In "Romeo and Juliet," playwright William Shakespeare once posed the existential question: “What’s in a name?” In cybersecurity, it turns out, the answer is: “Almost everything you hold dear.”
A new report released Tuesday by CrowdStrike finds that identity-based attacks have become a crucial component of most interactive cyberattacks today, providing malicious hackers with cheap and easy means to gain initial access into victim environments, facilitate widespread lateral movement and hide amidst the background noise of routine authentication work that happens hundreds or thousands of times a day at many organizations.
The report, authored by CrowdStrike’s newly formed counter adversary operations team, covers activity from July 1, 2022, to June 31, 2023, and includes data from “tens of thousands” of incidents.
CrowdStrike’s data lends weight to a number of trends over the past few years in cybersecurity, from the increased targeting of identity and authentication mechanisms and buggy software as a means of initial access to the expanded use of zero-day vulnerabilities and remote management tools to stealthily operate once inside a victim environment.
But the biggest takeaway this year is that, leveraging the digital identity of a user, organization or vendor has become a key feature of most of the malicious hacking performed today, present in 62% of all “hands on keyboard” intrusions observed over the last year.
“The consistent appearance of valid accounts across various tactics highlights the intensification of adversaries' strategic use of trusted accounts to gain initial access, establish persistence, elevate privileges and evade defenses,” the report stated. “The concerning ease with which adversaries can gain initial access — often simply through purchases — blurs the distinction between legitimate users and imposters.”
One method known as “Kerberoasting” — whereby attackers steal encrypted tickets used as unique identifiers by the Kerberos authentication protocol and crack them offline to obtain plaintext credentials — rose by a whopping 583% over the last year, according to CrowdStrike’s data.
The technology sector was the top industry vertical targeted by a comfortable margin — both by cybercriminals and the kind of targeted intrusions carried out by state actors — reflecting how the use of third-party software and tools to break into the systems of downstream customers is becoming increasingly mainstream.
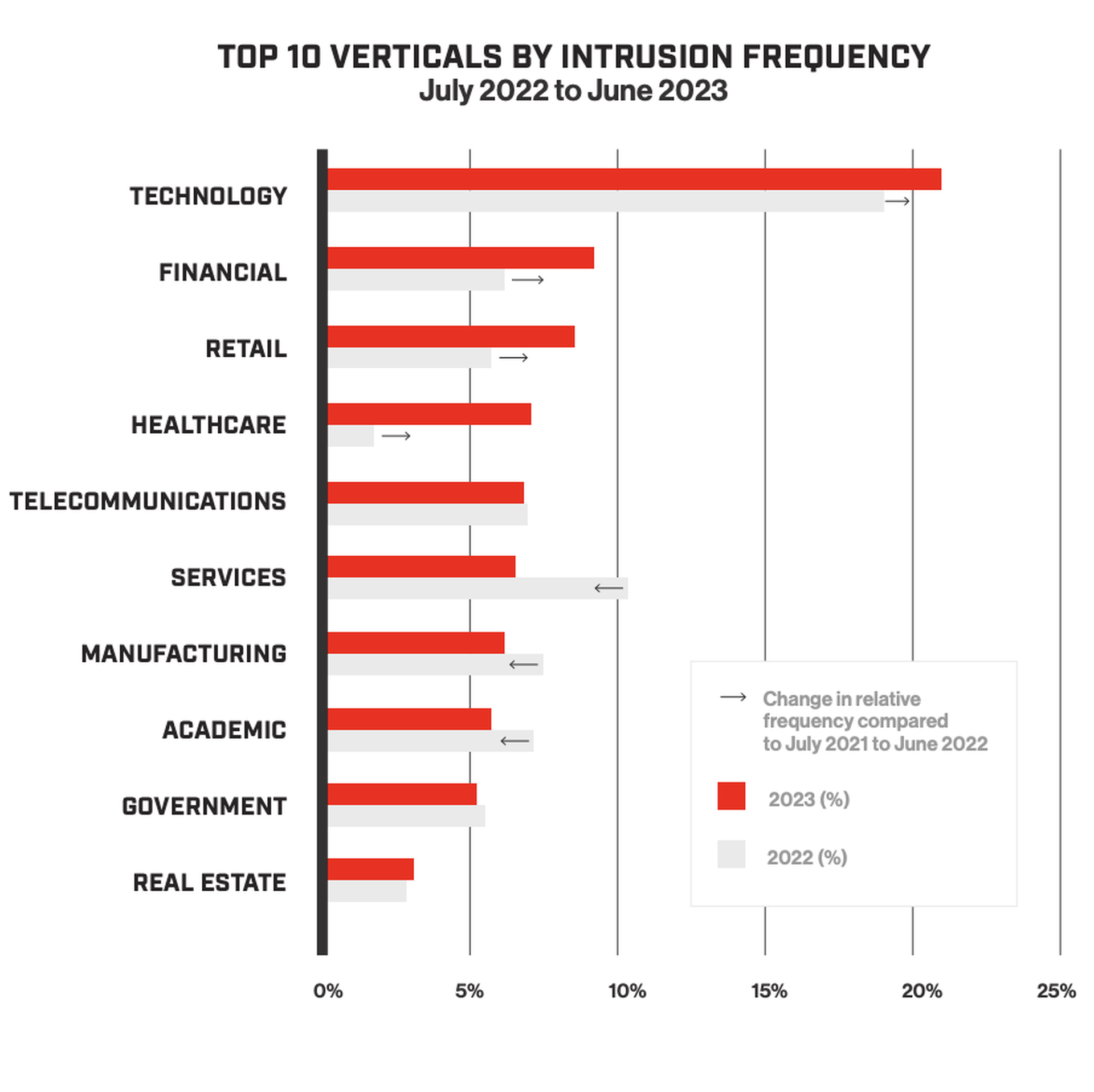
After the technology industry, the financial sector was the next most targeted vertical, led by North Korean hacking outfits on the lookout for profits that could help fund the Hermit Kingdom’s military and nuclear weapons program. The sector was also pilloried by cryptocurrency thieves and big-game hunting ransomware groups.
“Due to the victim organization's need to maintain system uptime and the sensitive nature of the sector, eCrime threat actors likely conclude that financial institutions are willing and able to pay ransom demands,” the report stated.
Cloud + creds = a lethal duo
The increased reliance on identity-based attacks goes hand-in-hand with rising threats against cloud-based services and assets. Cloud exploitation nearly doubled in 2022, while the number of incidents attributed by CrowdStrike to “cloud conscious” threat actors has tripled.
As businesses have moved to the cloud and increasingly relied on a distributed, remote workforce, the credentials, encryption keys and authentication tokens they use to control access and validate identities have become a priority for attackers. The latest example of this danger can be found in a campaign disclosed by Microsoft last month, wherein Chinese hackers were able to obtain a signing key that allowed them to break into the email accounts of high-level U.S. government officials (and possibly more) ahead of talks between the two nations.
One unnamed victim accidentally published a list of cloud access key credentials on GitHub in November 22 and “within seconds, automated scanners and multiple threat actors attempted to use the compromised credentials.” Of the intrusions that involved the use of valid credentials, more than half were obtained from an external system not associated with the victim — either purchased online or stolen from another organization.
Cloud-based credentials offer an attacker the ability to conduct expansive lateral movement. Once they’re in, many hacking groups are now “keenly aware” of how to leverage an organization’s own cloud tooling and services against them.
“Cloud-conscious adversaries are navigating cloud environments with a level of skill and confidence that is, unfortunately, often not matched by organizations’ in-house security teams,” CrowdStrike noted.




