(A preview for the soon-to-be released SC Media eBook “Endpoint security: Critical in the fight against ransomware.”)
Ransomware attacks cost organizations far more than just the ransom payment alone. There’s the high cost of recovery and remediation to consider, the loss of revenue resulting from paused operations, as well as damages to reputation and trust that negatively affect companies’ bottom line for years to come.
These costs would be debilitating enough for large companies with the resources to fight back, but new data by cybersecurity vendor Sophos shows that small and medium-sized businesses are no more immune to ransomware.
Between January and March 2023, Sophos commissioned an independent survey of 3,000 IT cybersecurity leaders in organizations across 14 countries in the Americas, EMEA, and Asia Pacific. The output of that survey, the 2023 State of Ransomware report, reveals the business and operational impact the ransomware threat is having on security teams around the world. It includes the top root causes for ransomware as well as how organizational revenue might factor into an organization’s decision of paying or not paying a ransom.
Key findings
Here are a few of the top takeaways from the study and their implications.
- Ransomware attack rates remained level with 2022’s record-high output.
2022 saw companies hit hard by ransomware, with 66% of respondents testifying to one or more attacks on their business that year — 15 percentage points higher than 2021, and 29 percentage points higher than 2020. That number remained the same in 2023, demonstrating adversary resilience despite recent crackdowns by law enforcement and global intelligence agencies. The maturation of ransomware-as-a-service has lowered the barrier for entry to would-be ransomware actors, fueling an organized industry of specialized players capable of consistently executing attacks at scale.
- Attackers target the big fish, knowing they can demand more.
The more revenue a company brought in, the more likely it was to incur a ransomware attack. 56% of organizations with revenue of $10-$50 million experienced a ransomware attack compared to 72% of victims with annual revenue of $5 billion or more. This is by design, of course, as those in the upper brackets of earnings are considerably more likely to bite the bullet and pay the ransom than those in the bottom tier. Among organizations with less than $10 million in revenue, 36% paid the ransom at an average payout of $690,996. Meanwhile, the heaviest earners ($5 billion plus) paid out 55% of the time, at an average payout of $2,464,339. Attackers know that higher ransoms may be cost-prohibitive to smaller earners, and it looks like they’re adjusting their tactics to focus primarily on the biggest fish in the pond.
