As security teams grapple with ways to better protect their company endpoints, Extended Detection and Response (XDR) is increasingly cited as the technology necessary to make it happen. But for many practitioners, the details around XDR are new.
For a security decision maker trying to make sense of where to begin – from evaluating XDR offerings to moving toward deployment – the first step is to understand the components.
To that end, here is an excerpt from a recently released Sophos beginner’s guide:
What is XDR?
There are three interpretations of XDR:
- Extended Detection and Response: “Extended” refers to going beyond the endpoint and server, bringing in additional data sources such as firewall, email, cloud, mobile and others.
- Cross-product Detection and Response: This refers to data being combined from multiple products and security layers.
- The third interpretation uses the ‘X’ in XDR as a mathematical variable that stands in for whichever data sources are being leveraged as part of the solution.
Whichever definition you use for XDR, all reference and make use of the same core components to access and query a range of data sources to give your organization greater visibility and context.
What it does
XDR is designed to give organizations a holistic view of their cybersecurity posture and IT environment with the ability to quickly pivot to deep investigation when necessary.
A commonly asked question is how XDR differs from EDR. XDR solutions should include the business-critical question answering capabilities of EDR (Endpoint Detection and Response). That is, being able to get live data directly from an endpoint or server, as well as access to cloud data if a device is offline.
XDR builds upon that solid foundation by adding even more data and context that both increases visibility and gives the user even more insight during an investigation.
This results in faster and more accurate incident detection and response.
One of the most valuable ways to use XDR is to begin with the ‘macro’ spotlight that gives you the tools to quickly scan across your entire environment and highlight suspicious activity, anomalous behavior and other IT issues.
When an issue is identified you can then hone-in on a device of interest, pulling live data or remotely accessing the device to dig deeper and take remedial action.
Extended data sources
As powerful as EDR tools are they are limited to detection and response on endpoints and servers.
This isn’t necessarily a bad thing. If you had to choose one place to focus your detection and response efforts your organization’s endpoints and servers are a great choice.
However, there are things you can’t do by working on them in isolation. After all, your IT environment is an interconnected web of networks, communication tools, mobile devices, cloud applications and more.
To defend your IT infrastructure more comprehensively an integrated detection and response system is key.
This is where XDR comes in.
XDR takes the idea of EDR and extends it. It goes beyond the endpoint and server, incorporating data from other security tools such as firewalls, email gateways, public cloud tools and mobile threat management solutions.
XDR is an emerging technology, so data sources and functionality varies between vendors.
This diagram gives a good starting point to understand what XDR adds onto EDR:
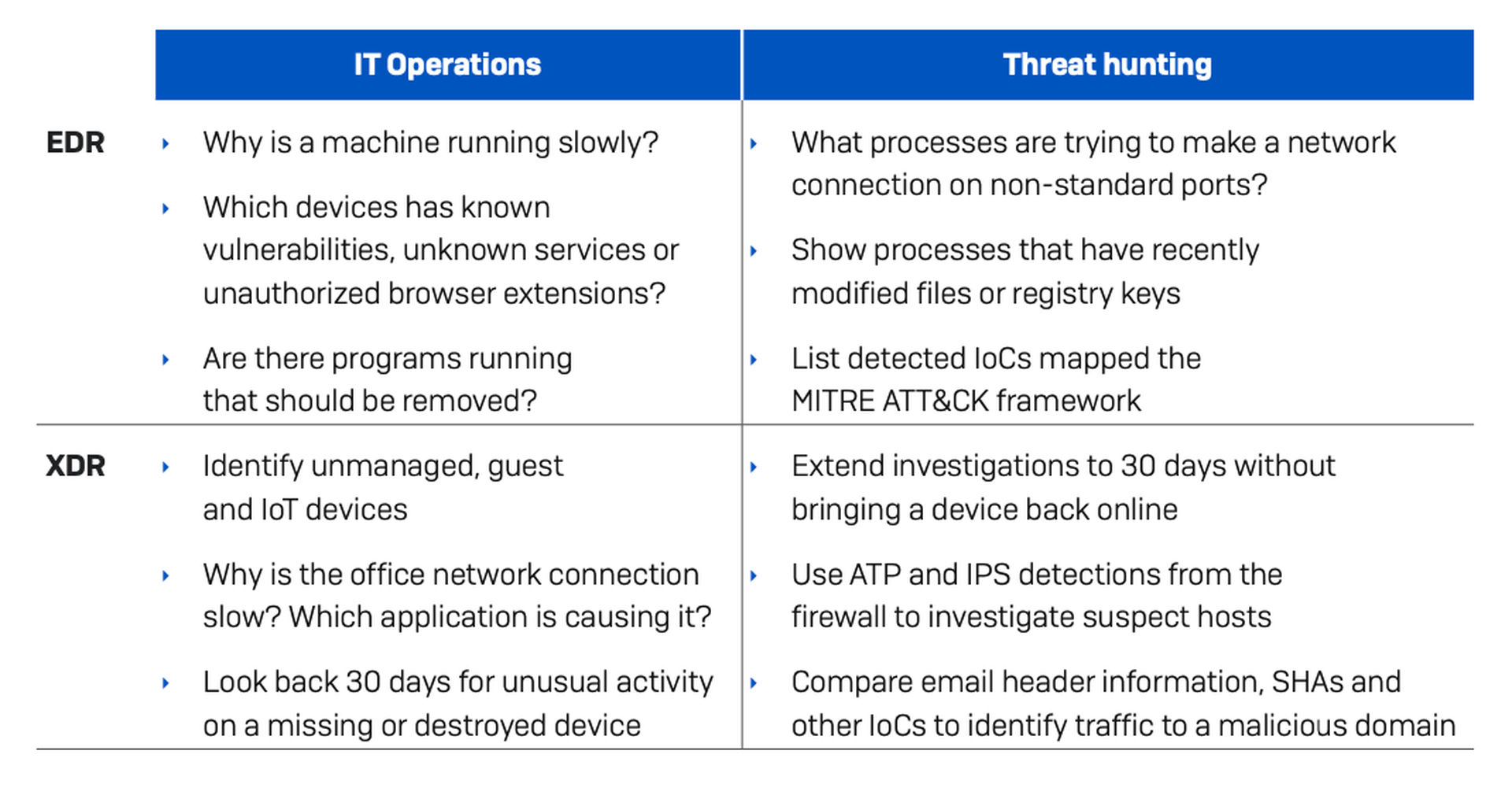
XDR use cases
The best way to explain the real-world benefits of XDR is to look at how the functionality can help organizations in their day to day IT operations and threat hunting capabilities. Note that we have included EDR examples as your XDR solution should also cover those use cases.

How Sophos can help
Sophos XDR gives organizations a broad, holistic view of their entire cybersecurity environment with the ability to deep dive when required. In other words you get both the 10,000 feet, high level view and the granular detail as you need them.
XDR enabled solutions send endpoint, server, firewall, email and other data sources* to the Sophos Data Lake, a cloud repository for critical XDR and offline device data. It’s a centralized location for all the data so you can quickly answer business critical questions, correlate events from different data sources and take even more informed action.
Getting started is easy, with a library of pre-written, fully customizable queries so you can choose a category, add devices and start answering IT operations and threat hunting questions.