
Ride-share company Uber confirmed it was hacked in what appears to be a damaging compromise that includes both internal systems and the company’s accounts for multiple third-party services.
Last night, the New York Times reported that Uber was investigating a compromise of its internal systems and had to take a number of its communications and engineering systems offline while employees were warned not to use Slack after the hacker was able to gain access to an employee’s work account and began posting messages advertising the hack.
Two hours later, the company confirmed the incident in a Twitter post, while screenshots of internal Uber systems were shared online by security researchers, some of whom claimed to have been in contact with the hacker.
“We are currently responding to a cybersecurity incident. We are in touch with law enforcement and will post additional updates here as they become available,” Uber’s communications team wrote.
Later in the day, Uber posted an update claiming that there is currently no evidence that sensitive user data like trip histories were accessed, that internal communication and service tools are coming back online and that services like Uber, UberEats, Uber Freight and Uber Driver are all operational. Cybersecurity experts routinely warn that it is very difficult to assess the full scope of a breach in the immediate aftermath.
The actor also posted screenshots that indicate they have access to Uber’s administrative account on third-party services like HackerOne, a bug bounty platform, as well as their AWS cloud server.
“We’re in close contact with Uber’s security team, have locked their data down, and will continue to assist with their investigation,” said Chris Evans, CISO for HackerOne.
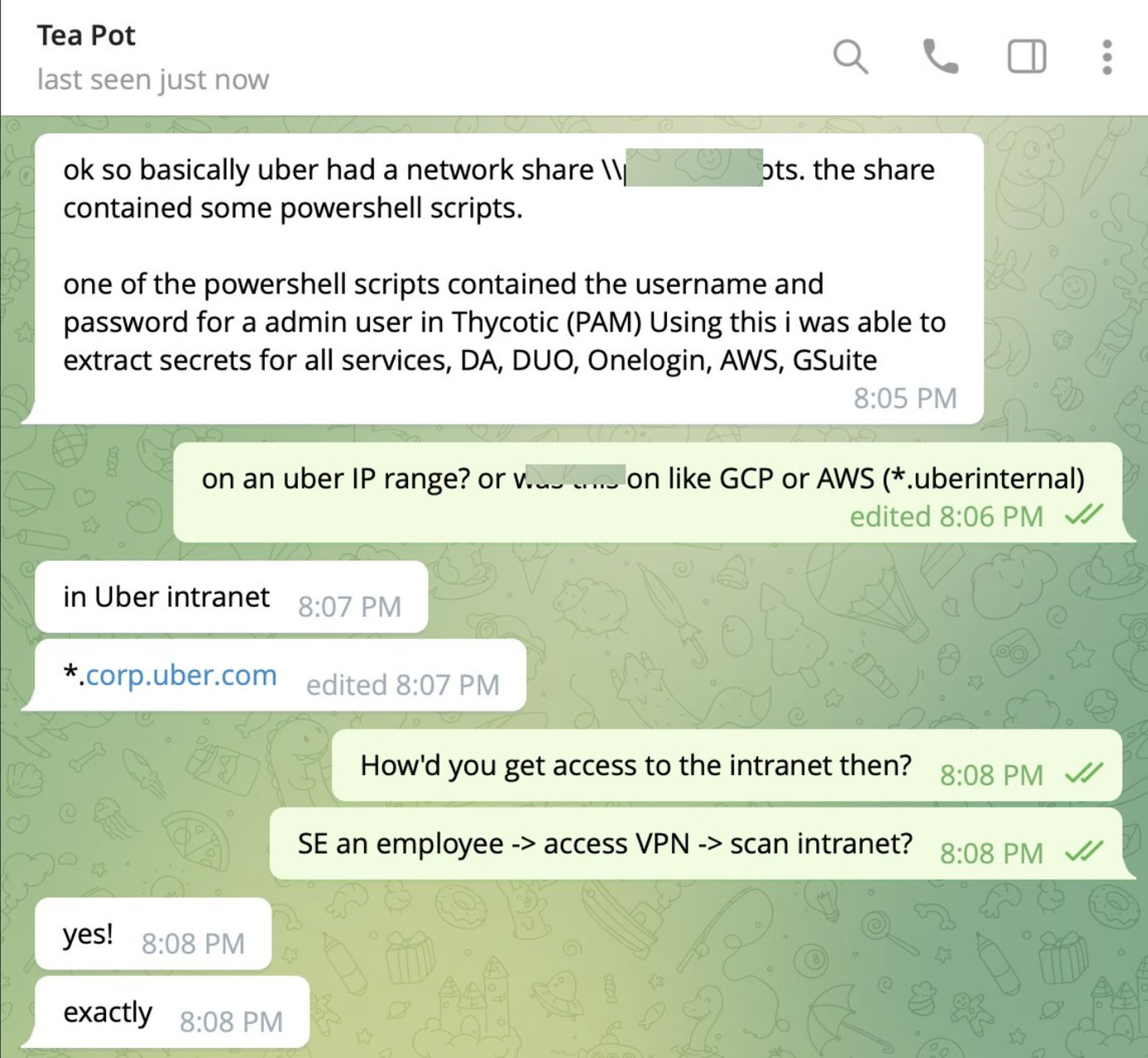
Corben Leo, a security researcher and chief marketing officer at Zellic, told SC Media that he learned directly from the hacker that the individual phished an Uber employee to gain access to Uber’s corporate VPN. From there, they were able to scan Uber’s internal corporate network, where they found administrative user credentials for Uber’s Thycotic account, a privileged access management system, through a shared network resource.
“Using this they were able to access Uber's AWS environment, GSuite, Duo (can thus bypass 2FA for anything), OneLogin, get Domain Admin, etc.,” Corben said through a Twitter direct message.
Leo told SC Media that beyond that conversation, he has not been in further contact with the hacker.
If those reports turn out to be accurate, it will mark yet another instance where access to a single account resulted in the compromise of a multi-billion dollar company. Companies like Twitter, Microsoft and Okta have all been hacked in a similar fashion. Further, the widespread, ubiquitous access that many employees have to internal systems was one of the chief concerns highlighted by Peiter Zatko, former CISO for Twitter, in his whistleblower complaint against the company earlier this year.
While details about the hack are still coming to light, it appears that “a single hard coded password has been used to access [Uber’s] privileged access management system, giving access to any area of the IT environment that links to it,” said Chris Vaughan, area vice president at Tanium.