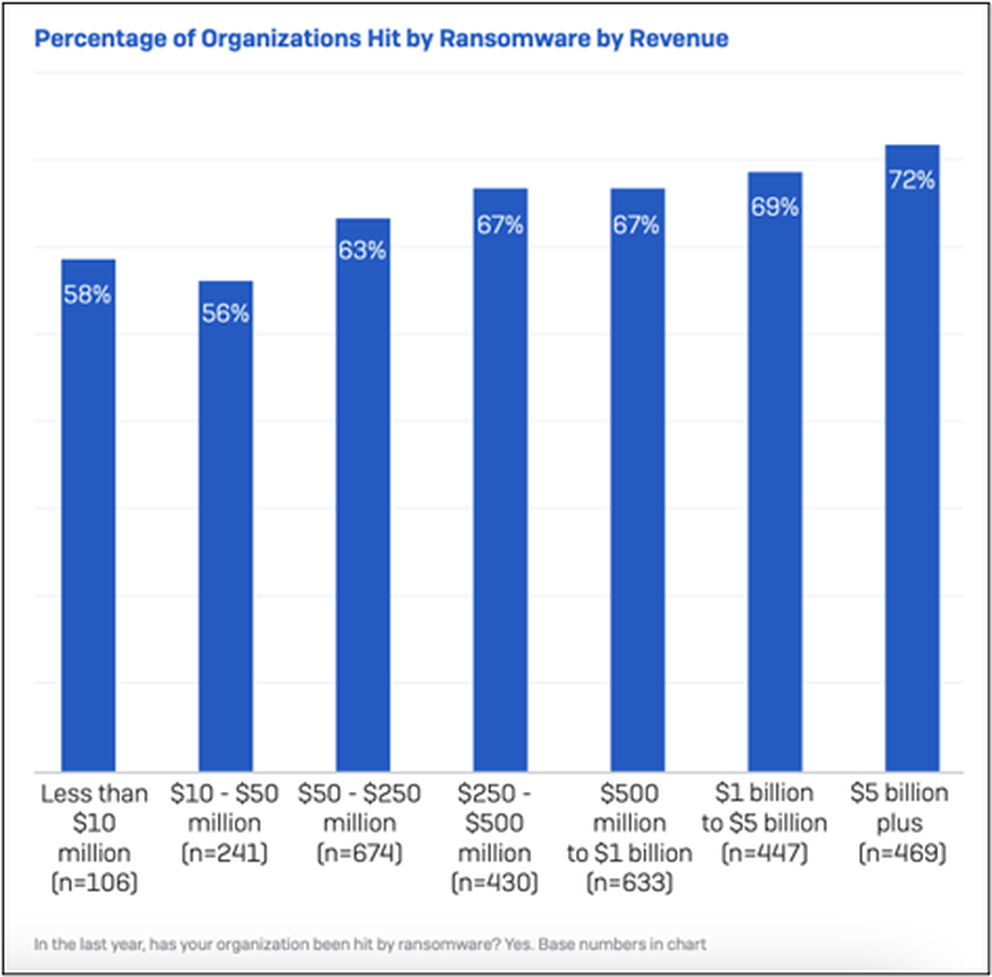
Source: The State of Ransomware 2023 (Sophos)
- Unpatched endpoints are low-hanging fruit for bad guys.
Vulnerable endpoints continue to give security teams heartburn, as they represent the most common points of entry for attackers to gain a foothold in their victims’ networks. Among the 66% of organizations who suffered one or more ransomware attacks in the last year, 36% of those attacks were carried out via exploited vulnerabilities found in devices – the leading root cause for the second year running, followed by compromised credentials (29%). Most of these attacks likely could have been prevented if organizations had practiced diligent patching. In over half of the investigations where an exploited vulnerability was the root cause, the ProxyShell or Log4Shell vulnerabilities were present in the affected assets (each of which should have been patched back in May 2021 and December 2021 when they became publicly available). “While your board of directors will wish to hear that the enterprise is aware of and addressing high-profile threats (like zero-day vulnerabilities), it’s the thankless monthly and quarterly grind of patching that truly makes the difference in your enterprise’s risk profile,” says John Shier, Senior Security Advisor for Sophos.
- It pays to use backups (literally).
Rarely did an organization hit by a ransomware attack emerge unscathed. The average cost of recovery (excluding the ransom itself) totaled $1.82 million in 2023 – $2.6 million if companies paid the ransom to restore data, versus $1.6 million if they used backups to restore data. Consider too that a quarter of the companies surveyed took anywhere between 1 and 6 months to fully recover. That being said, 45% of those who used physical backups of data were able to recover in a week, while just 39% who paid the ransom were able to recover in that same timespan. Notice that by backing up copies of data from endpoints and preserving them offline in another physical location, orgs were able to significantly curb the sting of ransomware. They still lost revenue, but far less than their peers who did not use backups. On top of that, they were able to recover within a week versus the months it took all others to get their bearings again. “Whether you pay ransom or don’t pay ransom, backups always accelerate the recovery process and the integrity of all of your systems and files,” says Chester Wisniewski, Field CTO of Applied Research at Sophos. Concerningly, overall use of backups declined this year, from 73% in 2022 to 70% in 2023.
