Progress Software, makers of the MOVEit file transfer application that has swept up hundreds of companies following the exploitation of multiple vulnerabilities in May and June, have disclosed three new vulnerabilities, including a SQL injection flaw they describe as critical and two other high severity bugs.
A CVE entry for the new SQL bug (CVE-2023-36934) was published on July 5, affecting MOVEit Transfer’s web application and allowing for unauthenticated access to the database by submitting a payload to an application endpoint, which allows the attacker to view or modify content.
The vulnerability was discovered by Guy Lederfein as part of Trend Micro’s Zero Day Initiative, and affects versions of MOVEit Transfer before 2020.1.11 (12.1.11), 2021.0.9 (13.0.9), 2021.1.7 (13.1.7), 2022.0.7 (14.0.7), 2022.1.8 (14.1.8), and 2023.0.4 (15.0.4).
Two other vulnerabilities were disclosed as part of a package of software updates released by Progress Software last night, both described as high severity.
One (CVE-2023-36932) outlines “multiple” SQL vulnerabilities that can also allow for disclosure and modification of database content, affecting versions of MOVEit Transfer before 2020.1.11 (12.1.11), 2021.0.9 (13.0.9), 2021.1.7 (13.1.7), 2022.0.7 (14.0.7), 2022.1.8 (14.1.8), 2023.0.4 (15.0.4). The company credits HackerOne bug hunters cchav3z, nicolas_zilio and hoangha2, hoangnx, and duongdpt with VCSLAB of Viettel Cyber Security for discovering the vulnerabilitt.
The third (CVE-2023-36933) would let an attacker to terminate instances of MOVEit Transfer, and affects versions before 2021.0.9 (13.0.9), 2021.1.7 (13.1.7), 2022.0.7 (14.0.7), 2022.1.8 (14.1.8), and 2023.0.4 (15.0.4). It was discovered by HackerOne and user jameshorseman.
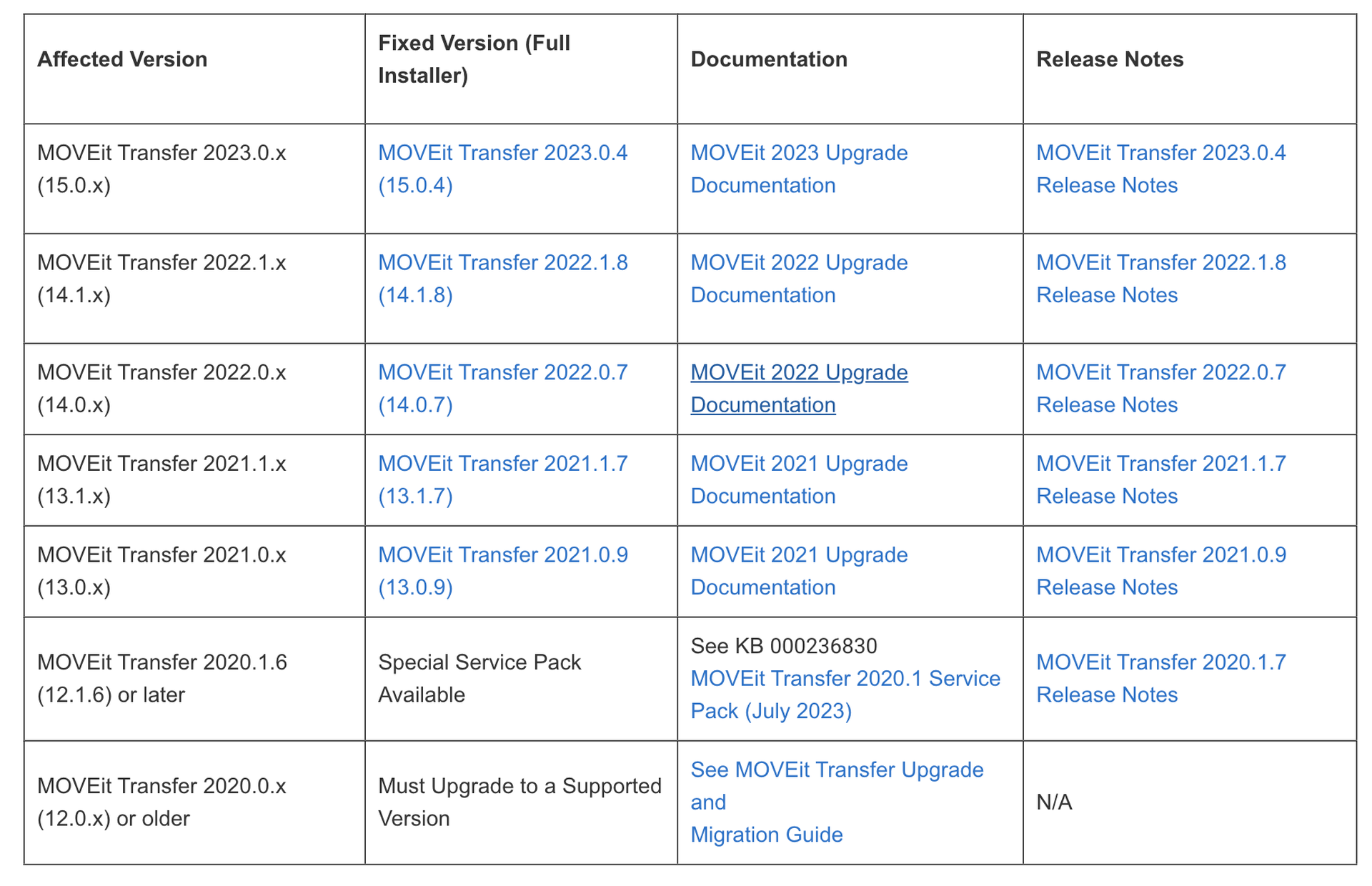
A list of affected versions of MOVEit Transfer (Source: Progress Software)
“Progress Software highly recommends you apply this Service Pack for product updates and security improvements,” the company security bulletin stated.
The newly reported flaws come on the heels of multiple disclosed SQL injection vulnerabilities reported in MOVEit Transfer and MOVEit Cloud in May and June, at least one of which was exploited by the Cl0p extortion group, resulting in dozens of companies disclosing that their data was stolen in the attack. Cl0p has listed nearly 200 companies thus far on its dark web leak page, and experts expect more victims to be discovered in the coming weeks and months.
According to a post on Progress Software’s community board, users who have already applied previous patches issued and May can simply run the latest update package, while those who haven’t will need to install the earlier patches first before the July 5 update will work.




