenges. Companies face everything from internal obstacles and competing priorities, such as limited resources and lack of skills/qualified staff, and budgeting/financial constraints to issues related to dealing with the evolving threat landscape and expanding attack surface.
Unfortunately, the ability to implement automated security responses to threats, enabling detection and remediation of the latest types of attacks, remains out of reach for many. Some claim actionable intelligence is hard to find, while others grapple with threat data overload and collating and assembling critical attack data, along with controlling excessive alerts and false positives.
Click here to download the CRA Business Intelligence December threat intelligence report.
Finding the most efficient solution that enables rapid deployment and the greatest ROI was also considered problematic, as well as intelligence integration and deployment of advanced technologies, such as machine learning models that optimize the use of historical data to predict future events.
Threat intelligence investments planned
Given the need for more threat intelligence, survey respondents were planning to Increase their investments, with 66% expecting their organizations to invest more in the coming year. Automation and threat modeling are especially sought after by security teams, based on planned investments.
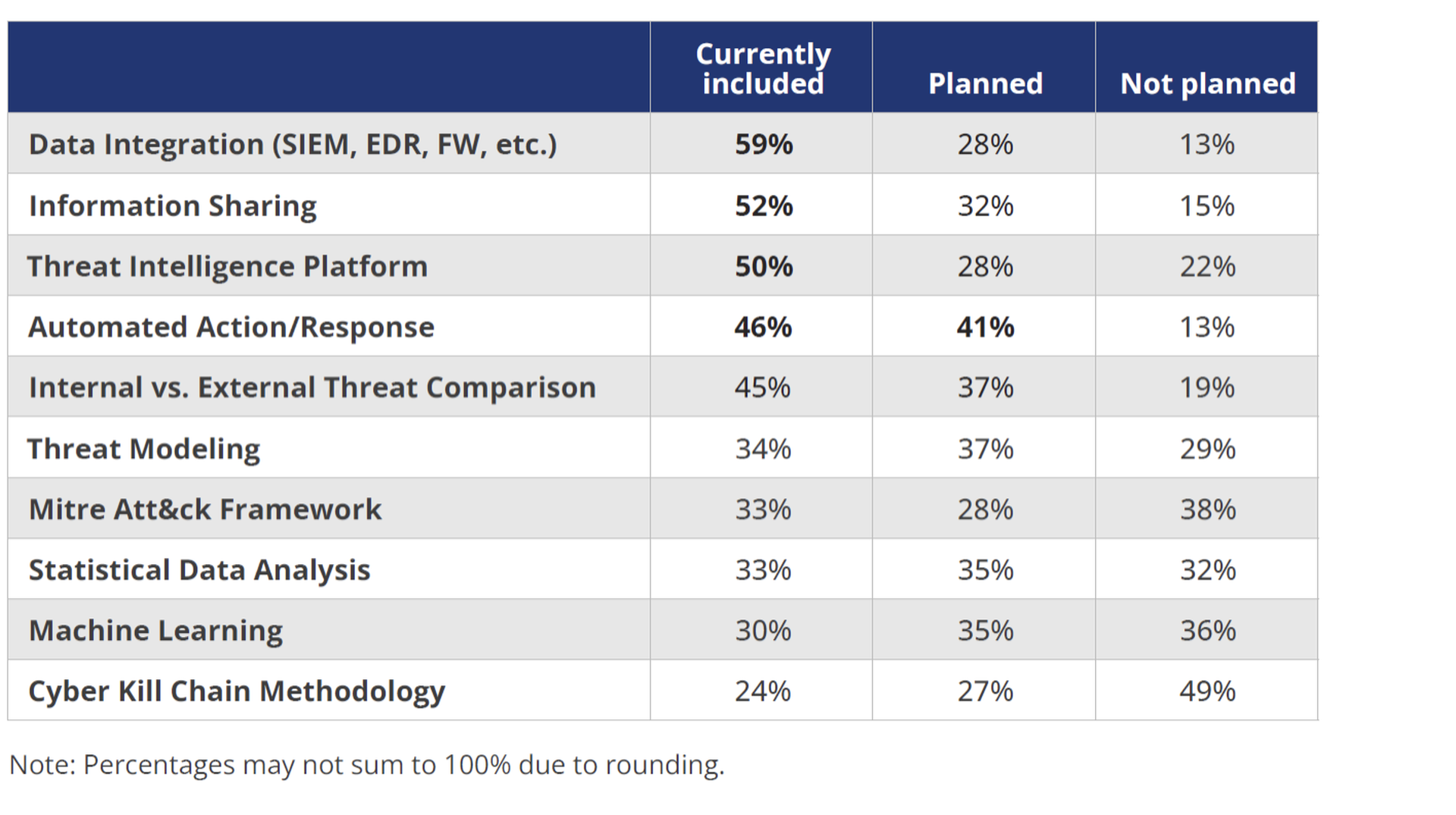
This specific trend bodes well for security operations centers hoping to boost defense capabilities through improved threat intelligence, particularly as it relates to patching security flaws in current software and responding more quickly to security events.
One respondent said her own organization’s plans to spend more on threat intelligence was critical to understanding exactly how systems are being attacked and building a plan to detect and respond.
As she put it: “Knowledge is everything.”