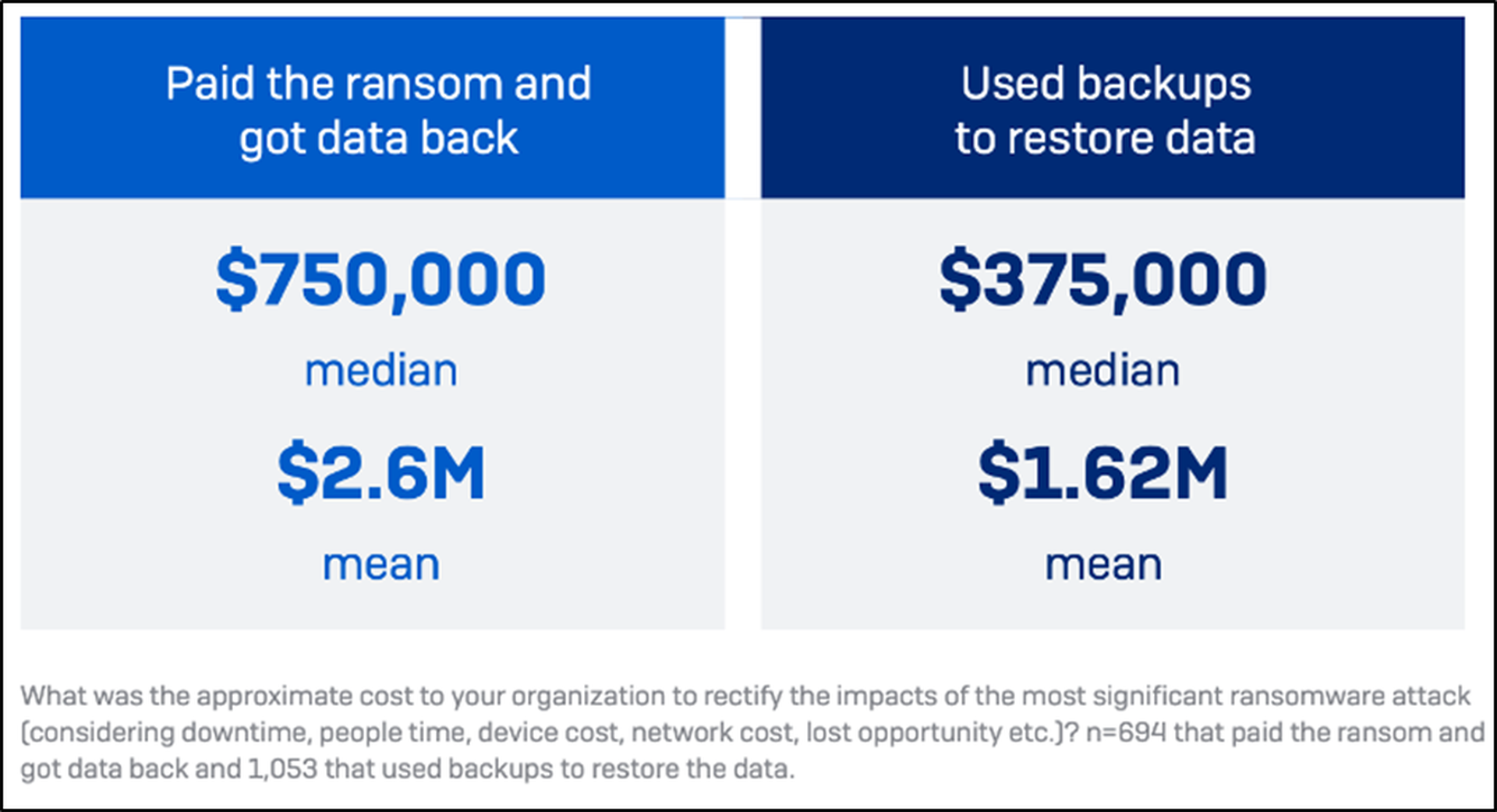
Source: The State of Ransomware 2023 (Sophos)
- Ransomware insurance correlates with higher rates of recovering encrypted data, but also higher rates of paying the ransom
Organizations with cyber insurance were considerably more likely to recover encrypted data than those without such policies. However, the type of cyber coverage made very little difference: 98% of those with a standalone policy and 97% of those with a wider insurance policy that covers cyber got data back. In comparison, 84% of those without a policy were able to get encrypted data back. According to Sophos, these numbers can likely be chalked up to the fact that cyber insurance generally requires organizations to keep backups and recovery plans as conditions of coverage, which would increase their chances of recovering data. Insurers are also able to guide ransomware victims through the recovery process in order to optimize outcomes. Furthermore, organizations with cyber insurance were more likely to pay the ransom to recover data than those without a policy.




