Until a recent update to the BlackMatter ransomware platform fixed a coding bug, cybersecurity firm Emsisoft was able to help a wide number of victims recover data without paying.
"With the help of law enforcement agencies, CERTs and private sector partners in multiple countries, we were able to reach numerous victims, helping them avoid tens of millions of dollars in demands," Fabian Wosar, Emsisoft chief technology officer, wrote in a blog on Sunday.
Emsisoft had been doing the recoveries without publically announcing the vulnerability they had exploited as not to alert the ransomware gang to the costly error. Emsisoft came forward after BlackMatter caught their mistake and patched it.
BlackMatter is the continuation of the Dark Side malware famously used in the Colonial Pipeline attack. Dark Side changed names due to the global law enforcement attention brought by the attack, pulling up stakes quickly enough to leave the affiliates who licensed use of Dark Side ransomware in their criminal hacking campaigns in the lurch. While security experts are convinced BlackMatter is Dark Side, the affiliates have been willing to see the groups as distinct enough not to fear similar abandonment.
The connection between the groups led Emsisoft to discover the vulnerability it would use to recover files for victims. Dark Side patched a vulnerability in January that Emsisoft was using to recover files. As BlackMatter, which launched over the summer, tinkered with the platform, it accidentally reopened that vulnerability.
But all good things come to an end. According to Emsisoft's blog, BlackMatter recently hardened its platform after the group's detractors started to exploit a glitch in the communications system that allowed anyone to enter negotiations and communicate as the victim. Though it was not mentioned by name, this appears to be a reference to the New Cooperative ransomware negotiations, where someone — allegedly not the victim — posted a timeless response to an accusation the Cooperative had violated ransomware rules by contacting the police.
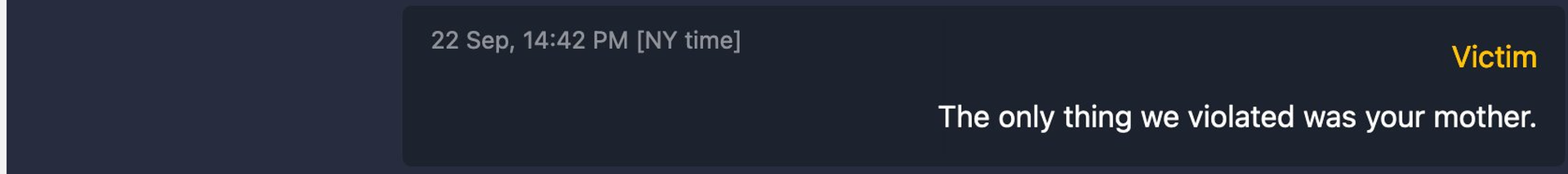
Hardening the platform removed the vulnerability Emsisoft discovered, according to the blog, and the company felt that it could now come forward with what it had been able to do without interrupting its ability to do it.
Wosar said Emsisoft has similar unpublicized capabilities with other ransomware services.
"Beyond BlackMatter, our team has identified vulnerabilities in about a dozen active ransomware families. In these cases, we can recover the vast majority of victims’ encrypted data without a ransom payment," he said.




